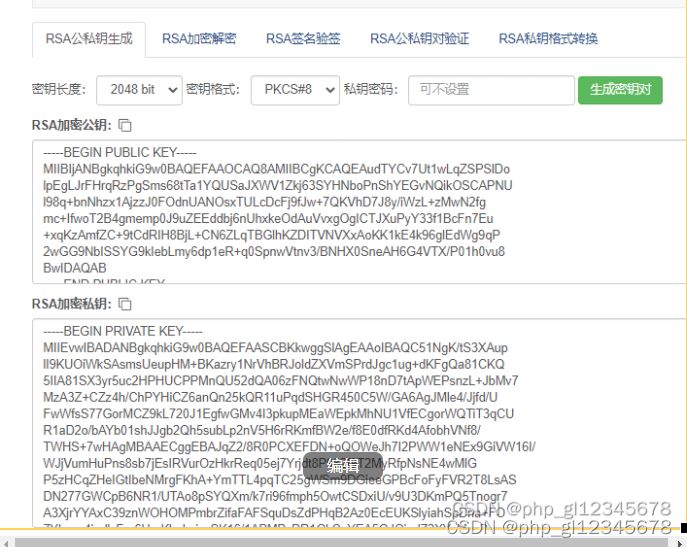
第一步、生成公私钥
密钥长度:
- rsa 密钥通常有不同的长度,通常以位数来表示,如 1024 位、2048 位等。一般来说,密钥长度越长,加密强度越高,但同时也会增加加密和解密的计算复杂度。一般推荐使用 2048 位或更长的 rsa 密钥来确保较高的安全性。
密钥格式:
- openssl 中的私钥通常采用 pem 格式(privacy-enhanced mail,即隐私增强邮件)存储。pem 格式的密钥是经过 base64 编码的文本字符串,通常以
-----begin private key-----开头,以-----end private key-----结尾。 - 另外,私钥也可以存储在 pkcs#12 格式的证书文件中,通常以
.p12或.pfx结尾。这些文件通常包含私钥、公钥和证书链等信息。
第二步、三种方式读取rsa密钥
第1种:公私钥弄成一行,必须一行没有空格和换行
$publickey = 'mfwwdqyjkozihvcnaqebbqadswawsajbakz1mktymrogknhip1xay4aiyt5r0bscczndaoncrmfz4kbgripnhxealr5lfbnmkw7k6i+2dsfpsezootvqtpucaweaaq=='; $privatekey = 'miibvaibadanbgkqhkig9w0baqefaascat4wgge6ageaakeapnwyppkzggyqcei/xedlhqlk3mvqgxwjmcmcickswvniqeaui80ferouvmv8gcwrdutql7z2wu9irmiho+q09qidaqabakbunx3nghxyjppsfn++7iytd+i7+agfy/0xwyb3rpeigggfemjcrfaeq5sc2vunxsreoy5gbusqmfxh//cym18naiea1z1czx/q9cbijfpwp1a+k5cvfdxdcfbi/aqgakvs0/cciqdf+2fr23aobslcoc4s0yax94abgxcntyurqztxybsrcwigmw86zct87tx2oaq1xxk6vc68zqn6fbzee7wu1fa1pakcielmojp3qfac/aalj+diwlhlqwgjwl3674cu9bfui2bdaiea0ckjpf8x7kanccopeqc93psbiztuml322lofdv1lw/k=';
转化能使用的密钥资源
- 如果私钥不是资源类型,则将私钥进行处理,将其转换为 pem 格式。这里使用
chunk_split函数将私钥按照每行64个字符的长度进行分割,并在适当的位置插入换行符\n。 - 在拼接完整的 pem 格式私钥之后,再使用
openssl_pkey_get_private函数将 pem 格式的私钥转换为 openssl 的私钥资源
$pem = chunk_split($privatekey, 64, "\n"); $pem = "-----begin private key-----\n" . $pem. "-----end private key-----\n"; $pem2 = chunk_split($publickey, 64, "\n"); $pem2 = "-----begin public key-----\n" . $pem2 . "-----end public key-----\n";
第2种:直接复制生成公私钥
$publickeystring = "-----begin public key----- miibijanbgkqhkig9w0baqefaaocaq8amiibcgkcaqeap1ffl+kueedbltzqrku+ 8oq9izsuroxhmnwrxa1xmgtlbevchqnljujqwgulelyk7i78cgczwcyge2svj9oi tbzgn02fwzncb3bhpv6oflitvqyczofaftwb+ttkuomopck/bgqve7hc6+74s/3x q4tm1jvbnpysy11++dljeq8kaa3pnjwoftxer3gvegmfhi5xuttaba5zoianfsfr 0fgzvgbmrpqoior6mlsxxbmo4k2pmzb7yjyyr7zrc28doejcj5xnxkq4xpijzo8/ g79163dp0y9m7cdn4nfrddbsfehy6n+hkps6hsvf1z1ztqtlfk0mre/echubdcuh +qidaqab -----end public key-----"; $privatekeystring = "-----begin private key----- miievqibadanbgkqhkig9w0baqefaascbkcwggsjageaaoibaqcnv98v6rqr50et pncspt7yir0hljsujggadatdrvcwa2vt5uida2wo6oraa4sqvktulvxwzzpaliyt zjwp2gi0hmaftz9zk0jvdsc+/qh+wjo+phxk4vovnyh61mq46aikkt9ubbv7sclr 7viz/ffdi0zwnvs09hjjxx74mumrdwpodek0ncgvperhczuscz+glnfrnnofrlk4 ho1+wwvr8bo8zuzgmqgiivoyvlfdsw7itakzmhtglhivvnelbwoh4kkpledesrhc 8gnojz+dv3xrd2ntl2btwofg19en0gwv4flqf6eqmzqfjv/xpvm1c2v+tszet8ry g5sny4f5agmbaaecggead5rfiv/emxs4yvvzlei7og1s+ojqtmtdiefazuzyqufj sf+w/lekkb1ts7ppxd+gficvct2otk1euu4mo7gxkniuyf3ba+tli3dqt0sanxum fzhykoqsv4zt7wxtrfbm2xalxsmie7m0xx6ziur6qtv56ixgmp1dbuow8uklqlv2 p3vdckfjt2pwylqm2yzuoc3+ajfqpjus/dpyirgtld8rlofcrpgm2naewxycaeyi cphgzyccabwyxzokfowifpm53zdbdzpupzkjs29rygjiz7st6sdceggoz+ayeuwa bb1rkzjkbelrxbuizhlsbrbo12ye8gz+vpzgsy1cvqkbgqdwhjj/7yur/m+d9yj0 9s14tk5kx3ex2cl46it8fmjektk1ihgyb6dmk10pdrv2glj3zlfwyeu82p9zgswh f34mu3o67medj3ojp+/qhyvem4wokw1973v8geqhqtvr7ypyvc/croyn49fkbkfc sf7scw7eatobxtwmdjyaa+jdpwkbgqdie3dhyzx1yahehktygvw9oaddykzyzv2j ko8rkaws0oxy6yi2j1ncrq3n5ro7pamcesrabgaps7n2gazlnfrtg/dch87m0kyz aewo1dvi3xviajipmzxbeu2xp1o40ooxzxehp3vzuu2ydyr6yp3y2wcclmgf3vuz o1ugk2a+xwkbgczzbpcaujldarvqwos4vr8ivi/a7dtdn/uxfxz8ovq2mhdlo5pt hebr5cnuu0wz56dd2xzo71+nvxn69b9pmz0+vm/oyjcdmhdmq3xwcngpga/lkxqz iqhf1c5zrsosutqpyiljhhainj4ipyqmohd+2omjbvypg2a4d5nnlk1paogbaixh ognc3heqzgvh0f+ml82edbd5dosa1es7klj7j2ekht7lvqj9q2imhkaqkzqarpsj 26fvt4iq36qzxltyc8fxllrjlfcuhuxi5ane53jgw33zpjg2nndyoeyavzqr8l2u obkiehnhpjc5xryr1vvbvevbgciwvbodfa7nckrpaogak2oiq5slu5ofab4qcn6v vherc8jxgzwl/o2z/4t0ox1x6nwddal87lcyq6ab3dqmgemtjdd2z9ddn2m9opto yunvlxynicqgsnyucwy6q1yy1fovhiujf8rkq4utseq8gsrf8hf3ajhmzha1r5b7 y5mupuhis6ckwmtf+paxagq= -----end private key-----";
openssl_pkey_get_public和openssl_pkey_get_private是php openssl扩展提供的两个函数。
openssl_pkey_get_public函数用于获取公钥,它可以从一个证书文件或pem格式的公钥字符串中提取公钥信息,并返回一个公钥资源
$publickeyresource = openssl_pkey_get_public($publickeystring); $privatekeyresource = openssl_pkey_get_private($privatekeystring);
第3种;复制密钥存储为.pem文件后缀
$publickeystring = file_get_contents('public.pem');
$privatekeystring = file_get_contents('private.pem');
$publickeyresource = openssl_pkey_get_public($publickeystring);
$privatekeyresource = openssl_pkey_get_private($privatekeystring);第三步、rsa加解密
rsa加密
公钥加密 openssl_public_encrypt => 私钥解密 openssl_private_decrypt
私钥加密 openssl_private_encrypt => 公钥解密 openssl_public_decrypt
1. 公钥加密、私钥解密:
- 使用公钥加密数据:发送方使用接收方的公钥对数据进行加密。
- 使用私钥解密数据:只有拥有相应私钥的接收方才能使用私钥解密并获取原始数据。
2. 私钥加密、公钥解密:
- 使用私钥加密数据:发送方使用自己的私钥对数据进行加密。
- 使用公钥解密数据:接收方使用发送方的公钥来解密并获取原始数据。
<?php // 待加密的数据 $data = "hello, rsa!"; // 使用公钥加密数据 openssl_public_encrypt($data, $encryptedwithpublickey, $publickey); // 使用私钥解密数据 openssl_private_decrypt($encryptedwithpublickey, $decryptedwithprivatekey, $privatekey); // 使用私钥加密数据 openssl_private_encrypt($data, $encryptedwithprivatekey, $privatekey); // 使用公钥解密数据 openssl_public_decrypt($encryptedwithprivatekey, $decryptedwithpublickey, $publickey); // 输出结果 echo "原始数据: " . $data . "\n"; echo "公钥加密,私钥解密结果: " . $decryptedwithprivatekey . "\n"; echo "私钥加密,公钥解密结果: " . $decryptedwithpublickey . "\n"; ?>
第四步、rsa签名以及验证签名
/**
* 构造签名
* @param string $datastring 被签名数据
* @return string
*/
public function sign($datastring)
{
$signature = false;
openssl_sign($datastring, $signature, $privkey);
return base64_encode($signature);
}
/**
* 验证签名
* @param string $datastring 被签名数据
* @param string $signstring 已经签名的字符串
* @return number 1签名正确 0签名错误
*/
public function verify($datastring, $signstring)
{
$signature = base64_decode($signstring);
$flg = openssl_verify($datastring, $signature, $pubkey);
return $flg;
}第五步、封装完整代码
<?php
class rsa{
protected $publickey;
protected $privatekey;
//$type 1长类型 2完整key 3文件内完整key
public function __construct($publickey = '', $privatekey = '', $type=1){
$this->setkey($publickey, $privatekey, $type);
}
public function setkey($publickey = null, $privatekey = null, $type=1)
{
if (!is_null($publickey)) {
$this->setuppubkey($publickey, $type);
}
if (!is_null($privatekey)) {
$this->setupprivkey($privatekey, $type);
}
}
private function setupprivkey($privatekey, $type)
{
if (is_resource($this->privatekey)) {
return true;
}
if ($type == 1) {
$pem = chunk_split($privatekey, 64, "\n");
$pem = "-----begin private key-----\n" . $pem . "-----end private key-----\n";
$this->privatekey = openssl_pkey_get_private($pem);
} elseif ($type == 2) {
$this->privatekey = openssl_pkey_get_private($privatekey);
} elseif ($type == 3) {
$privatekeystring = file_get_contents($privatekey);
$this->privatekey= openssl_pkey_get_private($privatekeystring);
}
return true;
}
private function setuppubkey($publickey, $type=1)
{
if (is_resource($this->publickey)) {
return true;
}
if ($type == 1) {
$pem = chunk_split($publickey, 64, "\n");
$pem = "-----begin public key-----\n" . $pem . "-----end public key-----\n";
$this->publickey = openssl_pkey_get_public($pem);
} elseif ($type == 2) {
$this->publickey= openssl_pkey_get_public($publickey);
} elseif ($type == 3) {
$pubstring = file_get_contents($publickey);
$this->publickey= openssl_pkey_get_public($pubstring);
}
return true;
}
public function privencrypt($data)
{
if (!is_string($data) || empty($this->privatekey)) {
return null;
}
$r = openssl_private_encrypt($data, $encrypted, $this->privatekey);
if ($r === true) {
return base64_encode($encrypted);
}
return null;
}
public function privdecrypt($encrypted)
{
if (!is_string($encrypted) || empty($this->privatekey)) {
return null;
}
$encrypted = base64_decode($encrypted);
$r = openssl_private_decrypt($encrypted, $decrypted, $this->privatekey);
if ($r === true) {
return $decrypted;
}
return null;
}
public function pubencrypt($data)
{
if (!is_string($data) || empty($this->publickey)) {
return null;
}
$r = openssl_public_encrypt($data, $encrypted, $this->publickey);
if ($r === true) {
return base64_encode($encrypted);
}
return null;
}
public function pubdecrypt($crypted)
{
if (!is_string($crypted) || empty($this->publickey)) {
return null;
}
$crypted = base64_decode($crypted);
$r = openssl_public_decrypt($crypted, $decrypted, $this->publickey);
if ($r === true) {
return $decrypted;
}
return null;
}
/**
* 构造签名
* @param string $datastring 被签名数据
* @return string
*/
public function sign($datastring)
{
$signature = false;
openssl_sign($datastring, $signature, $this->privatekey);
return base64_encode($signature);
}
/**
* 验证签名
* @param string $datastring 被签名数据
* @param string $signstring 已经签名的字符串
* @return number 1签名正确 0签名错误
*/
public function verify($datastring, $signstring)
{
$signature = base64_decode($signstring);
$flg = openssl_verify($datastring, $signature, $this->publickey);
return $flg;
}
public function __destruct()
{
is_resource($this->privatekey) && @openssl_free_key($this->privatekey);
is_resource($this->publickey) && @openssl_free_key($this->publickey);
}
}
/*$publickey = 'mfwwdqyjkozihvcnaqebbqadswawsajbakz1mktymrogknhip1xay4aiyt5r0bscczndaoncrmfz4kbgripnhxealr5lfbnmkw7k6i+2dsfpsezootvqtpucaweaaq==';
$privatekey = 'miibvaibadanbgkqhkig9w0baqefaascat4wgge6ageaakeapnwyppkzggyqcei/xedlhqlk3mvqgxwjmcmcickswvniqeaui80ferouvmv8gcwrdutql7z2wu9irmiho+q09qidaqabakbunx3nghxyjppsfn++7iytd+i7+agfy/0xwyb3rpeigggfemjcrfaeq5sc2vunxsreoy5gbusqmfxh//cym18naiea1z1czx/q9cbijfpwp1a+k5cvfdxdcfbi/aqgakvs0/cciqdf+2fr23aobslcoc4s0yax94abgxcntyurqztxybsrcwigmw86zct87tx2oaq1xxk6vc68zqn6fbzee7wu1fa1pakcielmojp3qfac/aalj+diwlhlqwgjwl3674cu9bfui2bdaiea0ckjpf8x7kanccopeqc93psbiztuml322lofdv1lw/k=';
$rsa = new rsa($publickey, $privatekey, 1);*/
$publickeystring = "-----begin public key-----
miibijanbgkqhkig9w0baqefaaocaq8amiibcgkcaqeap1ffl+kueedbltzqrku+
8oq9izsuroxhmnwrxa1xmgtlbevchqnljujqwgulelyk7i78cgczwcyge2svj9oi
tbzgn02fwzncb3bhpv6oflitvqyczofaftwb+ttkuomopck/bgqve7hc6+74s/3x
q4tm1jvbnpysy11++dljeq8kaa3pnjwoftxer3gvegmfhi5xuttaba5zoianfsfr
0fgzvgbmrpqoior6mlsxxbmo4k2pmzb7yjyyr7zrc28doejcj5xnxkq4xpijzo8/
g79163dp0y9m7cdn4nfrddbsfehy6n+hkps6hsvf1z1ztqtlfk0mre/echubdcuh
+qidaqab
-----end public key-----";
$privatekeystring = "-----begin private key-----
miievqibadanbgkqhkig9w0baqefaascbkcwggsjageaaoibaqcnv98v6rqr50et
pncspt7yir0hljsujggadatdrvcwa2vt5uida2wo6oraa4sqvktulvxwzzpaliyt
zjwp2gi0hmaftz9zk0jvdsc+/qh+wjo+phxk4vovnyh61mq46aikkt9ubbv7sclr
7viz/ffdi0zwnvs09hjjxx74mumrdwpodek0ncgvperhczuscz+glnfrnnofrlk4
ho1+wwvr8bo8zuzgmqgiivoyvlfdsw7itakzmhtglhivvnelbwoh4kkpledesrhc
8gnojz+dv3xrd2ntl2btwofg19en0gwv4flqf6eqmzqfjv/xpvm1c2v+tszet8ry
g5sny4f5agmbaaecggead5rfiv/emxs4yvvzlei7og1s+ojqtmtdiefazuzyqufj
sf+w/lekkb1ts7ppxd+gficvct2otk1euu4mo7gxkniuyf3ba+tli3dqt0sanxum
fzhykoqsv4zt7wxtrfbm2xalxsmie7m0xx6ziur6qtv56ixgmp1dbuow8uklqlv2
p3vdckfjt2pwylqm2yzuoc3+ajfqpjus/dpyirgtld8rlofcrpgm2naewxycaeyi
cphgzyccabwyxzokfowifpm53zdbdzpupzkjs29rygjiz7st6sdceggoz+ayeuwa
bb1rkzjkbelrxbuizhlsbrbo12ye8gz+vpzgsy1cvqkbgqdwhjj/7yur/m+d9yj0
9s14tk5kx3ex2cl46it8fmjektk1ihgyb6dmk10pdrv2glj3zlfwyeu82p9zgswh
f34mu3o67medj3ojp+/qhyvem4wokw1973v8geqhqtvr7ypyvc/croyn49fkbkfc
sf7scw7eatobxtwmdjyaa+jdpwkbgqdie3dhyzx1yahehktygvw9oaddykzyzv2j
ko8rkaws0oxy6yi2j1ncrq3n5ro7pamcesrabgaps7n2gazlnfrtg/dch87m0kyz
aewo1dvi3xviajipmzxbeu2xp1o40ooxzxehp3vzuu2ydyr6yp3y2wcclmgf3vuz
o1ugk2a+xwkbgczzbpcaujldarvqwos4vr8ivi/a7dtdn/uxfxz8ovq2mhdlo5pt
hebr5cnuu0wz56dd2xzo71+nvxn69b9pmz0+vm/oyjcdmhdmq3xwcngpga/lkxqz
iqhf1c5zrsosutqpyiljhhainj4ipyqmohd+2omjbvypg2a4d5nnlk1paogbaixh
ognc3heqzgvh0f+ml82edbd5dosa1es7klj7j2ekht7lvqj9q2imhkaqkzqarpsj
26fvt4iq36qzxltyc8fxllrjlfcuhuxi5ane53jgw33zpjg2nndyoeyavzqr8l2u
obkiehnhpjc5xryr1vvbvevbgciwvbodfa7nckrpaogak2oiq5slu5ofab4qcn6v
vherc8jxgzwl/o2z/4t0ox1x6nwddal87lcyq6ab3dqmgemtjdd2z9ddn2m9opto
yunvlxynicqgsnyucwy6q1yy1fovhiujf8rkq4utseq8gsrf8hf3ajhmzha1r5b7
y5mupuhis6ckwmtf+paxagq=
-----end private key-----";
//$rsa = new rsa($publickeystring, $privatekeystring, 2);
$rsa = new rsa("public.pem", "private.pem", 3);
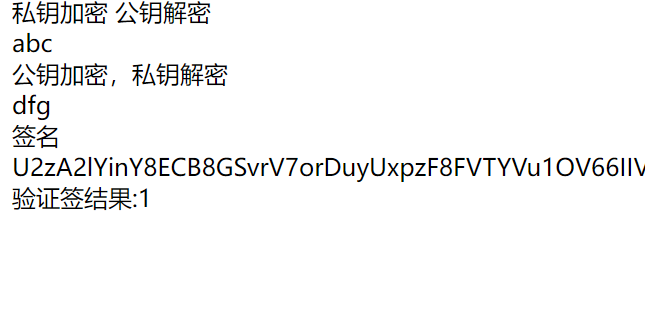
echo "私钥加密 公钥解密";
echo "<br/>";
$s = $rsa->privencrypt("abc");
echo $rsa->pubdecrypt($s);
echo "<br/>";
echo "公钥加密,私钥解密";
echo "<br/>";
$d = $rsa->pubencrypt("dfg");
echo $rsa->privdecrypt($d);
echo "<br/>";
echo "签名";
echo "<br/>";
$str="a=1&b=2";
$sign=$rsa->sign($str);
echo $sign;
$res6=$rsa->verify($str,$sign);
echo "<br/>";
echo "验证签结果:".$res6;
以上就是php三种方式读取rsa密钥加解密、签名验签完整教程的详细内容,更多关于php rsa密钥的资料请关注代码网其它相关文章!






发表评论