目录
2.2. hash 类型识别工具 hashidentifier
3.2. 输出格式(--outfile-format 参数)
一. 前言
hashcat 软件是一款非常强大的、开源的、号称世界上最快的密码破解软件,配合强大的字典,可以破译超过百分之九十的密码。hashcat 目前支持各类公开算法高达240+类,市面上公开的密码加密算法基本都支持,有 microsoft lm 哈希、md4、md5、sha 系列,unix 加密格式,mysql 和 cisco pix 等!是安全测试中经常用到的密码解密神器之一。
作为新手,可以使用 hashcat 工具 cpu 模式破解,电脑机型高端可以使用 gpu 破解。内存的大小也影响工具破解的成功率。
二. hashcat 安装
2.1. hashcat 官网下载
建议从官网下载最新版本的 hashcat 压缩包:https://hashcat.net/hashcat/
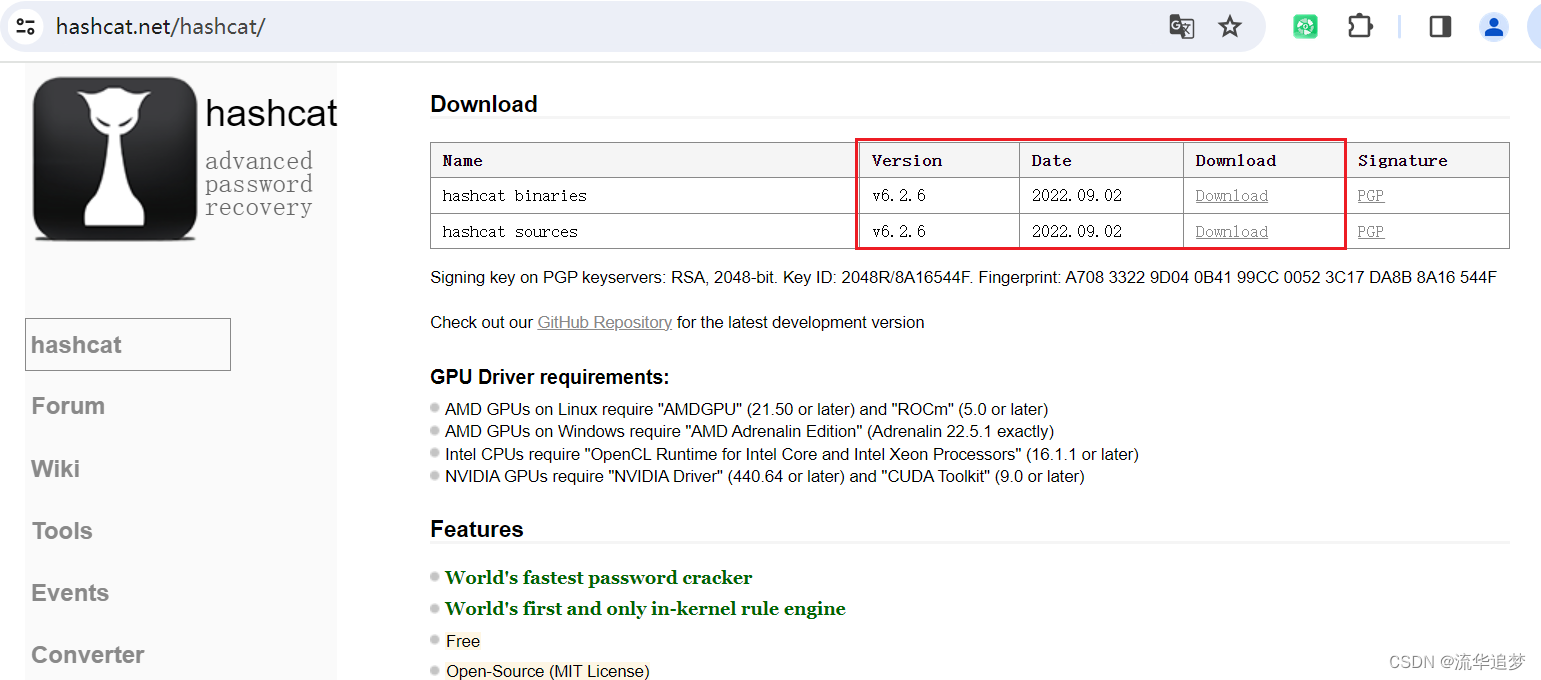
解压目录如下:

该目录下的文件:
- hashcat.exe:是64位操作系统上可以使用的可执行文件。
- hashcat.potfile:是 hashcat 破解后密文、译文默认存储文件,只要解密过的 hash 密文都会被记录,后续相同密文就不需要再破解,直接从该文件中通过 --show 参数获取。
- password.dict:是密码字典文件。
在该目录下 cmd 窗口中执行命令:hashcat -h
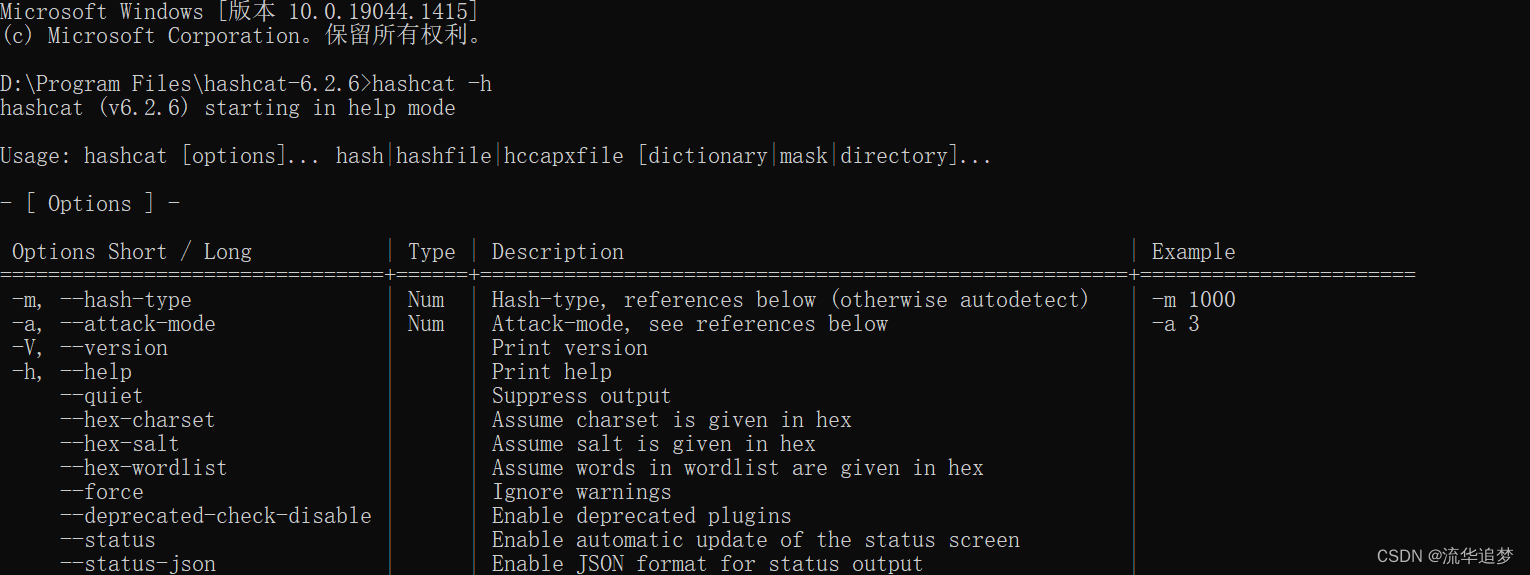
搞定,安装成功,为方便使用,可以配置该文件夹目录到系统环境变量 path 中,就可以在windows 任何目录下执行 hashcat 命令了。
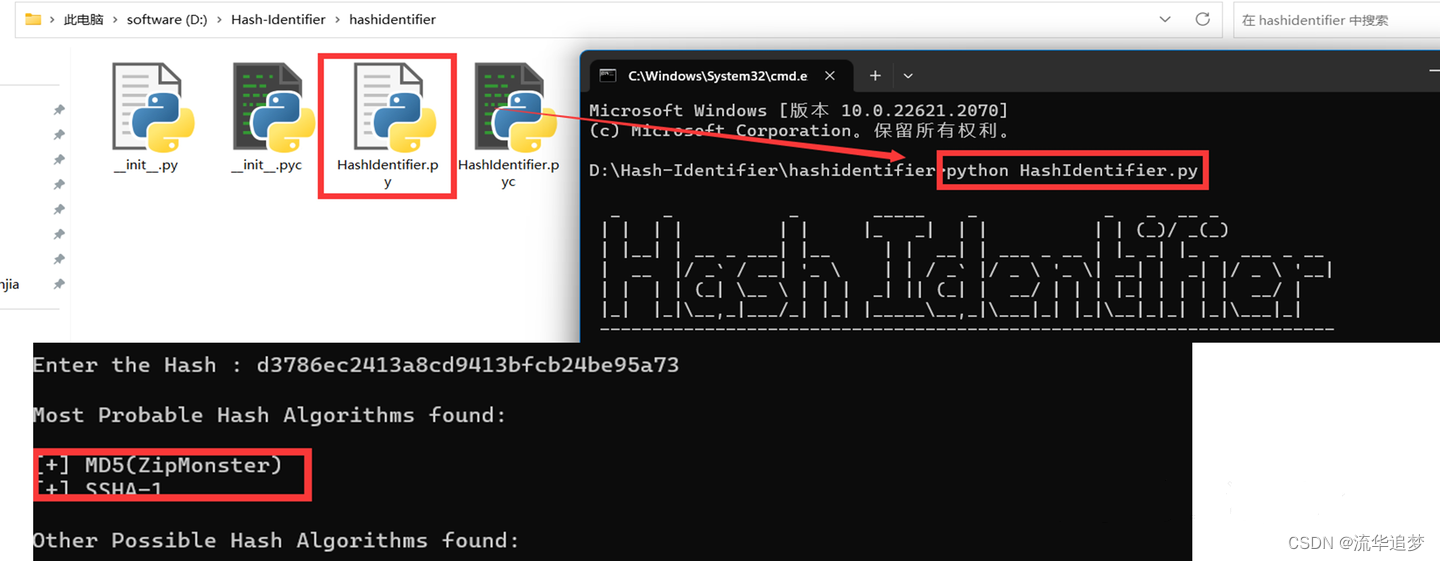
2.2. hash 类型识别工具 hashidentifier
可以使用 hashidentifier 识别数据的 hash 算法类型,hashidentifier 是 python 开发的工具,需要有 python3 的基础环境,下载压缩包,解压就可以使用。
2.3. john the ripper
一款免费、开源的暴力密码破解器,它有多平台版本,支持目前大多数的加密算法,如 des、md4、md5 等。该软件破解密码方式简单而粗暴,理论上只要时间上面允许,该软件可以破译绝大多数用户密码。john the ripper 免费的开源软件,支持目前大多数的加密算法,如 des、md4、md5 等。它支持多种不同类型的系统架构,包括 unix、linux、windows、dos 模式、beos 和 openvms,主要目的是破解不够牢固的 unix/linux 系统密码。
下载地址:https://www.openwall.com/john/

三. hashcat 全部参数
| 选项全称 | 选项简写 | 类型 | 描述 | 示例 |
|---|---|---|---|---|
| --hash-type | -m | num | 指定要破解的hash类型,如果不指定类型,则默认是md5 | -m 1000 |
| --attack-mode | -a | num | 指定要使用的破解模式,其值参考后面对参数。“-a 0”字典攻击,“-a 1” 组合攻击;“-a 3”掩码攻击。 | -a 3 |
| --version | -v | 查看版本信息 | ||
| --help | -h | 查看帮助信息 | ||
| --quiet | 禁止输出 | |||
| --hex-charset | 假设字符集是用十六进制给出的 | |||
| --hex-salt | 假设salt是十六进制的 | |||
| --hex-wordlist | 假设单词表中的单词是用十六进制表示的 | |||
| --force | 忽略破解过程中的警告信息,跑单条hash可能需要加上此选项 | |||
| --deprecated-check-disable | 启用不推荐使用的插件 | |||
| --status | 启用状态屏幕的自动更新 | |||
| --status-json | 为状态输出启用json格式 | |||
| --status-timer | num | 将状态屏幕更新之间的秒数设置为x | --status-timer=1 | |
| --stdin-timeout-abort | num | 如果在x秒内没有来自stdin的输入,则中止 | --stdin-timeout-abort=300 | |
| --machine-readable | 以机器可读的格式显示状态视图 | |||
| --keep-guessing | 破解后继续猜测散列 | |||
| --self-test-disable | 启动时禁用自检功能 | |||
| --loopback | 将新plains添加到导入目录 | |||
| --markov-hcstat2 | file | 指定要使用的hcstat2文件 | --markov-hcstat2=my.hcstat2 | |
| --markov-disable | 禁用马尔可夫链,模仿经典暴力 | |||
| --markov-classic | 启用经典马尔可夫链,无每个位置 | |||
| --markov-inverse | 启用逆马尔可夫链,无每个位置 | |||
| --markov-threshold | -t | num | 阈值x何时停止接受新的马尔可夫链 | -t 50 |
| --runtime | num | 运行x秒后中止会话 | --runtime=10 | |
| --session | str | 定义特定会话名称 | --session=mysession | |
| --restore | 从--session还原会话 | |||
| --restore-disable | 不写入还原文件 | |||
| --restore-file-path | file | 恢复文件的特定路径 | --restore-file-path=x.restore | |
| --outfile | -o | file | 为恢复的哈希定义输出文件 | -o outfile.txt |
| --outfile-format | str | 要使用的完整文件格式,用逗号分隔 | --outfile-format=1,3 | |
| --outfile-autohex-disable | 禁止在输出平面中使用$hex[] | |||
| --outfile-check-timer | num | 将输出文件检查之间的秒数设置为x | --outfile-check-timer=30 | |
| --wordlist-autohex-disable | 禁用单词列表中$hex[]的转换 | |||
| --separator | -p | char | 哈希列表和输出文件的分隔符字符 | -p : |
| --stdout | 不要破解哈希,而是只打印候选者 | |||
| --show | 将hashlist与potfile进行比较;显示破解的哈希 | |||
| --left | 将hashlist与potfile进行比较;显示未破解的哈希 | |||
| --username | 启用忽略哈希文件中的用户名 | |||
| --remove | 一旦哈希被破解,就可以删除它们 | |||
| --remove-timer | num | 每x秒更新一次输入哈希文件 | --remove-timer=30 | |
| --potfile-disable | 不写入potfile | |||
| --potfile-path | file | potfile的特定路径 | --potfile-path=my.pot | |
| --encoding-from | code | 强制从x进行内部单词表编码 | --encoding-from=iso-8859-15 | |
| --encoding-to | code | 强制内部单词表编码为x | --encoding-to=utf-32le | |
| --debug-mode | num | 定义调试模式(仅通过使用规则混合) | --debug-mode=4 | |
| --debug-file | file | 调试规则的输出文件 | --debug-file=good.log | |
| --induction-dir | dir | 指定用于环回的导入目录 | --induction=inducts | |
| --outfile-check-dir | dir | 指定要监视plains的输出文件目录 | --outfile-check-dir=x | |
| --logfile-disable | 禁用日志文件 | |||
| --hccapx-message-pair | num | 仅从匹配x的hccapx加载消息对 | --hccapx-message-pair=2 | |
| --nonce-error-corrections | num | 替换ap的nonce最后字节的bf大小范围 | --nonce-error-corrections=16 | |
| --keyboard-layout-mapping | file | 特殊哈希模式的键盘布局映射表 | --keyb=german.hckmap | |
| --truecrypt-keyfiles | file | 要使用的密钥文件,用逗号分隔 | --truecrypt-keyf=x.png | |
| --veracrypt-keyfiles | file | 要使用的密钥文件,用逗号分隔 | --veracrypt-keyf=x.txt | |
| --veracrypt-pim-start | num | veracrypt个人迭代乘数启动 | --veracrypt-pim-start=450 | |
| --veracrypt-pim-stop | num | veracrypt个人迭代乘数停止 | --veracrypt-pim-stop=500 | |
| --benchmark | -b | 运行所选哈希模式的基准测试 | ||
| --benchmark-all | 运行所有哈希模式的基准测试(需要-b) | |||
| --speed-only | 返回预期的攻击速度,然后退出 | |||
| --progress-only | 返回理想的进度步长和处理时间 | |||
| --segment-size | -c | num | 将wordfile中缓存的大小(mb)设置为x | -c 32 |
| --bitmap-min | num | 将位图允许的最小位设置为x | --bitmap-min=24 | |
| --bitmap-max | num | 将位图允许的最大位设置为x | --bitmap-max=24 | |
| --cpu-affinity | str | 锁定cpu设备,用逗号分隔 | --cpu-affinity=1,2,3 | |
| --hook-threads | num | 设置挂钩的线程数(每个计算单元) | --hook-threads=8 | |
| --hash-info | 显示每个哈希模式的信息 | |||
| --example-hashes | --hash-info的别名 | |||
| --backend-ignore-cuda | 启动时不要尝试打开cuda接口 | |||
| --backend-ignore-hip | 启动时不要尝试打开hip接口 | |||
| --backend-ignore-metal | 启动时不要尝试打开metal接口 | |||
| --backend-ignore-opencl | 启动时不要尝试打开opencl接口 | |||
| --backend-info | -i | 显示系统/环境/后端api信息 | -i or -ii | |
| --backend-devices | -d | str | 要使用的后端设备,用逗号分隔 | -d 1 |
| --opencl-device-types | -d | str | 要使用的opencl,用逗号分隔 | -d 1 |
| --optimized-kernel-enable | -o | 启用优化内核(限制密码长度) | ||
| --multiply-accel-disable | -m | 禁用将内核加速与处理器计数相乘 | ||
| --workload-profile | -w | num | 启用特定的工作负载配置文件,请参阅下面的池,有4种选项 | -w 3 |
| --kernel-accel | -n | num | 手动工作负载调整,将outerloop步长设置为x | -n 64 |
| --kernel-loops | -u | num | 手动工作负载调整,将innerloop步长设置为x | -u 256 |
| --kernel-threads | -t | num | 手动工作负载调整,将线程数设置为x | -t 64 |
| --backend-vector-width | num | 手动将后端矢量宽度覆盖为x | --backend-vector=4 | |
| --spin-damp | num | 使用cpu进行设备同步(百分比) | --spin-damp=10 | |
| --hwmon-disable | 禁用温度和风扇转速读数和触发器 | |||
| --hwmon-temp-abort | num | 如果温度达到x摄氏度,则中止 | --hwmon-temp-abort=100 | |
| --scrypt-tmto | num | 手动将scrypt的tmto值重写为x | --scrypt-tmto=3 | |
| --skip | -s | num | 从开头跳过x个单词 | -s 1000000 |
| --limit | -l | num | 从开始限制x个单词+跳过的单词 | -l 1000000 |
| --keyspace | 显示密钥空间基础:mod值并退出 | |||
| --rule-left | -j | rule | 单个规则应用于左侧单词列表中的每个单词 | -j 'c' |
| --rule-right | -k | rule | 单个规则应用于右侧单词列表中的每个单词 | -k '^-' |
| --rules-file | -r | file | 使用自定义破解规则 | -r rules/best64.rule |
| --generate-rules | -g | num | 生成x个随机规则 | -g 10000 |
| --generate-rules-func-min | num | 强制每个规则至少x个函数 | ||
| --generate-rules-func-max | num | 强制每个规则至多x个函数 | ||
| --generate-rules-func-sel | str | 对随机规则引擎有效的规则运算符池 | --generate-rules-func-sel=iotlc | |
| --generate-rules-seed | num | 强制rng种子设置为x | ||
| --custom-charset1 | -1 | cs | 用户定义的字符集 ?1 | -1 ?l?d?u |
| --custom-charset2 | -2 | cs | 用户定义的字符集 ?2 | -2 ?l?d?s |
| --custom-charset3 | -3 | cs | 用户定义的字符集 ?3 | |
| --custom-charset4 | -4 | cs | 用户定义的字符集 ?4 | |
| --identify | 显示所有支持的输入哈希算法 | --identify my.hash | ||
| --increment | -i | 启用掩码增量模式 | ||
| --increment-min | num | 在x处开始掩码递增 | --increment-min=4 | |
| --increment-max | num | 在x处停止掩码递增 | --increment-max=8 | |
| --slow-candidates | -s | 启用较慢(但高级)的候选生成器 | ||
| --brain-server | 启用大脑服务器 | |||
| --brain-server-timer | num | 每x秒更新一次大脑服务器转储(最小值:60) | --brain-server-timer=300 | |
| --brain-client | -z | 启用大脑客户端,激活-s | ||
| --brain-client-features | num | 定义大脑客户端功能,见下文 | --brain-client-features=3 | |
| --brain-host | str | 大脑服务器主机(ip或域) | --brain-host=127.0.0.1 | |
| --brain-port | port | brain服务器端口 | --brain-port=13743 | |
| --brain-password | str | brain server身份验证密码 | --brain-password=123 | |
| --brain-session | hex | 覆盖自动计算的大脑会话 | --brain-session=0x2ae611db | |
| --brain-session-whitelist | hex | 仅允许给定的会话,用逗号分隔 | --brain-session-whitelist=0x2ae611db |
3.1. hashcat 的攻击模式(-a 参数)
使用的格式为:-a 后跟对应的数字编号
0 | straight(字段破解)
1 | combination(将字典中密码进行组合,例:1,2 -> 11 22 12 21)
3 | brute-force(掩码暴力破解)
6 | hybrid wordlist + mask(字典+掩码破解)
7 | hybrid mask + wordlist(掩码+字典破解)
9 | association(关联破解)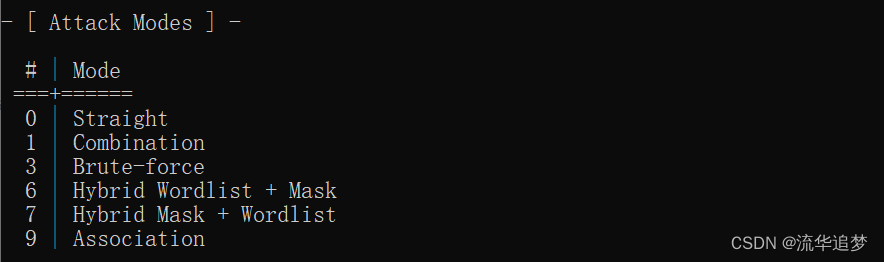
3.2. 输出格式(--outfile-format 参数)
1 | hash[:salt]
2 | plain
3 | hex_plain
4 | crack_pos
5 | timestamp absolute
6 | timestamp relative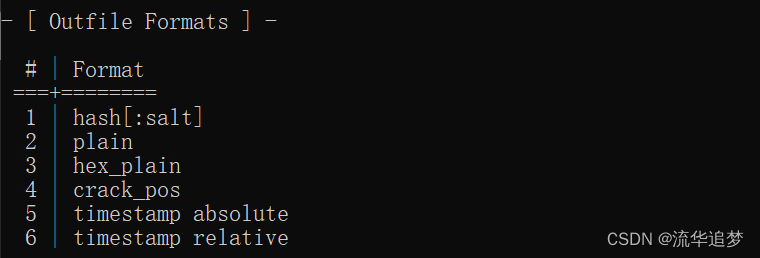
3.3. 内置掩码字符集
l | abcdefghijklmnopqrstuvwxyz [a-z]
u | abcdefghijklmnopqrstuvwxyz [a-z]
d | 0123456789 [0-9]
h | 0123456789abcdef [0-9a-f]
h | 0123456789abcdef [0-9a-f]
s | !"#$%&'()*+,-./:;<=>?@[\]^_`{|}~
a | ?l?u?d?s
b | 0x00 - 0xff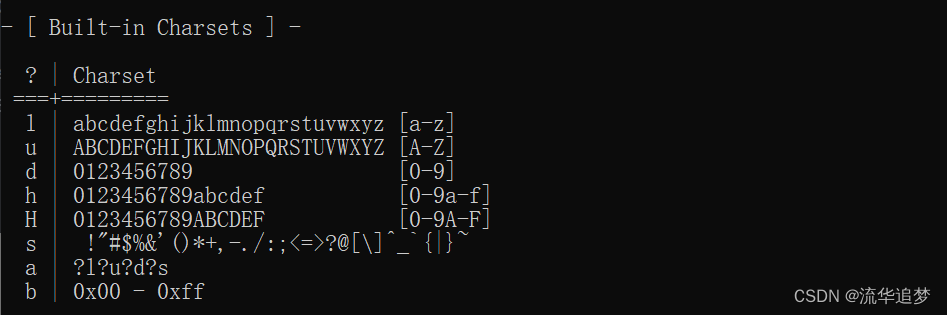
字符集含义:
- ?l:代表小写字母
- ?u:代表大写字母
- ?d:代表数字
- ?s:代表特殊字符
- ?a:代表大小写字母、数字以及特殊字符
- ?b:0x00-0xff
掩码的使用格式:
- 八位数字密码:?d?d?d?d?d?d?d?d
- 八位未知密码:?a?a?a?a?a?a?a?a
- 前四位为大写字母,后面四位为数字:?u?u?u?u?d?d?d?d
- 前四位为数字或者是小写字母,后四位为大写字母或者数字:?h?h?h?h?h?h?h?h
- 前三个字符未知,中间为admin,后三位未知:?a?a?aadmin?a?a?a
- 6-8 位数字密码:--increment --increment-min 6 --increment-max 8
- 6-8 位数字+小写字母密码:--increment --increment-min 6 --increment-max 8 ?h?h?h?h?h?h?h?h
3.4. hash 类型对照表(-m 参数)
可以通过 hashcat --help 查看。
# | name | category
======+============================================================+======================================
900 | md4 | raw hash
0 | md5 | raw hash
100 | sha1 | raw hash
1300 | sha2-224 | raw hash
1400 | sha2-256 | raw hash
10800 | sha2-384 | raw hash
1700 | sha2-512 | raw hash
17300 | sha3-224 | raw hash
17400 | sha3-256 | raw hash
17500 | sha3-384 | raw hash
17600 | sha3-512 | raw hash
6000 | ripemd-160 | raw hash
600 | blake2b-512 | raw hash
11700 | gost r 34.11-2012 (streebog) 256-bit, big-endian | raw hash
11800 | gost r 34.11-2012 (streebog) 512-bit, big-endian | raw hash
6900 | gost r 34.11-94 | raw hash
17010 | gpg (aes-128/aes-256 (sha-1($pass))) | raw hash
5100 | half md5 | raw hash
17700 | keccak-224 | raw hash
17800 | keccak-256 | raw hash
17900 | keccak-384 | raw hash
18000 | keccak-512 | raw hash
6100 | whirlpool | raw hash
10100 | siphash | raw hash
70 | md5(utf16le($pass)) | raw hash
170 | sha1(utf16le($pass)) | raw hash
1470 | sha256(utf16le($pass)) | raw hash
10870 | sha384(utf16le($pass)) | raw hash
1770 | sha512(utf16le($pass)) | raw hash
610 | blake2b-512($pass.$salt) | raw hash salted and/or iterated
620 | blake2b-512($salt.$pass) | raw hash salted and/or iterated
10 | md5($pass.$salt) | raw hash salted and/or iterated
20 | md5($salt.$pass) | raw hash salted and/or iterated
3800 | md5($salt.$pass.$salt) | raw hash salted and/or iterated
3710 | md5($salt.md5($pass)) | raw hash salted and/or iterated
4110 | md5($salt.md5($pass.$salt)) | raw hash salted and/or iterated
4010 | md5($salt.md5($salt.$pass)) | raw hash salted and/or iterated
21300 | md5($salt.sha1($salt.$pass)) | raw hash salted and/or iterated
40 | md5($salt.utf16le($pass)) | raw hash salted and/or iterated
2600 | md5(md5($pass)) | raw hash salted and/or iterated
3910 | md5(md5($pass).md5($salt)) | raw hash salted and/or iterated
3500 | md5(md5(md5($pass))) | raw hash salted and/or iterated
4400 | md5(sha1($pass)) | raw hash salted and/or iterated
4410 | md5(sha1($pass).$salt) | raw hash salted and/or iterated
20900 | md5(sha1($pass).md5($pass).sha1($pass)) | raw hash salted and/or iterated
21200 | md5(sha1($salt).md5($pass)) | raw hash salted and/or iterated
4300 | md5(strtoupper(md5($pass))) | raw hash salted and/or iterated
30 | md5(utf16le($pass).$salt) | raw hash salted and/or iterated
110 | sha1($pass.$salt) | raw hash salted and/or iterated
120 | sha1($salt.$pass) | raw hash salted and/or iterated
4900 | sha1($salt.$pass.$salt) | raw hash salted and/or iterated
4520 | sha1($salt.sha1($pass)) | raw hash salted and/or iterated
24300 | sha1($salt.sha1($pass.$salt)) | raw hash salted and/or iterated
140 | sha1($salt.utf16le($pass)) | raw hash salted and/or iterated
19300 | sha1($salt1.$pass.$salt2) | raw hash salted and/or iterated
14400 | sha1(cx) | raw hash salted and/or iterated
4700 | sha1(md5($pass)) | raw hash salted and/or iterated
4710 | sha1(md5($pass).$salt) | raw hash salted and/or iterated
21100 | sha1(md5($pass.$salt)) | raw hash salted and/or iterated
18500 | sha1(md5(md5($pass))) | raw hash salted and/or iterated
4500 | sha1(sha1($pass)) | raw hash salted and/or iterated
4510 | sha1(sha1($pass).$salt) | raw hash salted and/or iterated
5000 | sha1(sha1($salt.$pass.$salt)) | raw hash salted and/or iterated
130 | sha1(utf16le($pass).$salt) | raw hash salted and/or iterated
1410 | sha256($pass.$salt) | raw hash salted and/or iterated
1420 | sha256($salt.$pass) | raw hash salted and/or iterated
22300 | sha256($salt.$pass.$salt) | raw hash salted and/or iterated
20720 | sha256($salt.sha256($pass)) | raw hash salted and/or iterated
21420 | sha256($salt.sha256_bin($pass)) | raw hash salted and/or iterated
1440 | sha256($salt.utf16le($pass)) | raw hash salted and/or iterated
20800 | sha256(md5($pass)) | raw hash salted and/or iterated
20710 | sha256(sha256($pass).$salt) | raw hash salted and/or iterated
21400 | sha256(sha256_bin($pass)) | raw hash salted and/or iterated
1430 | sha256(utf16le($pass).$salt) | raw hash salted and/or iterated
10810 | sha384($pass.$salt) | raw hash salted and/or iterated
10820 | sha384($salt.$pass) | raw hash salted and/or iterated
10840 | sha384($salt.utf16le($pass)) | raw hash salted and/or iterated
10830 | sha384(utf16le($pass).$salt) | raw hash salted and/or iterated
1710 | sha512($pass.$salt) | raw hash salted and/or iterated
1720 | sha512($salt.$pass) | raw hash salted and/or iterated
1740 | sha512($salt.utf16le($pass)) | raw hash salted and/or iterated
1730 | sha512(utf16le($pass).$salt) | raw hash salted and/or iterated
50 | hmac-md5 (key = $pass) | raw hash authenticated
60 | hmac-md5 (key = $salt) | raw hash authenticated
150 | hmac-sha1 (key = $pass) | raw hash authenticated
160 | hmac-sha1 (key = $salt) | raw hash authenticated
1450 | hmac-sha256 (key = $pass) | raw hash authenticated
1460 | hmac-sha256 (key = $salt) | raw hash authenticated
1750 | hmac-sha512 (key = $pass) | raw hash authenticated
1760 | hmac-sha512 (key = $salt) | raw hash authenticated
11750 | hmac-streebog-256 (key = $pass), big-endian | raw hash authenticated
11760 | hmac-streebog-256 (key = $salt), big-endian | raw hash authenticated
11850 | hmac-streebog-512 (key = $pass), big-endian | raw hash authenticated
11860 | hmac-streebog-512 (key = $salt), big-endian | raw hash authenticated
28700 | amazon aws4-hmac-sha256 | raw hash authenticated
11500 | crc32 | raw checksum
27900 | crc32c | raw checksum
28000 | crc64jones | raw checksum
18700 | java object hashcode() | raw checksum
25700 | murmurhash | raw checksum
27800 | murmurhash3 | raw checksum
14100 | 3des (pt = $salt, key = $pass) | raw cipher, known-plaintext attack
14000 | des (pt = $salt, key = $pass) | raw cipher, known-plaintext attack
26401 | aes-128-ecb nokdf (pt = $salt, key = $pass) | raw cipher, known-plaintext attack
26402 | aes-192-ecb nokdf (pt = $salt, key = $pass) | raw cipher, known-plaintext attack
26403 | aes-256-ecb nokdf (pt = $salt, key = $pass) | raw cipher, known-plaintext attack
15400 | chacha20 | raw cipher, known-plaintext attack
14500 | linux kernel crypto api (2.4) | raw cipher, known-plaintext attack
14900 | skip32 (pt = $salt, key = $pass) | raw cipher, known-plaintext attack
11900 | pbkdf2-hmac-md5 | generic kdf
12000 | pbkdf2-hmac-sha1 | generic kdf
10900 | pbkdf2-hmac-sha256 | generic kdf
12100 | pbkdf2-hmac-sha512 | generic kdf
8900 | scrypt | generic kdf
400 | phpass | generic kdf
16100 | tacacs+ | network protocol
11400 | sip digest authentication (md5) | network protocol
5300 | ike-psk md5 | network protocol
5400 | ike-psk sha1 | network protocol
25100 | snmpv3 hmac-md5-96 | network protocol
25000 | snmpv3 hmac-md5-96/hmac-sha1-96 | network protocol
25200 | snmpv3 hmac-sha1-96 | network protocol
26700 | snmpv3 hmac-sha224-128 | network protocol
26800 | snmpv3 hmac-sha256-192 | network protocol
26900 | snmpv3 hmac-sha384-256 | network protocol
27300 | snmpv3 hmac-sha512-384 | network protocol
2500 | wpa-eapol-pbkdf2 | network protocol
2501 | wpa-eapol-pmk | network protocol
22000 | wpa-pbkdf2-pmkid+eapol | network protocol
22001 | wpa-pmk-pmkid+eapol | network protocol
16800 | wpa-pmkid-pbkdf2 | network protocol
16801 | wpa-pmkid-pmk | network protocol
7300 | ipmi2 rakp hmac-sha1 | network protocol
10200 | cram-md5 | network protocol
16500 | jwt (json web token) | network protocol
29200 | radmin3 | network protocol
19600 | kerberos 5, etype 17, tgs-rep | network protocol
19800 | kerberos 5, etype 17, pre-auth | network protocol
28800 | kerberos 5, etype 17, db | network protocol
19700 | kerberos 5, etype 18, tgs-rep | network protocol
19900 | kerberos 5, etype 18, pre-auth | network protocol
28900 | kerberos 5, etype 18, db | network protocol
7500 | kerberos 5, etype 23, as-req pre-auth | network protocol
13100 | kerberos 5, etype 23, tgs-rep | network protocol
18200 | kerberos 5, etype 23, as-rep | network protocol
5500 | netntlmv1 / netntlmv1+ess | network protocol
27000 | netntlmv1 / netntlmv1+ess (nt) | network protocol
5600 | netntlmv2 | network protocol
27100 | netntlmv2 (nt) | network protocol
29100 | flask session cookie ($salt.$salt.$pass) | network protocol
4800 | iscsi chap authentication, md5(chap) | network protocol
8500 | racf | operating system
6300 | aix {smd5} | operating system
6700 | aix {ssha1} | operating system
6400 | aix {ssha256} | operating system
6500 | aix {ssha512} | operating system
3000 | lm | operating system
19000 | qnx /etc/shadow (md5) | operating system
19100 | qnx /etc/shadow (sha256) | operating system
19200 | qnx /etc/shadow (sha512) | operating system
15300 | dpapi masterkey file v1 (context 1 and 2) | operating system
15310 | dpapi masterkey file v1 (context 3) | operating system
15900 | dpapi masterkey file v2 (context 1 and 2) | operating system
15910 | dpapi masterkey file v2 (context 3) | operating system
7200 | grub 2 | operating system
12800 | ms-azuresync pbkdf2-hmac-sha256 | operating system
12400 | bsdi crypt, extended des | operating system
1000 | ntlm | operating system
9900 | radmin2 | operating system
5800 | samsung android password/pin | operating system
28100 | windows hello pin/password | operating system
13800 | windows phone 8+ pin/password | operating system
2410 | cisco-asa md5 | operating system
9200 | cisco-ios $8$ (pbkdf2-sha256) | operating system
9300 | cisco-ios $9$ (scrypt) | operating system
5700 | cisco-ios type 4 (sha256) | operating system
2400 | cisco-pix md5 | operating system
8100 | citrix netscaler (sha1) | operating system
22200 | citrix netscaler (sha512) | operating system
1100 | domain cached credentials (dcc), ms cache | operating system
2100 | domain cached credentials 2 (dcc2), ms cache 2 | operating system
7000 | fortigate (fortios) | operating system
26300 | fortigate256 (fortios256) | operating system
125 | arubaos | operating system
501 | juniper ive | operating system
22 | juniper netscreen/ssg (screenos) | operating system
15100 | juniper/netbsd sha1crypt | operating system
26500 | iphone passcode (uid key + system keybag) | operating system
122 | macos v10.4, macos v10.5, macos v10.6 | operating system
1722 | macos v10.7 | operating system
7100 | macos v10.8+ (pbkdf2-sha512) | operating system
3200 | bcrypt $2*$, blowfish (unix) | operating system
500 | md5crypt, md5 (unix), cisco-ios $1$ (md5) | operating system
1500 | descrypt, des (unix), traditional des | operating system
29000 | sha1($salt.sha1(utf16le($username).':'.utf16le($pass))) | operating system
7400 | sha256crypt $5$, sha256 (unix) | operating system
1800 | sha512crypt $6$, sha512 (unix) | operating system
24600 | sqlcipher | database server
131 | mssql (2000) | database server
132 | mssql (2005) | database server
1731 | mssql (2012, 2014) | database server
24100 | mongodb serverkey scram-sha-1 | database server
24200 | mongodb serverkey scram-sha-256 | database server
12 | postgresql | database server
11100 | postgresql cram (md5) | database server
28600 | postgresql scram-sha-256 | database server
3100 | oracle h: type (oracle 7+) | database server
112 | oracle s: type (oracle 11+) | database server
12300 | oracle t: type (oracle 12+) | database server
7401 | mysql $a$ (sha256crypt) | database server
11200 | mysql cram (sha1) | database server
200 | mysql323 | database server
300 | mysql4.1/mysql5 | database server
8000 | sybase ase | database server
8300 | dnssec (nsec3) | ftp, http, smtp, ldap server
25900 | knx ip secure - device authentication code | ftp, http, smtp, ldap server
16400 | cram-md5 dovecot | ftp, http, smtp, ldap server
1411 | ssha-256(base64), ldap {ssha256} | ftp, http, smtp, ldap server
1711 | ssha-512(base64), ldap {ssha512} | ftp, http, smtp, ldap server
24900 | dahua authentication md5 | ftp, http, smtp, ldap server
10901 | redhat 389-ds ldap (pbkdf2-hmac-sha256) | ftp, http, smtp, ldap server
15000 | filezilla server >= 0.9.55 | ftp, http, smtp, ldap server
12600 | coldfusion 10+ | ftp, http, smtp, ldap server
1600 | apache $apr1$ md5, md5apr1, md5 (apr) | ftp, http, smtp, ldap server
141 | episerver 6.x < .net 4 | ftp, http, smtp, ldap server
1441 | episerver 6.x >= .net 4 | ftp, http, smtp, ldap server
1421 | hmailserver | ftp, http, smtp, ldap server
101 | nsldap, sha-1(base64), netscape ldap sha | ftp, http, smtp, ldap server
111 | nsldaps, ssha-1(base64), netscape ldap ssha | ftp, http, smtp, ldap server
7700 | sap codvn b (bcode) | enterprise application software (eas)
7701 | sap codvn b (bcode) from rfc_read_table | enterprise application software (eas)
7800 | sap codvn f/g (passcode) | enterprise application software (eas)
7801 | sap codvn f/g (passcode) from rfc_read_table | enterprise application software (eas)
10300 | sap codvn h (pwdsaltedhash) issha-1 | enterprise application software (eas)
133 | peoplesoft | enterprise application software (eas)
13500 | peoplesoft ps_token | enterprise application software (eas)
21500 | solarwinds orion | enterprise application software (eas)
21501 | solarwinds orion v2 | enterprise application software (eas)
24 | solarwinds serv-u | enterprise application software (eas)
8600 | lotus notes/domino 5 | enterprise application software (eas)
8700 | lotus notes/domino 6 | enterprise application software (eas)
9100 | lotus notes/domino 8 | enterprise application software (eas)
26200 | openedge progress encode | enterprise application software (eas)
20600 | oracle transportation management (sha256) | enterprise application software (eas)
4711 | huawei sha1(md5($pass).$salt) | enterprise application software (eas)
20711 | authme sha256 | enterprise application software (eas)
22400 | aes crypt (sha256) | full-disk encryption (fde)
27400 | vmware vmx (pbkdf2-hmac-sha1 + aes-256-cbc) | full-disk encryption (fde)
14600 | luks v1 (legacy) | full-disk encryption (fde)
29541 | luks v1 ripemd-160 + aes | full-disk encryption (fde)
29542 | luks v1 ripemd-160 + serpent | full-disk encryption (fde)
29543 | luks v1 ripemd-160 + twofish | full-disk encryption (fde)
29511 | luks v1 sha-1 + aes | full-disk encryption (fde)
29512 | luks v1 sha-1 + serpent | full-disk encryption (fde)
29513 | luks v1 sha-1 + twofish | full-disk encryption (fde)
29521 | luks v1 sha-256 + aes | full-disk encryption (fde)
29522 | luks v1 sha-256 + serpent | full-disk encryption (fde)
29523 | luks v1 sha-256 + twofish | full-disk encryption (fde)
29531 | luks v1 sha-512 + aes | full-disk encryption (fde)
29532 | luks v1 sha-512 + serpent | full-disk encryption (fde)
29533 | luks v1 sha-512 + twofish | full-disk encryption (fde)
13711 | veracrypt ripemd160 + xts 512 bit (legacy) | full-disk encryption (fde)
13712 | veracrypt ripemd160 + xts 1024 bit (legacy) | full-disk encryption (fde)
13713 | veracrypt ripemd160 + xts 1536 bit (legacy) | full-disk encryption (fde)
13741 | veracrypt ripemd160 + xts 512 bit + boot-mode (legacy) | full-disk encryption (fde)
13742 | veracrypt ripemd160 + xts 1024 bit + boot-mode (legacy) | full-disk encryption (fde)
13743 | veracrypt ripemd160 + xts 1536 bit + boot-mode (legacy) | full-disk encryption (fde)
29411 | veracrypt ripemd160 + xts 512 bit | full-disk encryption (fde)
29412 | veracrypt ripemd160 + xts 1024 bit | full-disk encryption (fde)
29413 | veracrypt ripemd160 + xts 1536 bit | full-disk encryption (fde)
29441 | veracrypt ripemd160 + xts 512 bit + boot-mode | full-disk encryption (fde)
29442 | veracrypt ripemd160 + xts 1024 bit + boot-mode | full-disk encryption (fde)
29443 | veracrypt ripemd160 + xts 1536 bit + boot-mode | full-disk encryption (fde)
13751 | veracrypt sha256 + xts 512 bit (legacy) | full-disk encryption (fde)
13752 | veracrypt sha256 + xts 1024 bit (legacy) | full-disk encryption (fde)
13753 | veracrypt sha256 + xts 1536 bit (legacy) | full-disk encryption (fde)
13761 | veracrypt sha256 + xts 512 bit + boot-mode (legacy) | full-disk encryption (fde)
13762 | veracrypt sha256 + xts 1024 bit + boot-mode (legacy) | full-disk encryption (fde)
13763 | veracrypt sha256 + xts 1536 bit + boot-mode (legacy) | full-disk encryption (fde)
29451 | veracrypt sha256 + xts 512 bit | full-disk encryption (fde)
29452 | veracrypt sha256 + xts 1024 bit | full-disk encryption (fde)
29453 | veracrypt sha256 + xts 1536 bit | full-disk encryption (fde)
29461 | veracrypt sha256 + xts 512 bit + boot-mode | full-disk encryption (fde)
29462 | veracrypt sha256 + xts 1024 bit + boot-mode | full-disk encryption (fde)
29463 | veracrypt sha256 + xts 1536 bit + boot-mode | full-disk encryption (fde)
13721 | veracrypt sha512 + xts 512 bit (legacy) | full-disk encryption (fde)
13722 | veracrypt sha512 + xts 1024 bit (legacy) | full-disk encryption (fde)
13723 | veracrypt sha512 + xts 1536 bit (legacy) | full-disk encryption (fde)
29421 | veracrypt sha512 + xts 512 bit | full-disk encryption (fde)
29422 | veracrypt sha512 + xts 1024 bit | full-disk encryption (fde)
29423 | veracrypt sha512 + xts 1536 bit | full-disk encryption (fde)
13771 | veracrypt streebog-512 + xts 512 bit (legacy) | full-disk encryption (fde)
13772 | veracrypt streebog-512 + xts 1024 bit (legacy) | full-disk encryption (fde)
13773 | veracrypt streebog-512 + xts 1536 bit (legacy) | full-disk encryption (fde)
13781 | veracrypt streebog-512 + xts 512 bit + boot-mode (legacy) | full-disk encryption (fde)
13782 | veracrypt streebog-512 + xts 1024 bit + boot-mode (legacy) | full-disk encryption (fde)
13783 | veracrypt streebog-512 + xts 1536 bit + boot-mode (legacy) | full-disk encryption (fde)
29471 | veracrypt streebog-512 + xts 512 bit | full-disk encryption (fde)
29472 | veracrypt streebog-512 + xts 1024 bit | full-disk encryption (fde)
29473 | veracrypt streebog-512 + xts 1536 bit | full-disk encryption (fde)
29481 | veracrypt streebog-512 + xts 512 bit + boot-mode | full-disk encryption (fde)
29482 | veracrypt streebog-512 + xts 1024 bit + boot-mode | full-disk encryption (fde)
29483 | veracrypt streebog-512 + xts 1536 bit + boot-mode | full-disk encryption (fde)
13731 | veracrypt whirlpool + xts 512 bit (legacy) | full-disk encryption (fde)
13732 | veracrypt whirlpool + xts 1024 bit (legacy) | full-disk encryption (fde)
13733 | veracrypt whirlpool + xts 1536 bit (legacy) | full-disk encryption (fde)
29431 | veracrypt whirlpool + xts 512 bit | full-disk encryption (fde)
29432 | veracrypt whirlpool + xts 1024 bit | full-disk encryption (fde)
29433 | veracrypt whirlpool + xts 1536 bit | full-disk encryption (fde)
23900 | bestcrypt v3 volume encryption | full-disk encryption (fde)
16700 | filevault 2 | full-disk encryption (fde)
27500 | virtualbox (pbkdf2-hmac-sha256 & aes-128-xts) | full-disk encryption (fde)
27600 | virtualbox (pbkdf2-hmac-sha256 & aes-256-xts) | full-disk encryption (fde)
20011 | diskcryptor sha512 + xts 512 bit | full-disk encryption (fde)
20012 | diskcryptor sha512 + xts 1024 bit | full-disk encryption (fde)
20013 | diskcryptor sha512 + xts 1536 bit | full-disk encryption (fde)
22100 | bitlocker | full-disk encryption (fde)
12900 | android fde (samsung dek) | full-disk encryption (fde)
8800 | android fde <= 4.3 | full-disk encryption (fde)
18300 | apple file system (apfs) | full-disk encryption (fde)
6211 | truecrypt ripemd160 + xts 512 bit (legacy) | full-disk encryption (fde)
6212 | truecrypt ripemd160 + xts 1024 bit (legacy) | full-disk encryption (fde)
6213 | truecrypt ripemd160 + xts 1536 bit (legacy) | full-disk encryption (fde)
6241 | truecrypt ripemd160 + xts 512 bit + boot-mode (legacy) | full-disk encryption (fde)
6242 | truecrypt ripemd160 + xts 1024 bit + boot-mode (legacy) | full-disk encryption (fde)
6243 | truecrypt ripemd160 + xts 1536 bit + boot-mode (legacy) | full-disk encryption (fde)
29311 | truecrypt ripemd160 + xts 512 bit | full-disk encryption (fde)
29312 | truecrypt ripemd160 + xts 1024 bit | full-disk encryption (fde)
29313 | truecrypt ripemd160 + xts 1536 bit | full-disk encryption (fde)
29341 | truecrypt ripemd160 + xts 512 bit + boot-mode | full-disk encryption (fde)
29342 | truecrypt ripemd160 + xts 1024 bit + boot-mode | full-disk encryption (fde)
29343 | truecrypt ripemd160 + xts 1536 bit + boot-mode | full-disk encryption (fde)
6221 | truecrypt sha512 + xts 512 bit (legacy) | full-disk encryption (fde)
6222 | truecrypt sha512 + xts 1024 bit (legacy) | full-disk encryption (fde)
6223 | truecrypt sha512 + xts 1536 bit (legacy) | full-disk encryption (fde)
29321 | truecrypt sha512 + xts 512 bit | full-disk encryption (fde)
29322 | truecrypt sha512 + xts 1024 bit | full-disk encryption (fde)
29323 | truecrypt sha512 + xts 1536 bit | full-disk encryption (fde)
6231 | truecrypt whirlpool + xts 512 bit (legacy) | full-disk encryption (fde)
6232 | truecrypt whirlpool + xts 1024 bit (legacy) | full-disk encryption (fde)
6233 | truecrypt whirlpool + xts 1536 bit (legacy) | full-disk encryption (fde)
29331 | truecrypt whirlpool + xts 512 bit | full-disk encryption (fde)
29332 | truecrypt whirlpool + xts 1024 bit | full-disk encryption (fde)
29333 | truecrypt whirlpool + xts 1536 bit | full-disk encryption (fde)
12200 | ecryptfs | full-disk encryption (fde)
10400 | pdf 1.1 - 1.3 (acrobat 2 - 4) | document
10410 | pdf 1.1 - 1.3 (acrobat 2 - 4), collider #1 | document
10420 | pdf 1.1 - 1.3 (acrobat 2 - 4), collider #2 | document
10500 | pdf 1.4 - 1.6 (acrobat 5 - 8) | document
25400 | pdf 1.4 - 1.6 (acrobat 5 - 8) - user and owner pass | document
10600 | pdf 1.7 level 3 (acrobat 9) | document
10700 | pdf 1.7 level 8 (acrobat 10 - 11) | document
9400 | ms office 2007 | document
9500 | ms office 2010 | document
9600 | ms office 2013 | document
25300 | ms office 2016 - sheetprotection | document
9700 | ms office <= 2003 $0/$1, md5 + rc4 | document
9710 | ms office <= 2003 $0/$1, md5 + rc4, collider #1 | document
9720 | ms office <= 2003 $0/$1, md5 + rc4, collider #2 | document
9810 | ms office <= 2003 $3, sha1 + rc4, collider #1 | document
9820 | ms office <= 2003 $3, sha1 + rc4, collider #2 | document
9800 | ms office <= 2003 $3/$4, sha1 + rc4 | document
18400 | open document format (odf) 1.2 (sha-256, aes) | document
18600 | open document format (odf) 1.1 (sha-1, blowfish) | document
16200 | apple secure notes | document
23300 | apple iwork | document
6600 | 1password, agilekeychain | password manager
8200 | 1password, cloudkeychain | password manager
9000 | password safe v2 | password manager
5200 | password safe v3 | password manager
6800 | lastpass + lastpass sniffed | password manager
13400 | keepass 1 (aes/twofish) and keepass 2 (aes) | password manager
29700 | keepass 1 (aes/twofish) and keepass 2 (aes) - keyfile only mode | password manager
23400 | bitwarden | password manager
16900 | ansible vault | password manager
26000 | mozilla key3.db | password manager
26100 | mozilla key4.db | password manager
23100 | apple keychain | password manager
11600 | 7-zip | archive
12500 | rar3-hp | archive
23800 | rar3-p (compressed) | archive
23700 | rar3-p (uncompressed) | archive
13000 | rar5 | archive
17220 | pkzip (compressed multi-file) | archive
17200 | pkzip (compressed) | archive
17225 | pkzip (mixed multi-file) | archive
17230 | pkzip (mixed multi-file checksum-only) | archive
17210 | pkzip (uncompressed) | archive
20500 | pkzip master key | archive
20510 | pkzip master key (6 byte optimization) | archive
23001 | securezip aes-128 | archive
23002 | securezip aes-192 | archive
23003 | securezip aes-256 | archive
13600 | winzip | archive
18900 | android backup | archive
24700 | stuffit5 | archive
13200 | axcrypt 1 | archive
13300 | axcrypt 1 in-memory sha1 | archive
23500 | axcrypt 2 aes-128 | archive
23600 | axcrypt 2 aes-256 | archive
14700 | itunes backup < 10.0 | archive
14800 | itunes backup >= 10.0 | archive
8400 | wbb3 (woltlab burning board) | forums, cms, e-commerce
2612 | phps | forums, cms, e-commerce
121 | smf (simple machines forum) > v1.1 | forums, cms, e-commerce
3711 | mediawiki b type | forums, cms, e-commerce
4521 | redmine | forums, cms, e-commerce
24800 | umbraco hmac-sha1 | forums, cms, e-commerce
11 | joomla < 2.5.18 | forums, cms, e-commerce
13900 | opencart | forums, cms, e-commerce
11000 | prestashop | forums, cms, e-commerce
16000 | tripcode | forums, cms, e-commerce
7900 | drupal7 | forums, cms, e-commerce
4522 | punbb | forums, cms, e-commerce
2811 | mybb 1.2+, ipb2+ (invision power board) | forums, cms, e-commerce
2611 | vbulletin < v3.8.5 | forums, cms, e-commerce
2711 | vbulletin >= v3.8.5 | forums, cms, e-commerce
25600 | bcrypt(md5($pass)) / bcryptmd5 | forums, cms, e-commerce
25800 | bcrypt(sha1($pass)) / bcryptsha1 | forums, cms, e-commerce
28400 | bcrypt(sha512($pass)) / bcryptsha512 | forums, cms, e-commerce
21 | oscommerce, xt:commerce | forums, cms, e-commerce
18100 | totp (hmac-sha1) | one-time password
2000 | stdout | plaintext
99999 | plaintext | plaintext
21600 | web2py pbkdf2-sha512 | framework
10000 | django (pbkdf2-sha256) | framework
124 | django (sha-1) | framework
12001 | atlassian (pbkdf2-hmac-sha1) | framework
19500 | ruby on rails restful-authentication | framework
27200 | ruby on rails restful auth (one round, no sitekey) | framework
30000 | python werkzeug md5 (hmac-md5 (key = $salt)) | framework
30120 | python werkzeug sha256 (hmac-sha256 (key = $salt)) | framework
20200 | python passlib pbkdf2-sha512 | framework
20300 | python passlib pbkdf2-sha256 | framework
20400 | python passlib pbkdf2-sha1 | framework
24410 | pkcs#8 private keys (pbkdf2-hmac-sha1 + 3des/aes) | private key
24420 | pkcs#8 private keys (pbkdf2-hmac-sha256 + 3des/aes) | private key
15500 | jks java key store private keys (sha1) | private key
22911 | rsa/dsa/ec/openssh private keys ($0$) | private key
22921 | rsa/dsa/ec/openssh private keys ($6$) | private key
22931 | rsa/dsa/ec/openssh private keys ($1, $3$) | private key
22941 | rsa/dsa/ec/openssh private keys ($4$) | private key
22951 | rsa/dsa/ec/openssh private keys ($5$) | private key
23200 | xmpp scram pbkdf2-sha1 | instant messaging service
28300 | teamspeak 3 (channel hash) | instant messaging service
22600 | telegram desktop < v2.1.14 (pbkdf2-hmac-sha1) | instant messaging service
24500 | telegram desktop >= v2.1.14 (pbkdf2-hmac-sha512) | instant messaging service
22301 | telegram mobile app passcode (sha256) | instant messaging service
23 | skype | instant messaging service
29600 | terra station wallet (aes256-cbc(pbkdf2($pass))) | cryptocurrency wallet
26600 | metamask wallet | cryptocurrency wallet
21000 | bitshares v0.x - sha512(sha512_bin(pass)) | cryptocurrency wallet
28501 | bitcoin wif private key (p2pkh), compressed | cryptocurrency wallet
28502 | bitcoin wif private key (p2pkh), uncompressed | cryptocurrency wallet
28503 | bitcoin wif private key (p2wpkh, bech32), compressed | cryptocurrency wallet
28504 | bitcoin wif private key (p2wpkh, bech32), uncompressed | cryptocurrency wallet
28505 | bitcoin wif private key (p2sh(p2wpkh)), compressed | cryptocurrency wallet
28506 | bitcoin wif private key (p2sh(p2wpkh)), uncompressed | cryptocurrency wallet
11300 | bitcoin/litecoin wallet.dat | cryptocurrency wallet
16600 | electrum wallet (salt-type 1-3) | cryptocurrency wallet
21700 | electrum wallet (salt-type 4) | cryptocurrency wallet
21800 | electrum wallet (salt-type 5) | cryptocurrency wallet
12700 | blockchain, my wallet | cryptocurrency wallet
15200 | blockchain, my wallet, v2 | cryptocurrency wallet
18800 | blockchain, my wallet, second password (sha256) | cryptocurrency wallet
25500 | stargazer stellar wallet xlm | cryptocurrency wallet
16300 | ethereum pre-sale wallet, pbkdf2-hmac-sha256 | cryptocurrency wallet
15600 | ethereum wallet, pbkdf2-hmac-sha256 | cryptocurrency wallet
15700 | ethereum wallet, scrypt | cryptocurrency wallet
22500 | multibit classic .key (md5) | cryptocurrency wallet
27700 | multibit classic .wallet (scrypt) | cryptocurrency wallet
22700 | multibit hd (scrypt) | cryptocurrency wallet
28200 | exodus desktop wallet (scrypt) | cryptocurrency wallet
3.5. 工作负载配置
# | performance | runtime | power consumption | desktop impact
===+=============+=========+===================+=================
1 | low | 2 ms | low | minimal
2 | default | 12 ms | economic | noticeable
3 | high | 96 ms | high | unresponsive
4 | nightmare | 480 ms | insane | headless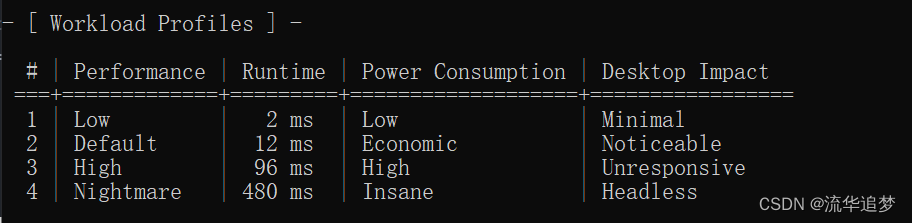
四. hashcat 的常见使用案例
hashcat 支持多种平台、多种 hash 密文的破解。
4.1. rar 文件解密
1. 通过 john the ripper 获取文件的密文值
把要获取密文的 rar 文件拷贝到 john-1.9.0-jumbo-1-win64 的 run 目录下。
// 通过命令获取密文值
rar2john.exe python_glxtym.rar
// 获取到的密文为:
$rar3$*1*a55d3f6aa676f7b3*9b850ef5*16*8*1*5d3dbaafa35e973c49a01dfcdcebfc4e*33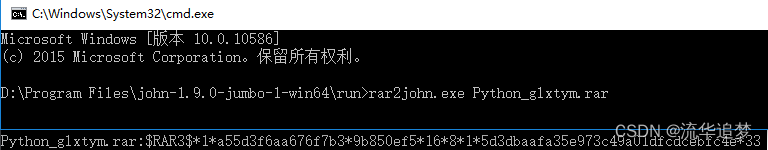
2. 通过 hashcat 获取明文密码
hashcat.exe -m 23800 -a 3 $rar3$*1*a55d3f6aa676f7b3*9b850ef5*16*8*1*5d3dbaafa35e973c49a01dfcdcebfc4e*33 -o password.txt
破解成功会在目录下生成 password.txt 文件。
4.2. md5 密文解密
4.2.1. 字典模式破解
需要提前准备好字典文件 password.dict。
hashcat -m 0 -a 0 d3786ec2413a8cd9413bfcb24be95a73 password.dict --force
hashcat -m 0 -a 0 d3786ec2413a8cd9413bfcb24be95a73 password.dict --force --show
hashcat -m 0 -a 0 d3786ec2413a8cd9413bfcb24be95a73 password.dict -o result.txt –force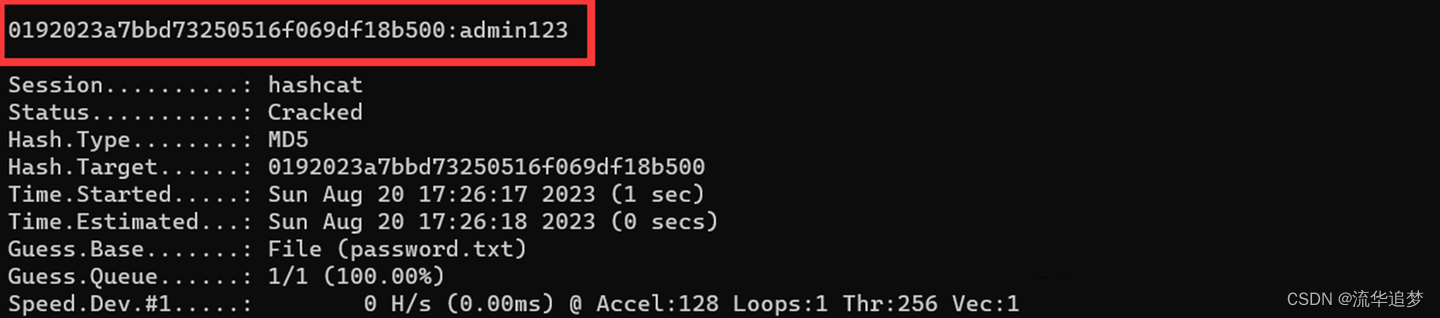
4.2.2. 掩码模式破解
hashcat -m 0 -a 3 63a9f0ea7bb98050796b649e85481845 ?l?l?l?l --force -o -w 3 -s
hashcat -m 0 -a 3 63a9f0ea7bb98050796b649e85481845 ?l?l?l?l --force -o -w 3 -s --show
hashcat -m 0 -a 3 63a9f0ea7bb98050796b649e85481845 ?l?l?l?l -o result.txt --force --show -o -w 3 -s4.2.3. 使用字典+掩码进行破解
hashcat -m 0 -a 6 1844156d4166d94387f1a4ad031ca5fa password.dict ?d?d --force -o
hashcat -m 0 -a 6 1844156d4166d94387f1a4ad031ca5fa password.dict ?d?d --force --show –o
hashcat -m 0 -a 6 1844156d4166d94387f1a4ad031ca5fa password.dict ?d?d -o result.txt --force –show –o
4.2.4. 使用掩码+字典进行破解
hashcat -m 0 -a 7 f8def8bcecb2e7925a2b42d60d202deb ?d?d password.dict --force -o
hashcat -m 0 -a 7 f8def8bcecb2e7925a2b42d60d202deb ?d?d password.dict --force -o --show
hashcat -m 0 -a 7 f8def8bcecb2e7925a2b42d60d202deb ?d?d password.dict -o result.txt --force –o
如果已经破解过,加参数:--show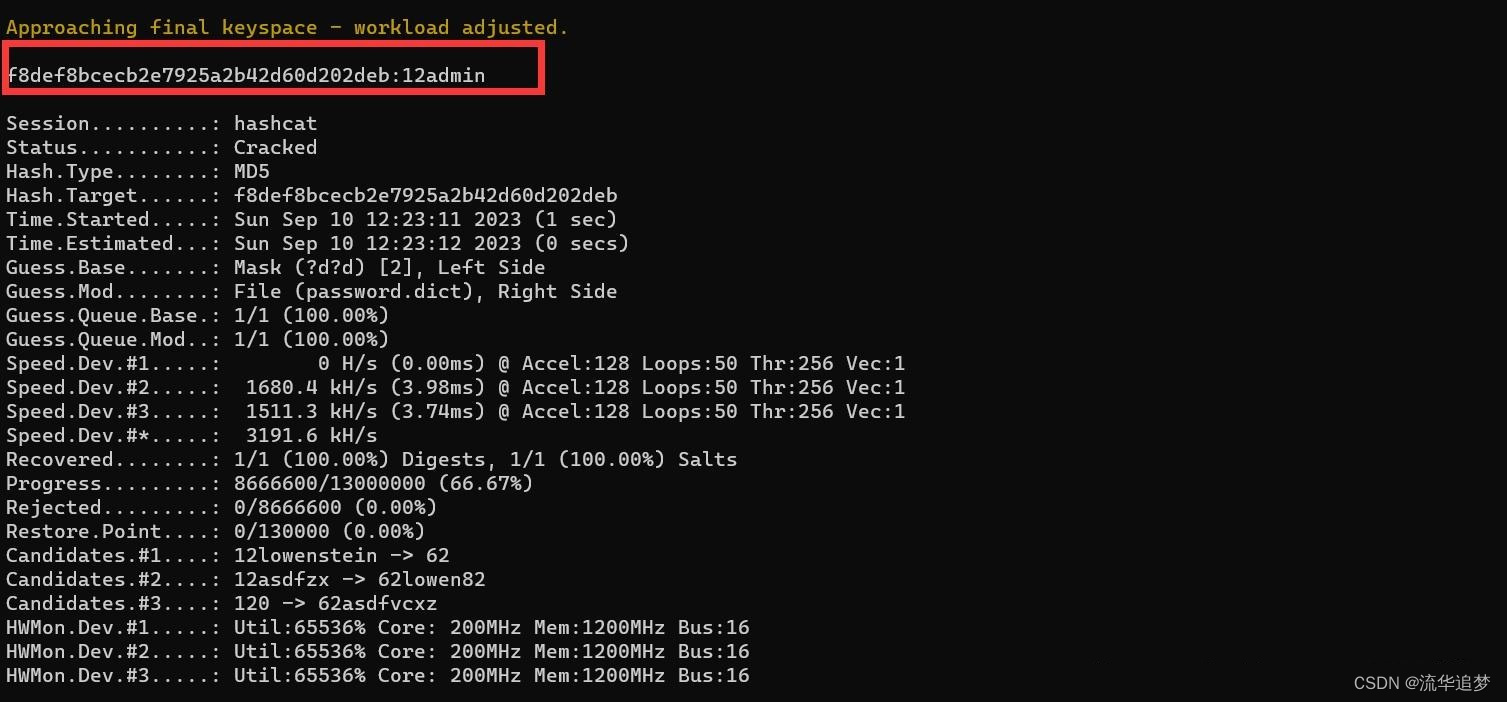
4.2.5. 批量字典破解
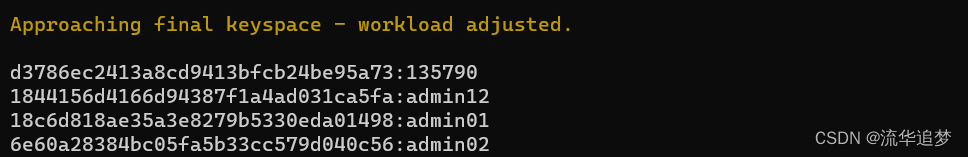
hashcat -m 0 -a 0 jiami.txt password.dict --force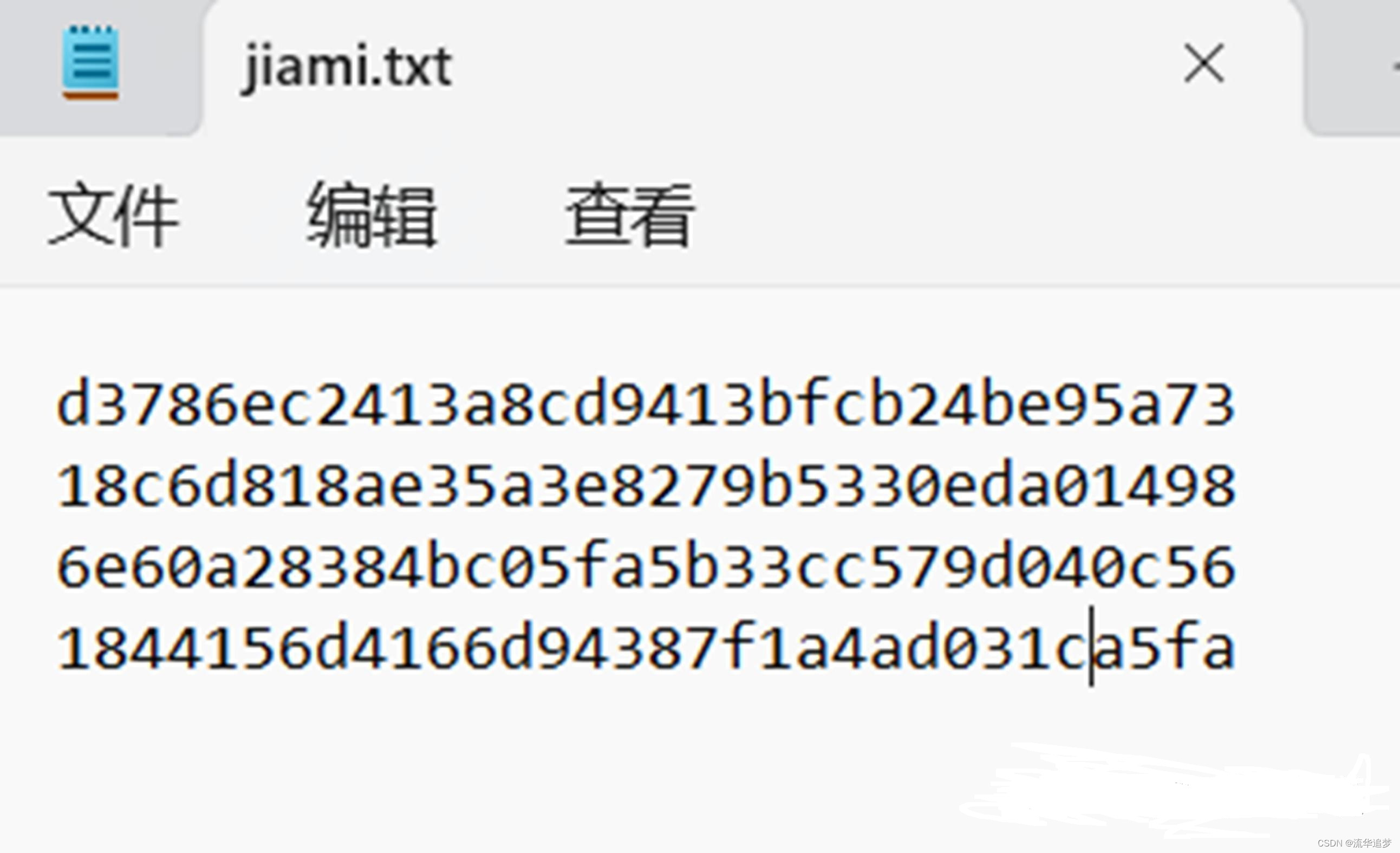
破解后的结果文件如下:
4.3. sha512 密文解密
密文:$6$zje1waos$eh24jfr5n67149ybcdwwsfxme5cyloxmmjxnf2uinbvym8vwc0bmjvaoxify/0zujitrpphhkcgdiqjxt10ev0首先使用hashidentifier工具识别该密文的类型:
- 识别到的 hash 类型为 sha512 crypt
- 对应 hashcat 的类型编号为 1800
再使用 hashcat 使用字典破解模式进行破解,提前准备字典文件:
hashcat -m 1800 -a 0 $6$zje1waos$eh24jfr5n67149ybcdwwsfxme5cyloxmmjxnf2uinbvym8vwc0bmjvaoxify/0zujitrpphhkcgdiqjxt10ev0 password.dict --force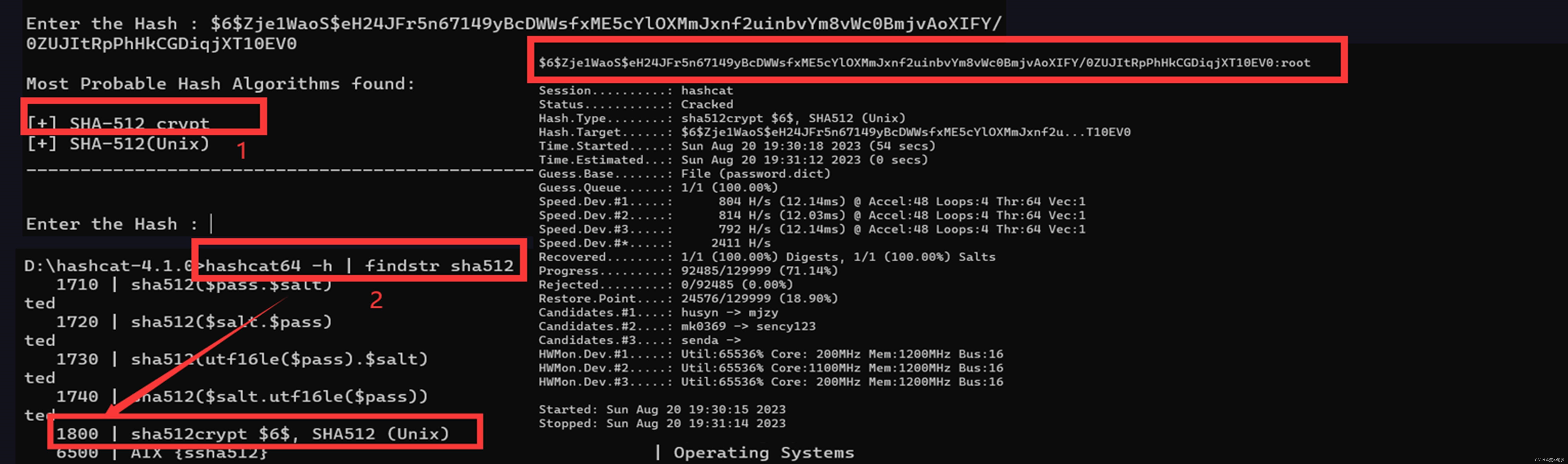
如果破解时间太长,我们可以按 s 键查看破解进度,p 键暂停,r 键继续破解,q 键退出破解。
4.4. windows 密码解密
windows 系统通常使用两种方法对用户的明文密码进行加密处理,分别是:
- lm hash :对应 hashcat 中的类型编号为 3000
- ntlm hash:对应 hashcat 中的类型编号为 1000
lm hash 是一种 windows 系统身份认证协议,在 windows 7 或 windows 2008 之前的系统使用,之后的系统默认禁用了 lm hash 协议认证,使用 ntlm hash 的方式。
对 windows 密码进行破解建议使用高版本的 hashcat 软件,4.1.0及以下的版本会因各种问题提前终止破解而导致破解失败,本案例建议使用最新的 hashcat-6.2.6 版本。
1. root 字符串对应的 lm hash 密文为:d480ea9533c500d4aad3b435b51404ee
hashcat -m 3000 -a 0 d480ea9533c500d4aad3b435b51404ee password.dict --force 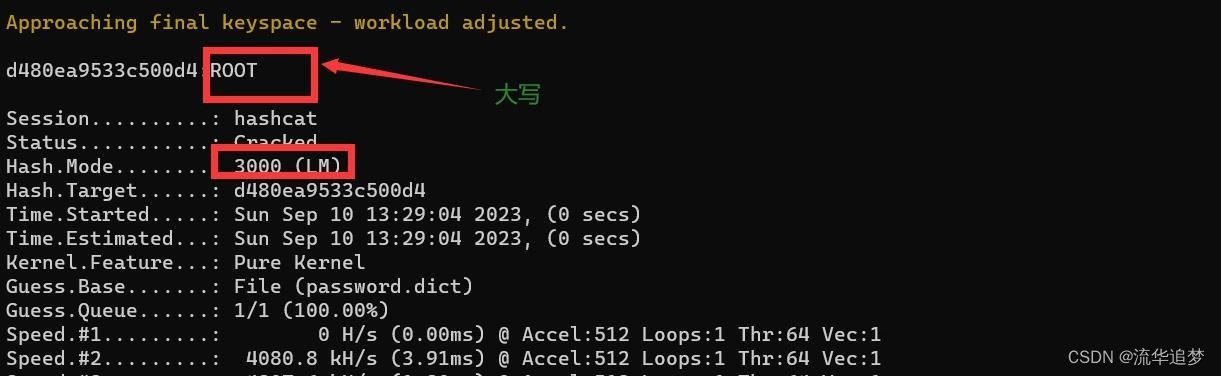
2. root 字符串对应的 ntlm hash 密文为:329153f560eb329c0e1deea55e88a1e9
hashcat -m 1000 -a 0 329153f560eb329c0e1deea55e88a1e9 password.dict --force -o -w 3 -s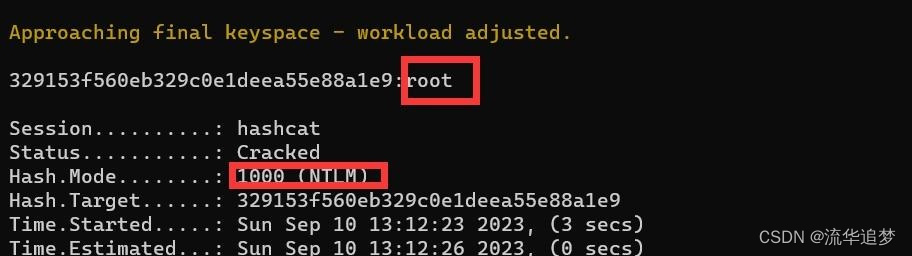
4.5. mysql 密码解密
hashcat -a 3 -m 300 --force 6bb4837eb74329105ee4568dda7dc67ed2ca2ad9 ?d?d?d?d?d?d4.6. office 密码解密
获取 office 的 hash 值:python office2john.py 11.docx
结果:
11.docx:$office$*2013*100000*256*16*e4a3eb62e8d3576f861f9eded75e0525*9eeb35f0849a7800d48113440b4bbb9c*577f8d8b2e1c5f60fed76e62327b38d28f25230f6c7dfd66588d9ca8097aabb9破解密码:
hashcat -a 3 -m 9600 $office$*2013*100000*256*16*e4a3eb62e8d3576f861f9eded75e0525*9eeb35f0849a7800d48113440b4bbb9c*577f8d8b2e1c5f60fed76e62327b38d28f25230f6c7dfd66588d9ca8097aabb9 --force ?d?d?d?d?d?d4.7. 在线解密
sha 256 在线解密:http://www.ttmd5.com/hash.php?type=09
md5 在线解密:https://www.somd5.com/
end




发表评论