漏洞描述
cors 不安全配置漏洞指的是在跨域资源共享过程中,由于资源服务器的响应头 access-control-allow-origin 配置不当导致本应该受限访问的请求网站可以绕过访问控制策略读取资源服务器的数据,造成用户隐私泄露,信息窃取甚至账户劫持的危害。
漏洞细节
经过对以下目标进行扫描测试:https://xxx.com/external/
发现存在该漏洞。
发现 access-control-allow-origin 的值为 https://xxx.com.qa5bnet.cn
漏洞探测过程的请求流为
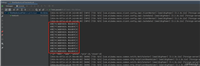
第 1 个请求为
get /external/ http/1.1 host: xxx.com user-agent: mozilla/5.0 (windows nt 10.0; wow64) applewebkit/537.36 (khtml, like gecko) chrome/71.0.3578.98 safari/537.36 accept: text/html,application/xhtml+xml,application/xml;q=0.9,image/avif,image/webp,image/apng,*/*;q=0.8,application/signed-exchange;v=b3;q=0.9 accept-language: en origin: https://xxx.com.qa5bnet.cn sec-fetch-dest: document sec-fetch-mode: navigate sec-fetch-site: none sec-fetch-user: ?1 upgrade-insecure-requests: 1 accept-encoding: gzip
第 1 个响应为
http/1.1 401 access-control-allow-methods: get,post,options,put,delete access-control-allow-origin: https://xxx.com.qa5bnet.cn connection: keep-alive content-length: 0 date: mon, 13 nov 2023 02:07:00 gmt www-authenticate: basic realm="application"
漏洞修复
set $flag 0;
if ($http_origin = ''){
set $flag "${flag}1";
}
if ($http_origin !~* ^(http|https)://test\.test\.com$){
set $flag "${flag}1";
}
if ($flag = "01"){
return 403;
}
if ($http_origin ~* ^(http|https)://test\.test\.com$) {
add_header access-control-allow-origin $http_origin;
add_header access-control-allow-methods get,post;
add_header access-control-allow-credentials true;
add_header access-control-allow-headers dnt,keep-alive,user-agent,if-modified-since,cache-control,content-type;
}
具体配置如下:
server {
listen 80;
server_name test.test.com;
location / {
set $flag 0;
if ($http_origin = ''){
set $flag "${flag}1";
}
if ($http_origin !~* ^(http|https)://test\.test\.com$){
set $flag "${flag}1";
}
if ($flag = "01"){
return 403;
}
if ($http_origin ~* ^(http|https)://test\.test\.com$) {
add_header access-control-allow-origin $http_origin;
add_header access-control-allow-methods get,post;
add_header access-control-allow-credentials true;
add_header access-control-allow-headers dnt,keep-alive,user-agent,if-modified-since,cache-control,content-type;
}
#将ip和端口改为dataease服务器的访问地址和端口
proxy_pass http://192.168.110.251:81/;
server_name_in_redirect off;
# websocket 代理
proxy_http_version 1.1;
proxy_set_header upgrade $http_upgrade;
proxy_set_header connection "upgrade";
proxy_set_header host $host:$server_port;
proxy_set_header x-real-ip $remote_addr;
proxy_set_header x-forwarded-for $proxy_add_x_forwarded_for;
proxy_set_header x-forwarded-proto $scheme;
}
}到此这篇关于nginx修复cors漏洞的实现方法的文章就介绍到这了,更多相关nginx修复cors漏洞内容请搜索代码网以前的文章或继续浏览下面的相关文章希望大家以后多多支持代码网!





发表评论