论坛里面有人询问如何使用powershell脚本查询文件修改的审计日志,豆子服务器没开这个功能,不过尝试写了个类似的脚本可以查询日志,并输出对应的xml内容。
基本方法是get-winevent, 可以指定对应的eventid,获取列表。如果想获取这个事件具体的内容,需要根据不同事件的xml内容进行变化。
比如
$events = get-winevent -computername syddc01 -filterhashtable @{logname='security';id=4771} -maxevents 1
$eventxml = [xml]$event.toxml()
$eventxml.event.event.data
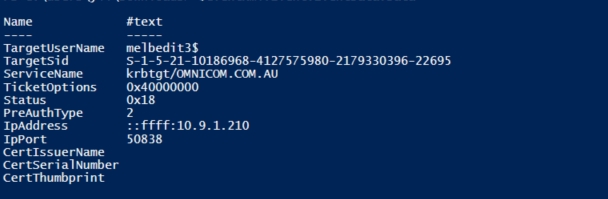
根据这个思路,我如果想获取最新的20个4771的事件日志,并输出结果
$events = get-winevent -computername syddc01 -filterhashtable @{logname='security';id=4771} -maxevents 20
# parse out the event message data
foreach ($event in $events) {
# convert the event to xml
$eventxml = [xml]$event.toxml()
# iterate through each one of the xml message properties
for ($i=0; $i -lt $eventxml.event.eventdata.data.count; $i++) {
# append these as object properties
add-member -inputobject $event -membertype noteproperty -force -name $eventxml.event.eventdata.data[$i].name -value $eventxml.event.eventdata.data[$i].'#text'
}
}
$events | select message, targetusername, ipaddress,timecreated | out-gridview
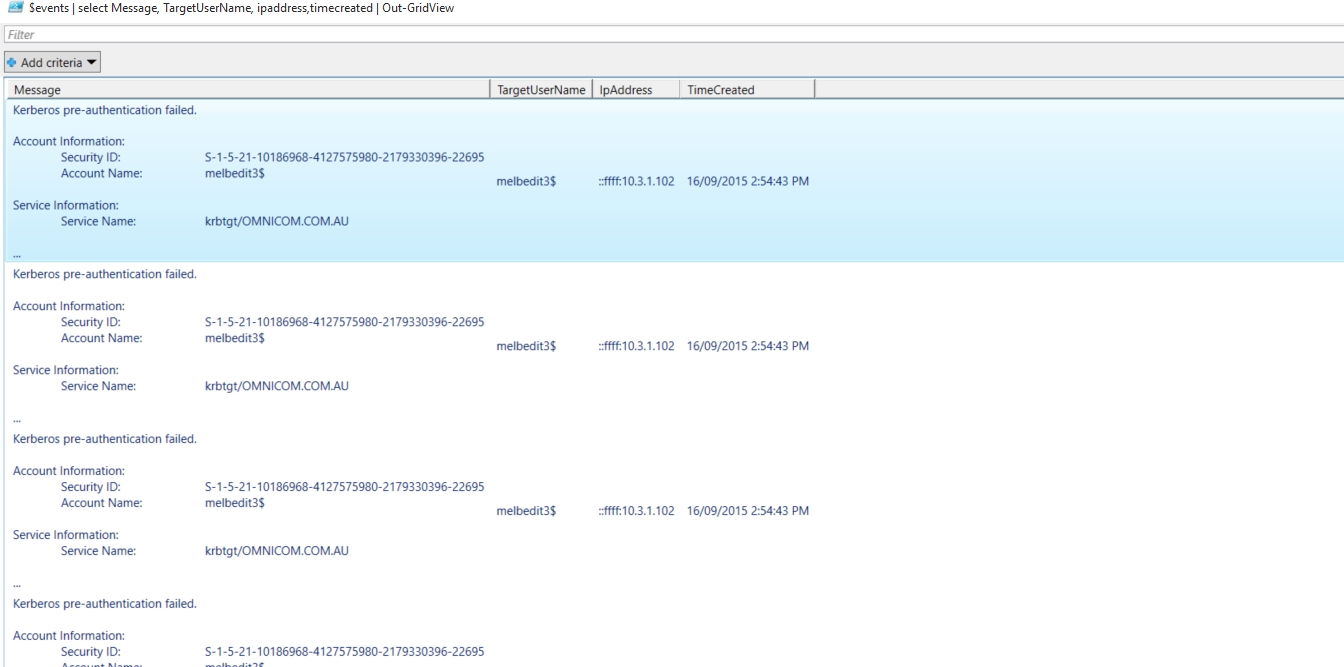
有的时候,事件的数目很多,我希望对这个时间进行一个限制。千万别用 where-object 的方式来过滤,不然等到地老天荒也未必出结果。
我们需要通过哈希表来过滤
$endtime=get-date
$starttime=$endtime.addminutes(-1)
$eventcritea = @{logname='security';id=4740;starttime=$starttime;endtime=$endtime}
另外一种常见的方式是通过xmlfilter来过滤日志
首先,我们可以通过event viewer来自定义一个xpath
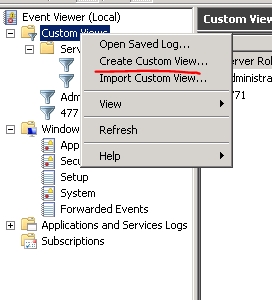
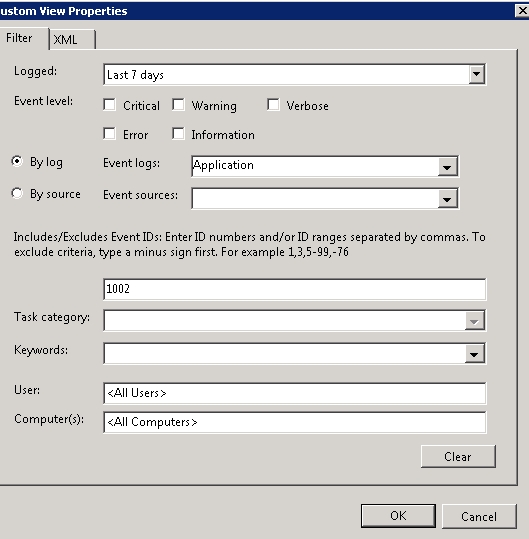
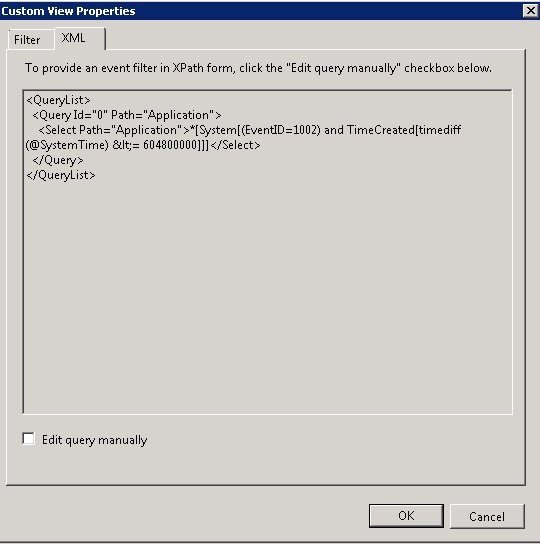
因为是不同的事件,他的eventdata结果是不一样的,因此我做了些变动。
[xml]$xmlfilter = @"
<querylist>
<query id="0" path="application">
<select path="application">*[system[(eventid=1002) and timecreated[timediff(@systemtime) <= 604800000]]]</select>
</query>
</querylist>
“@
#get-winevent -computername $dc.dc -logname security -filterxpath "*[system[(eventid=529 or eventid=644 or eventid=675 or eventid=676 or eventid=681 or eventid=4625) and timecreated[timediff(@systemtime) <= 86400000]]]" #-maxevents 50
$events = get-winevent -computername syddc01 -filterxml $xmlfilter
foreach ($event in $events) {
# convert the event to xml
$eventxml = [xml]$event.toxml()
# iterate through each one of the xml message properties
for ($i=0; $i -lt $eventxml.event.eventdata.data.count; $i++) {
# append these as object properties
add-member -inputobject $event -membertype noteproperty -force -name "app" -value $eventxml.event.eventdata.data[5]
}
}
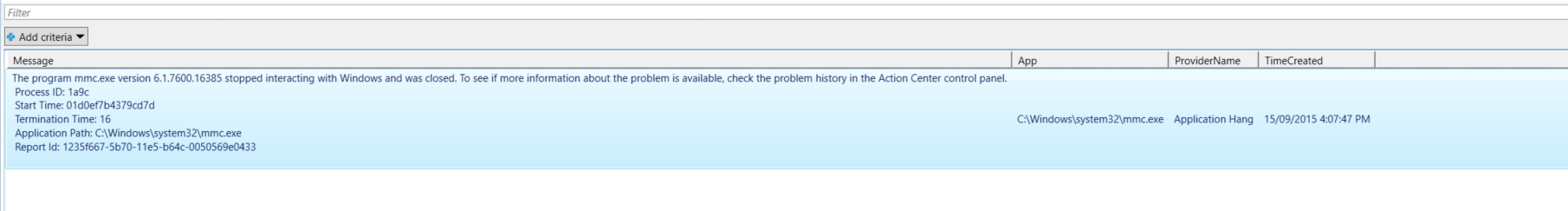
$events | select message, app, providername, timecreated | out-gridview
结果如下
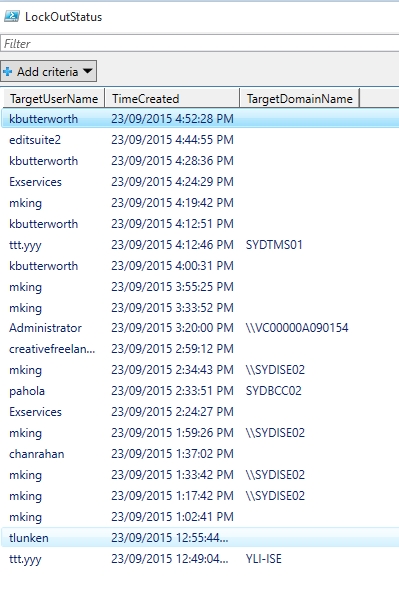
最后再给一个例子,我希望获取lockout用户的信息以及他们是在哪里被锁住的,这个日志我们查看4771或者4740。4771的日志过多,查询太慢,所以这里我已4740为例。
eventcritea = @{logname='security';id=4740}
$events =get-winevent -computername (get-addomain).pdcemulator -filterhashtable $eventcritea
#$events = get-winevent -computername syddc01 -filterxml $xmlfilter
# parse out the event message data
foreach ($event in $events) {
# convert the event to xml
$eventxml = [xml]$event.toxml()
# iterate through each one of the xml message properties
for ($i=0; $i -lt $eventxml.event.eventdata.data.count; $i++) {
# append these as object properties
add-member -inputobject $event -membertype noteproperty -force -name $eventxml.event.eventdata.data[$i].name -value $eventxml.event.eventdata.data[$i].'#text'
}
}
$events | select targetusername,timecreated, targetdomainname | out-gridview -title lockoutstatus
break;
search-adaccount -lockedout | foreach-object {unlock-adaccount -identity $_.distinguishedname }
本文出自 “麻婆豆腐” 博客





发表评论