前提条件:数据库密码忘记了,但是在navicat连接过且目前能连接上的状态!
1.导出数据库连接 connections.ncx 文件
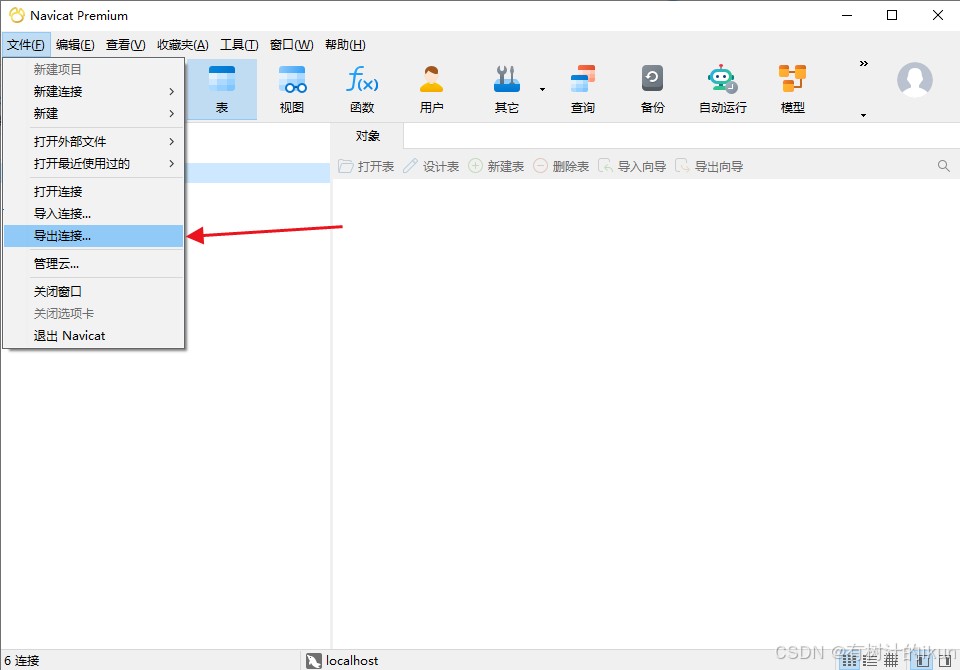
选择你要导出密码的数据库连接,切记要勾上导出密码
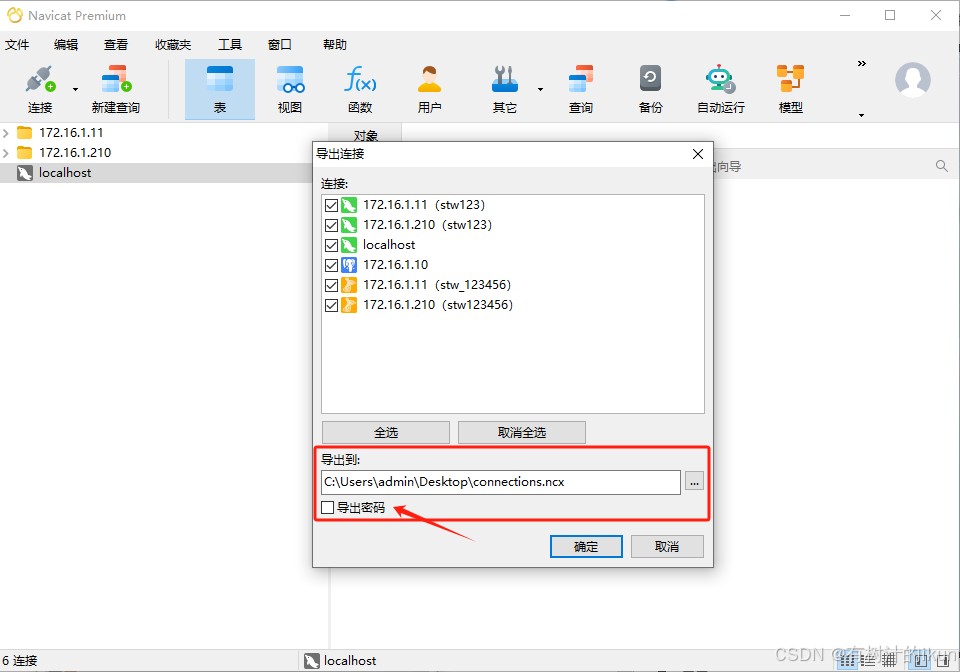
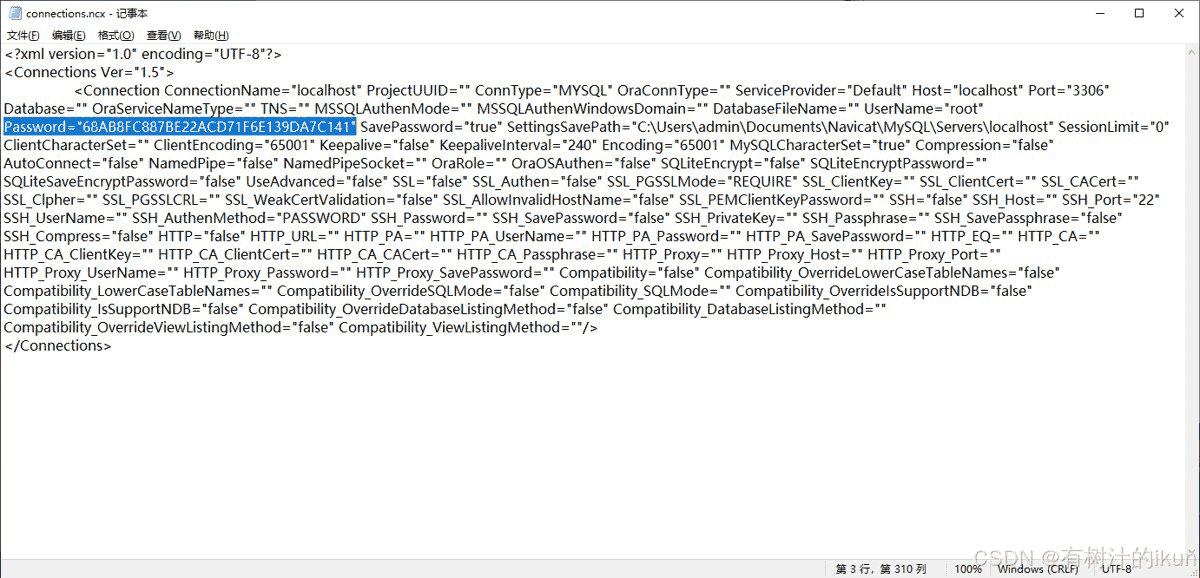
2.使用文本编辑工具打开导出的connections.ncx 文件
找到password="",将双引号中间的密码复制出来使用下面的java程序或php程序进行解密!
3.解密 - 使用java程序进行解密
java在线运行环境:代码在线运行 - 在线工具,进入选择java,将以下代码复制到在线运行环境中
选择你自己的navicat版本,把代码中的密码替换为你自己connections.ncx文件中的密码,然后执行即可输出(实测navicat16可以成功解密)
import javax.crypto.cipher;
import javax.crypto.spec.ivparameterspec;
import javax.crypto.spec.secretkeyspec;
import java.nio.charset.standardcharsets;
import java.security.messagedigest;
import java.util.arrays;
public class navicatpassword {
public static void main(string[] args) throws exception {
navicatpassword navicatpassword = new navicatpassword();
// navicat 11及以前的版本
// string decode = navicatpassword.decrypt("你的密码", 11);
// navicat 12及以后的版本
string decode = navicatpassword.decrypt("你的密码", 12);
system.out.println(decode);
}
private static final string aes_key = "libcckeylibcckey";
private static final string aes_iv = "libcciv libcciv ";
private static final string blow_key = "3dc5ca39";
private static final string blow_iv = "d9c7c3c8870d64bd";
public static string encrypt(string plaintext, int version) throws exception {
switch (version) {
case 11:
return encrypteleven(plaintext);
case 12:
return encrypttwelve(plaintext);
default:
throw new illegalargumentexception("unsupported version");
}
}
public static string decrypt(string ciphertext, int version) throws exception {
switch (version) {
case 11:
return decrypteleven(ciphertext);
case 12:
return decrypttwelve(ciphertext);
default:
throw new illegalargumentexception("unsupported version");
}
}
private static string encrypteleven(string plaintext) throws exception {
byte[] iv = hexstringtobytearray(blow_iv);
byte[] key = hashtobytes(blow_key);
int round = plaintext.length() / 8;
int leftlength = plaintext.length() % 8;
stringbuilder result = new stringbuilder();
byte[] currentvector = iv.clone();
cipher cipher = cipher.getinstance("blowfish/ecb/nopadding");
secretkeyspec secretkeyspec = new secretkeyspec(key, "blowfish");
cipher.init(cipher.encrypt_mode, secretkeyspec);
for (int i = 0; i < round; i++) {
byte[] block = xorbytes(plaintext.substring(i * 8, (i + 1) * 8).getbytes(), currentvector);
byte[] temp = cipher.dofinal(block);
currentvector = xorbytes(currentvector, temp);
result.append(bytestohex(temp));
}
if (leftlength > 0) {
currentvector = cipher.dofinal(currentvector);
byte[] block = xorbytes(plaintext.substring(round * 8).getbytes(), currentvector);
result.append(bytestohex(block));
}
return result.tostring().touppercase();
}
private static string encrypttwelve(string plaintext) throws exception {
byte[] iv = aes_iv.getbytes();
byte[] key = aes_key.getbytes();
cipher cipher = cipher.getinstance("aes/cbc/nopadding");
secretkeyspec secretkeyspec = new secretkeyspec(key, "aes");
ivparameterspec ivparameterspec = new ivparameterspec(iv);
cipher.init(cipher.encrypt_mode, secretkeyspec, ivparameterspec);
byte[] result = cipher.dofinal(plaintext.getbytes());
return bytestohex(result).touppercase();
}
private static string decrypteleven(string ciphertext) throws exception {
byte[] iv = hexstringtobytearray(blow_iv);
byte[] key = hashtobytes(blow_key);
byte[] encrypted = hexstringtobytearray(ciphertext.tolowercase());
int round = encrypted.length / 8;
int leftlength = encrypted.length % 8;
stringbuilder result = new stringbuilder();
byte[] currentvector = iv.clone();
cipher cipher = cipher.getinstance("blowfish/ecb/nopadding");
secretkeyspec secretkeyspec = new secretkeyspec(key, "blowfish");
cipher.init(cipher.decrypt_mode, secretkeyspec);
for (int i = 0; i < round; i++) {
byte[] block = arrays.copyofrange(encrypted, i * 8, (i + 1) * 8);
byte[] temp = xorbytes(cipher.dofinal(block), currentvector);
currentvector = xorbytes(currentvector, block);
result.append(new string(temp));
}
if (leftlength > 0) {
currentvector = cipher.dofinal(currentvector);
byte[] block = arrays.copyofrange(encrypted, round * 8, round * 8 + leftlength);
result.append(new string(xorbytes(block, currentvector), standardcharsets.utf_8));
}
return result.tostring();
}
private static string decrypttwelve(string ciphertext) throws exception {
byte[] iv = aes_iv.getbytes();
byte[] key = aes_key.getbytes();
byte[] encrypted = hexstringtobytearray(ciphertext.tolowercase());
cipher cipher = cipher.getinstance("aes/cbc/nopadding");
secretkeyspec secretkeyspec = new secretkeyspec(key, "aes");
ivparameterspec ivparameterspec = new ivparameterspec(iv);
cipher.init(cipher.decrypt_mode, secretkeyspec, ivparameterspec);
byte[] result = cipher.dofinal(encrypted);
return new string(result);
}
private static byte[] xorbytes(byte[] bytes1, byte[] bytes2) {
byte[] result = new byte[bytes1.length];
for (int i = 0; i < bytes1.length; i++) {
result[i] = (byte) (bytes1[i] ^ bytes2[i]);
}
return result;
}
private static byte[] hexstringtobytearray(string s) {
int len = s.length();
byte[] data = new byte[len / 2];
for (int i = 0; i < len; i += 2) {
data[i / 2] = (byte) ((character.digit(s.charat(i), 16) << 4) + character.digit(s.charat(i + 1), 16));
}
return data;
}
private static byte[] hashtobytes(string s) throws exception {
return messagedigest.getinstance("sha-1").digest(s.getbytes());
}
private static string bytestohex(byte[] bytes) {
stringbuilder result = new stringbuilder();
for (byte b : bytes) {
result.append(string.format("%02x", b));
}
return result.tostring();
}
}3.解密 - 使用php程序进行解密
php在线运行环境:代码在线运行 - 在线工具,进入后选择php,将以下代码复制到在线运行环境中
选择你自己的navicat版本,把代码中的密码替换为你自己connections.ncx文件中的密码,然后执行即可输出(实测navicat16可以成功解密)
<?php
// navicat 11及以前的版本
//$navicatpassword = new navicatpassword(11);
// navicat 12及以后的版本
$navicatpassword = new navicatpassword(12);
$decode = $navicatpassword->decrypt('68ab8fc887be22acd71f6e139da7c141');
echo $decode . "\n";
class navicatpassword
{
protected $version = 0;
protected $aeskey = 'libcckeylibcckey';
protected $aesiv = 'libcciv libcciv ';
protected $blowstring = '3dc5ca39';
protected $blowkey = null;
protected $blowiv = null;
public function __construct($version = 12)
{
$this->version = $version;
$this->blowkey = sha1('3dc5ca39', true);
$this->blowiv = hex2bin('d9c7c3c8870d64bd');
}
public function encrypt($string)
{
$result = false;
switch ($this->version) {
case 11:
$result = $this->encrypteleven($string);
break;
case 12:
$result = $this->encrypttwelve($string);
break;
default:
break;
}
return $result;
}
protected function encrypteleven($string)
{
$round = intval(floor(strlen($string) / 8));
$leftlength = strlen($string) % 8;
$result = '';
$currentvector = $this->blowiv;
for ($i = 0; $i < $round; $i++) {
$temp = $this->encryptblock($this->xorbytes(substr($string, 8 * $i, 8), $currentvector));
$currentvector = $this->xorbytes($currentvector, $temp);
$result .= $temp;
}
if ($leftlength) {
$currentvector = $this->encryptblock($currentvector);
$result .= $this->xorbytes(substr($string, 8 * $i, $leftlength), $currentvector);
}
return strtoupper(bin2hex($result));
}
protected function encryptblock($block)
{
return openssl_encrypt($block, 'bf-ecb', $this->blowkey, openssl_raw_data | openssl_no_padding);
}
protected function decryptblock($block)
{
return openssl_decrypt($block, 'bf-ecb', $this->blowkey, openssl_raw_data | openssl_no_padding);
}
protected function xorbytes($str1, $str2)
{
$result = '';
for ($i = 0; $i < strlen($str1); $i++) {
$result .= chr(ord($str1[$i]) ^ ord($str2[$i]));
}
return $result;
}
protected function encrypttwelve($string)
{
$result = openssl_encrypt($string, 'aes-128-cbc', $this->aeskey, openssl_raw_data, $this->aesiv);
return strtoupper(bin2hex($result));
}
public function decrypt($string)
{
$result = false;
switch ($this->version) {
case 11:
$result = $this->decrypteleven($string);
break;
case 12:
$result = $this->decrypttwelve($string);
break;
default:
break;
}
return $result;
}
protected function decrypteleven($upperstring)
{
$string = hex2bin(strtolower($upperstring));
$round = intval(floor(strlen($string) / 8));
$leftlength = strlen($string) % 8;
$result = '';
$currentvector = $this->blowiv;
for ($i = 0; $i < $round; $i++) {
$encryptedblock = substr($string, 8 * $i, 8);
$temp = $this->xorbytes($this->decryptblock($encryptedblock), $currentvector);
$currentvector = $this->xorbytes($currentvector, $encryptedblock);
$result .= $temp;
}
if ($leftlength) {
$currentvector = $this->encryptblock($currentvector);
$result .= $this->xorbytes(substr($string, 8 * $i, $leftlength), $currentvector);
}
return $result;
}
protected function decrypttwelve($upperstring)
{
$string = hex2bin(strtolower($upperstring));
return openssl_decrypt($string, 'aes-128-cbc', $this->aeskey, openssl_raw_data, $this->aesiv);
}
}
总结
到此这篇关于如何查看navicat已保存的数据库连接密码的文章就介绍到这了,更多相关查看navicat已保存连接密码内容请搜索代码网以前的文章或继续浏览下面的相关文章希望大家以后多多支持代码网!



发表评论