openssh 官方发布安全更新,修复了其 openssh 存在的远程代码执行漏洞,漏洞编号cve-2024-6387。可导致未经身份验证的远程攻击者执行任意代码等危害。
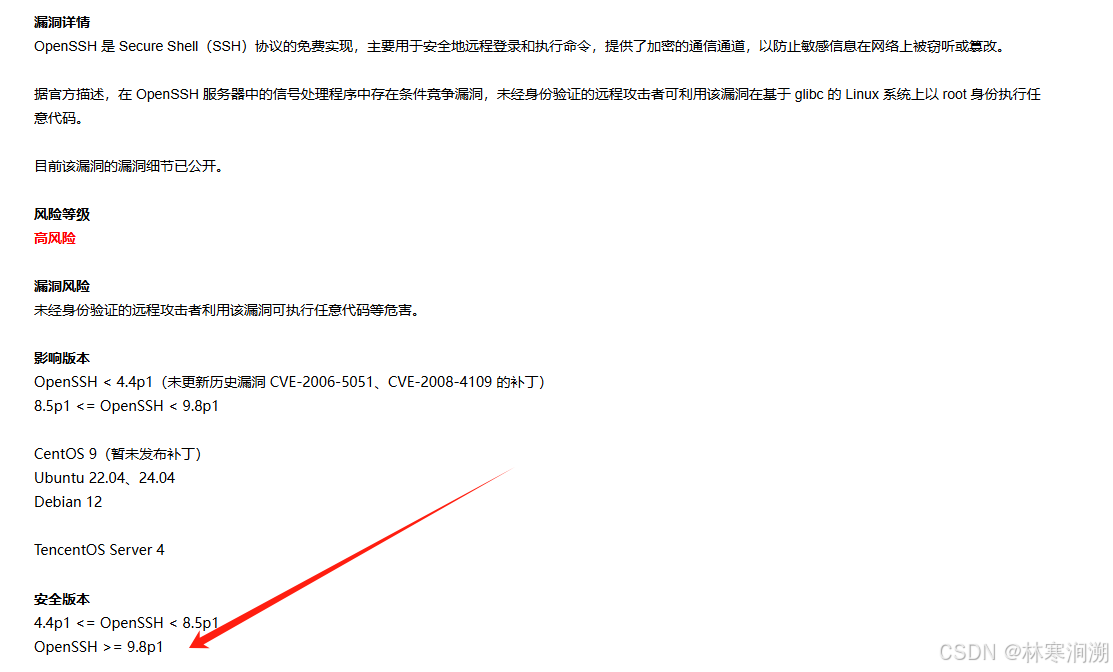
漏洞详情见上图和相关连接 https://nvd.nist.gov/vuln/detail/cve-2024-6387
本文在centos(x86) 和 麒麟sp3(arm)系统上均验证成功
准备工作
下载源码包和依赖,相关连接如下
openssh-9.8p1.tar.gz
x11-ssh-askpass-1.2.4.1.tar.gz
一、安装所需依赖包
#配置rpm构建环境
yum install rpmdevtools
二、rpm制作
rpmdev-setuptree
tar -xzvf openssh-9.8p1.tar.gz
cp openssh-9.8p1/contrib/redhat/openssh.spec /root/rpmbuild/specs/
cp openssh-9.8p1.tar.gz /root/rpmbuild/sources/
cp x11-ssh-askpass-1.2.4.1.tar.gz /root/rpmbuild/sources/
[root@localhost ~]# tree rpmbuild/
rpmbuild/
├── build
├── rpms
├── sources
│ ├── openssh-9.8p1.tar.gz
│ └── x11-ssh-askpass-1.2.4.1.tar.gz
├── specs
│ └── openssh.spec
└── srpms
# 编译并生成rpm
cd ~/rpmbuild/specs
rpmbuild -ba openssh.spec
# 编译完成后的rpm包生成在rpmbuild/rpms目录中
[root@localhost rpmbuild]# ls rpms/x86_64/
openssh-9.8p1-1.el7.x86_64.rpm
openssh-askpass-9.8p1-1.el7.x86_64.rpm
openssh-askpass-gnome-9.8p1-1.el7.x86_64.rpm
openssh-clients-9.8p1-1.el7.x86_64.rpm
openssh-debuginfo-9.8p1-1.el7.x86_64.rpm
openssh-server-9.8p1-1.el7.x86_64.rpm
三、备份ssh配置
mkdir -p /backup/ssh_backup/pam.d
cp /etc/pam.d/sshd /backup/ssh_backup/pam.d/
cp -r /etc/ssh /backup/ssh_backup/
四、安装openssh,注意离线安装可能缺少依赖,需要手动解决
#在线环境
yum localinstall open*.rpm
#离线环境
rpm -ivh --force --nodeps open*.rpm
报错1 /usr/include/x11/shell.h:51:26: 致命错误:x11/sm/smlib.h:没有那个文件或目录
# 缺少依赖,去yum地址找包或者yum install 解决
yum install libsm-devel
报错2 /usr/include/x11/shell.h:51:26: 致命错误:x11/ice/icelib.h:没有那个文件或目录
# 缺少依赖,去yum地址找包或者yum install 解决
yum install libice-devel
五、还原配置文件
cp /backup/ssh_backup/pam.d/sshd /etc/pam.d/
chmod 400 /etc/ssh/ssh_host_*
六、查看升级状态
ssh -v
openssh_9.8p1, without openssl


发表评论